Overnight on Thursday January 13th, a number of Ukrainian government websites were defaced. Below we have outlined the technical indicators of the event.
Whilst we have previously posted on the Destructive WhisperGate attack targeting Ukrainian organisations that become public just after the website defacements, we have avoided commenting on the defacements themselves, as:
1) It wasn’t clear if the activities were linked, and
2) We did not want to help spread the disinformation the defacements intended to provoke.
However, now that the two events have been confirmed by the Ukrainian Government as likely linked, and with the Polish CERT responding to the disinformation levelled against Poland, we feel it is a good time to record some of the technical indicators so they are not lost.
Website Defacement Contents
A number of Ukranian Governments were temporarily defaced, before promptly being taken down and mostly restored. The contents of one of these compromised sites, minagro.gov[.]ua - The Ministry of Agriculture, is recorded in the UrlScan service at January 14th 2022, 6:04:22 am UTC.
The contents that the attackers have put up is extremely simple, and consists of just a directly embedded image encoded in Base64:
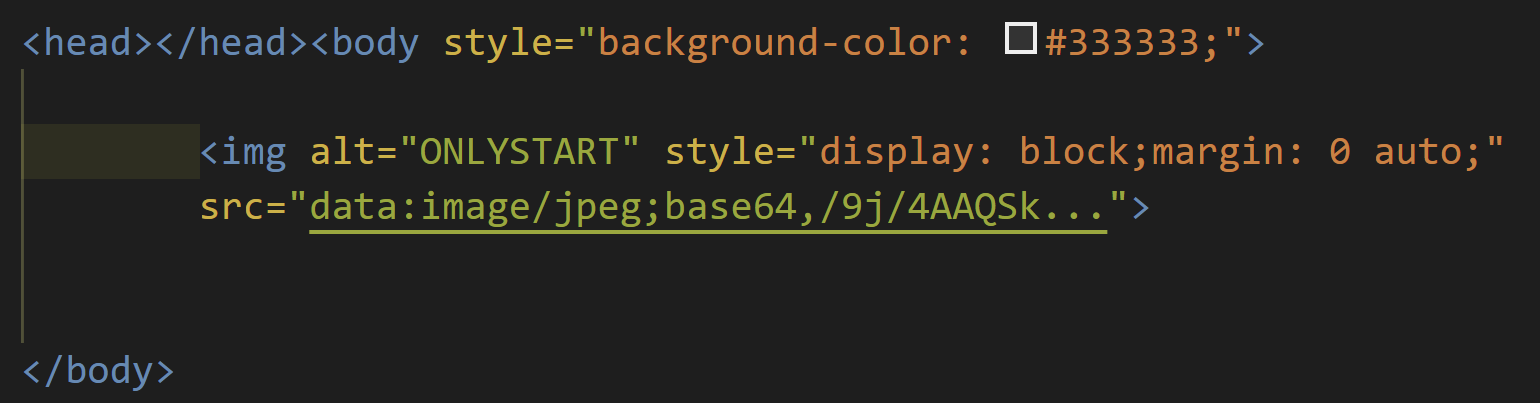
The image itself has been well discussed, and contains text that is likely an attempt at the Polish language via Google Translate as well as some potentially offensive images. We’ve redacted the images in the screenshot below:
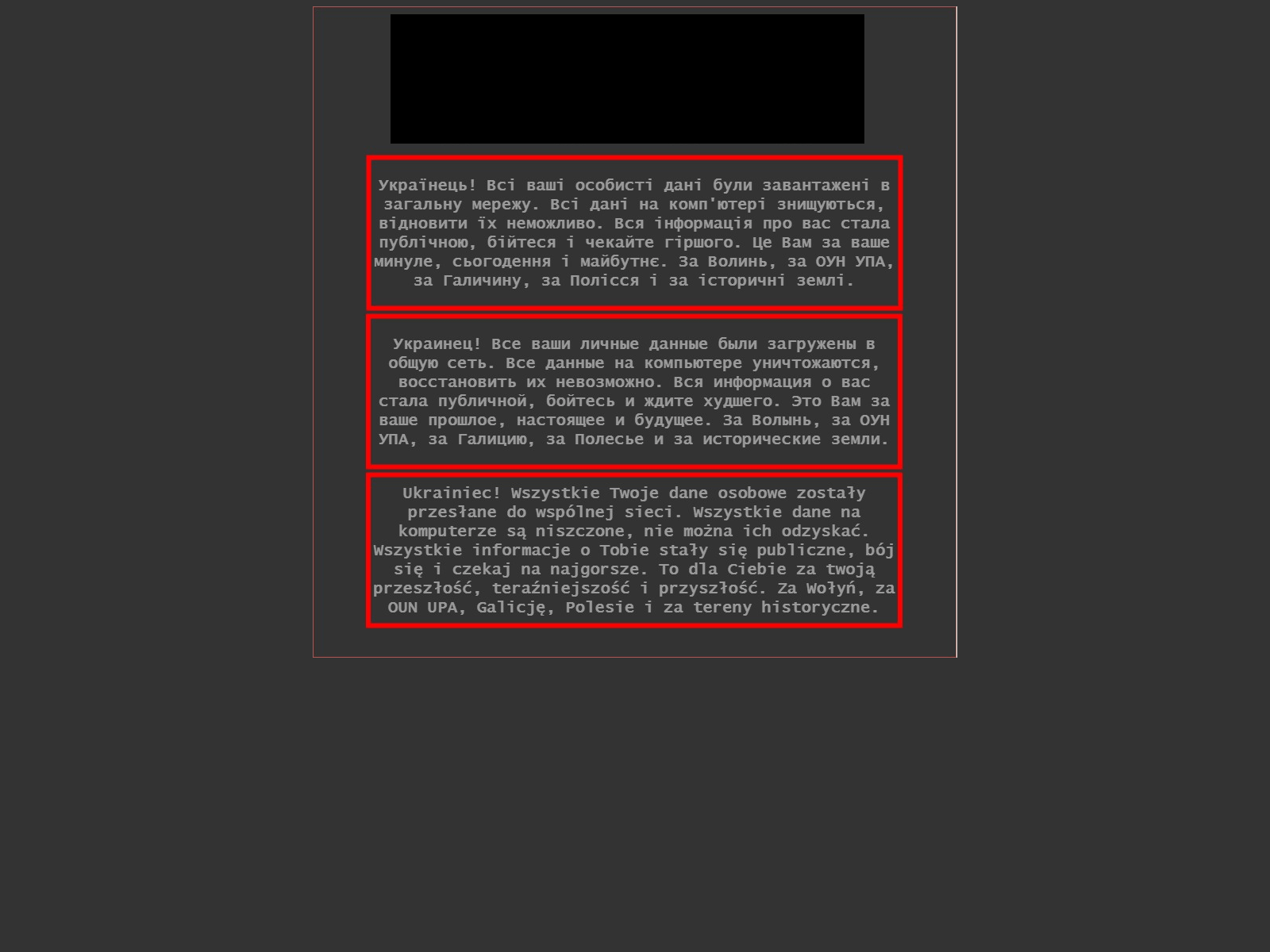
We can further analyse the image itself. The image has the SHA256 Hash 077DB0788055DCCF6983EBE513DCAD420182C22B956387D024835A3662D90962.
It was uploaded to Virustotal at 2022-01-14 08:12:35 UTC from a user in Ukraine with the filename “Без названия.jpeg” (Untitled). It is likely someone who either visited a compromised website or was investigating the attack uploaded it shortly after the attack.
Image files can have “Exif” meta-data recorded within them. This can include information such as the model of Camera a photo was taken with, or if GPS enabled the location of the Camera when the photo was taken. Extremely unusually, this Image contains GPS coordinates (52.208630, 21.009427) - even though it is a generated image and not a photo. This means that someone decided to manually add GPS Coordinates to the image after creating it.
As the Polish CSIRT team points out in their analysis, this was likely a false-flag attempt:
“Particularly noteworthy is the fact that the attacker prepared the metadata in the graphic file used for the defacement. The location under the given coordinates indicates the area of the Warsaw School of Economics. The CSIRT MON suspects that the real intention of the adversary was to use the geolocation of the General Staff of the Polish Army to lead potential analysts and the public to a false, controversial trail.”
(This quotation was automatically translated via Google Translate.)
