
Resources for DFIR Professionals Responding to the REvil Ransomware Kaseya Supply Chain Attack
Yesterday Sophos and Huntress Labs identified that Kaseya, a remote management provider popular with MSPs, was compromised to deploy a supply chain ransomware attack. A large number of organisations were impacted, including temporarily shutting 800 stores at the CoOp supermarket chain in Sweden.
We have provided a number of resources on our Github that may help Digital Forensics and Incident Response experts responding to these attacks over the weekend:
- Full DD Disk capture from an infected system
- Malware Samples
- Decompiled Malware Samples (via retdec)
- PCAP of network traffic capture from an infected system
- Indicators of Compromise and Yara Rules
- Configuration and Ransomware Note
We've also included a quick forensic triage of an infected system below with Cado Response (you can grab a demo here!).
Scope
This is not the first time a REVil operator has managed to compromise large sets of MSPs, as shown in sinkhole data from KPN:
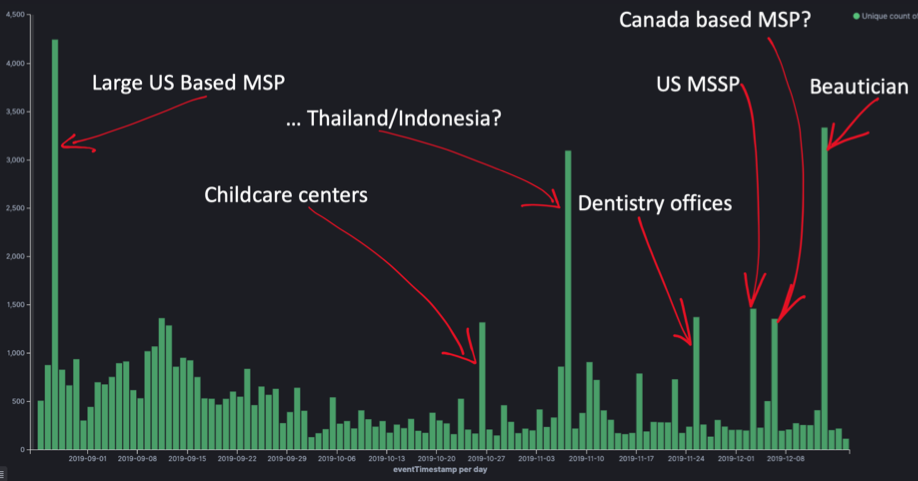
However this time the scope is particularly bad as Kaseya provides software/access to a number of MSPs - who in turn supply services/access to potentially thousands of businesses.
We have sinkholed some of the available domains from the REvil configuration and are seeing a relatively small number of infected machines connect in (see below). It is likely the peak of this particular attack has passed and the connections include both sandbox machines and other campaigns:
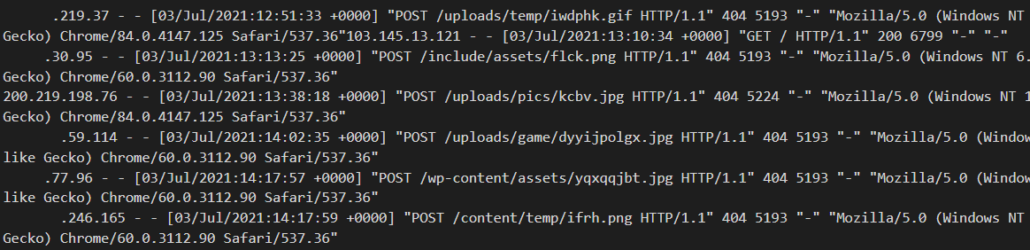
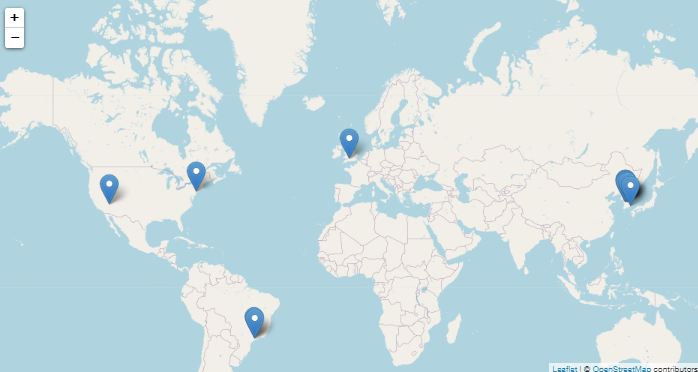
Indicators of Compromise
With thanks to Sophos for the most complete listing:
C:\Program Files (x86)\Kaseya\...\AgentMon.exe
(Legitimate Kaseya binary used for remote execution)
C:\windows\cert.exe
36a71c6ac77db619e18f701be47d79306459ff1550b0c92da47b8c46e2ec0752
(Not on VirusTotal)
C:\kworking\agent.crt
45AEBD60E3C4ED8D3285907F5BF6C71B3B60A9BCB7C34E246C20410CF678FC0C
C:\kworking\agent.exe
MD5 561cffbaba71a6e8cc1cdceda990ead4
SHA-1 5162f14d75e96edb914d1756349d6e11583db0b0
SHA-256 d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
(Primary malicious REvil Binary, drops legit \msmpeng.exe and malicious side-loaded dll mpsvc.dll below)
C:\windows\msmpeng.exe
MD5 8cc83221870dd07144e63df594c391d9
SHA-1 3d409b39b8502fcd23335a878f2cbdaf6d721995
SHA-256 33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7a
(Non-Malicious MS Defender Binary used for side loading)
C:\Windows\mpsvc.dll
MD5 a47cf00aedf769d60d58bfe00c0b5421
SHA-1 656c4d285ea518d90c1b669b79af475db31e30b1
SHA-256 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
(Side-loaded DLL)
And additional indicators of the likely first stages of the attacks from Huntress Labs and TrueSec:
Access from 18[.]223.199.234 and 161.35.239[.]148 to:
- /dl.asp
- /cgi-bin/KUpload.dll
- /userFilterTableRpt.asp
Creation on the VSA server of:
/Kaseya/WebPages/ManagedFiles/VSATicketFiles/Screenshot.jpg
/Kaseya/webpages/managedfiles/vsaticketfiles/agent.crt
/Kaseya/webpages/managedfiles/vsaticketfiles/agent.exe
Additional indicators are available:
REVil Configuration File
References and Other Reporting
- https://doublepulsar.com/kaseya-supply-chain-attack-delivers-mass-ransomware-event-to-us-companies-76e4ec6ec64b
- https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689
- https://www.bleepingcomputer.com/news/security/revil-ransomware-hits-200-companies-in-msp-supply-chain-attack/
Malware Analysis
Sandbox reports
- https://app.any.run/tasks/e76868a5-c717-4c32-a418-04b0d0dc29c5/
- https://www.virustotal.com/gui/file/d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e/community
- https://analyze.intezer.com/files/d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e?vt
- https://www.joesandbox.com/analysis/443736/0/html#deviceScreen
- https://www.vmray.com/analyses/d55f983c994c/report/behavior_grouped.html
- https://tria.ge/210703-97x2n2g7ps
Forensic Triage Analysis
We infected a system with a copy of the REvil malware and performed an automated forensic capture and analysis with Cado Response. You can download a full disk image of the system from our GitHub repository.
There are a number of clear markers for forensic analysts to look for on infected systems below.
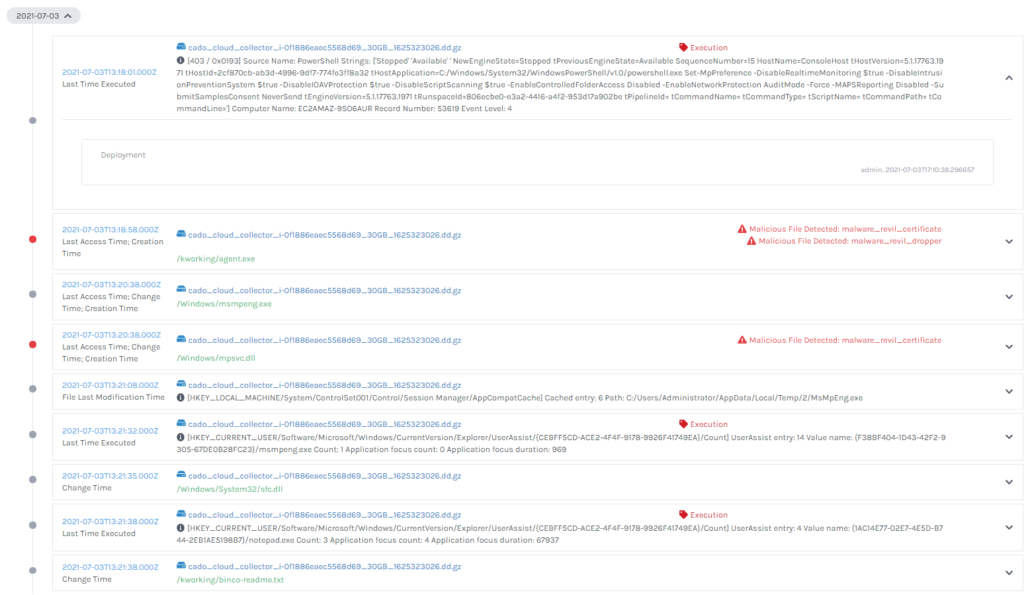
The ransomware is well detected by anti-virus and you will likely find both logs of anti-virus detections (below) and the malware itself detected by Yara rules (also below) during analysis:
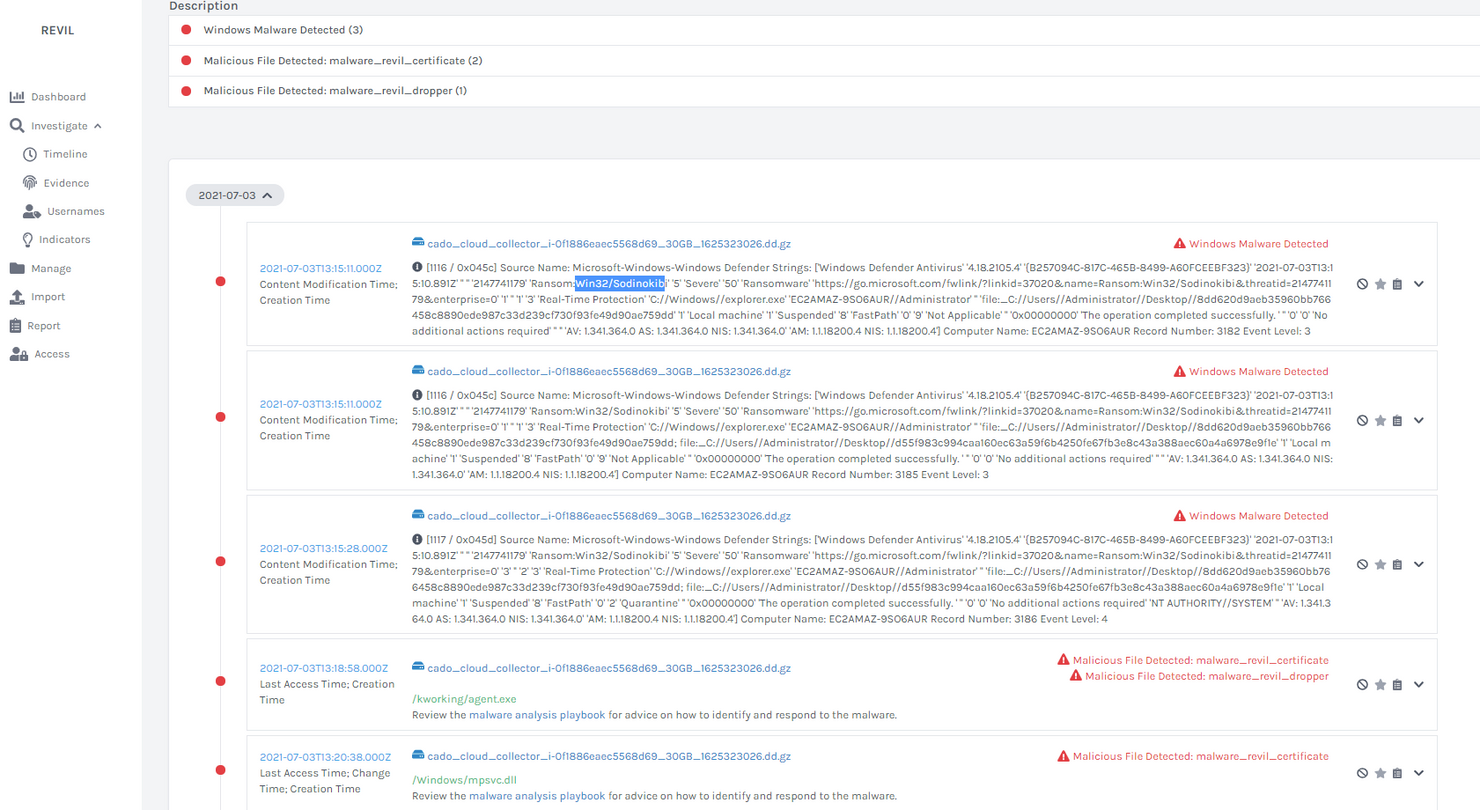
However - Kaseya recommends certain folder paths be excluded from detection. Not coincidentally, this includes the folder that REvil is executed from (c:\kworking) - so anti-virus detections may be missing.
The primary malicious binary clearly contains the known-bad certificate:
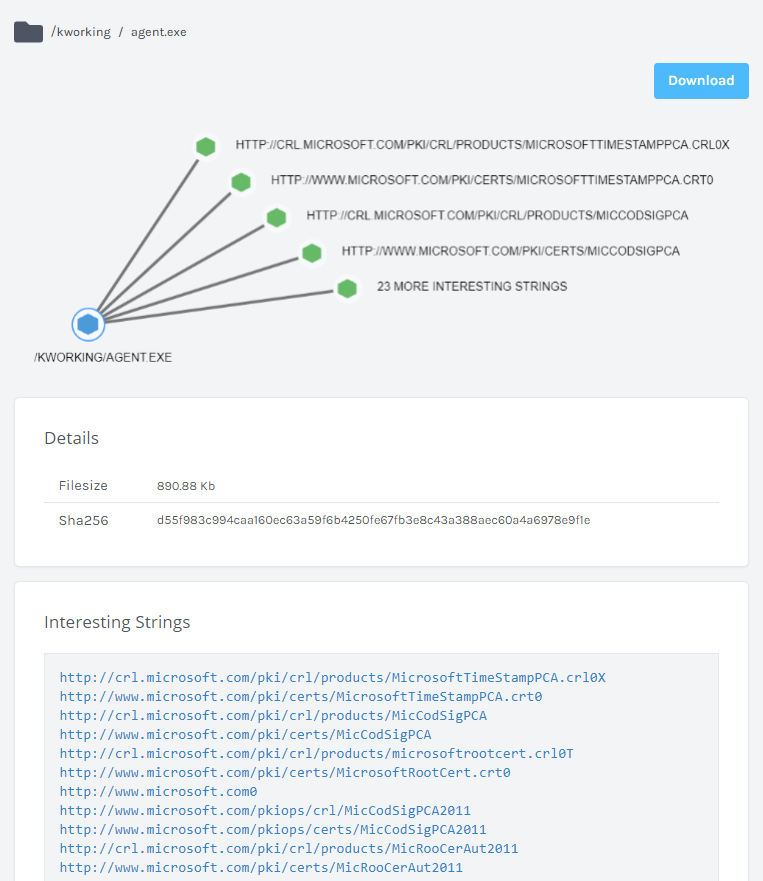