Exploitation with CVE-2021-32648
In their immediate response to the defacements, CERT-UA stated that the compromised sites were attacked using CVE-2021-32648 to compromise servers running the October Content Management System. The vulnerability was disclosed last year and allows an attacker to reset the administrative credentials:
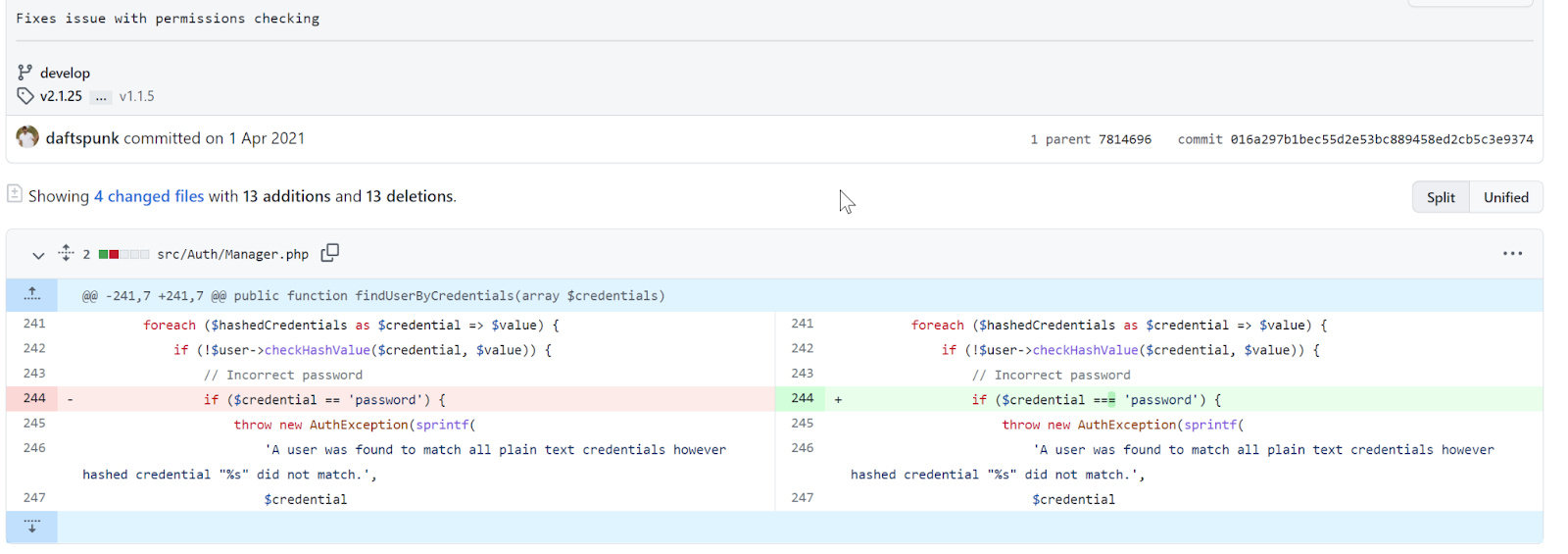
If you are running October CMS you should review logs for any suspicious access to the URLs:
- /backend/backend/auth/restore
- /backend/backend/auth/reset/1
KitSoft
It has been reported that there may be elements of a supply chain attack too. Many of the compromised sites were operated by a Ukrainian company called Kitsoft. In an interview with Kim Zetter, Kitsoft said they were also impacted by the WhiserGate wiper following compromise - likely in an attempt to delay them restoring the original contents of websites.
Records from the internet archive indicate Kitsoft’s website www.kitsoft.kiev[.]ua stopped responding after the 13th January - and it is currently set to redirect to their Facebook page instead:
Kitsoft posted today (19th January) that they have successfully restored databases for vehicle insurance and other services. Those that have responded to destructive cyber-attacks before will know how hard the staff at Kitsoft must have been working over the weekend and into the week to restore the service for their clients.
What’s next?
Unfortunately, Ukraine has seen a large number of destructive cyber attacks over the years. One silver lining is that they are now extremely well prepared for them. CERT-UA in particular has a strong reputation for responding to incidents. In an interview with The Record Serhii Demediuk, the Deputy Secretary of Ukraine’s National Security and Defense Council, indicates what the government thinks may come next:
“... the informational narratives that accompanied this attack indicate that this was a red herring to cover up for more destructive actions, which, in my opinion, we will feel in the near future. And, with high probability, this may be in the energy sector. Since the vulnerabilities used for the attack on January 14 are also present in some energy enterprises, however, they were not hit. At the same time, the active scanning and testing of the network infrastructure of energy enterprises that day were unprecedented. And there are also many other indicators that have been recorded as evidence of this threat.”
Indicators of Compromise
077DB0788055DCCF6983EBE513DCAD420182C22B956387D024835A3662D90962 (Image found on compromised servers)
About Cado Security
We have built the first platform to enabled and automate Incident Response in Cloud (Aws, Azure) and Container environments (Docker, Kubernetes). You can deploy a Free Trial of straight from our website.
Further Reading and References:

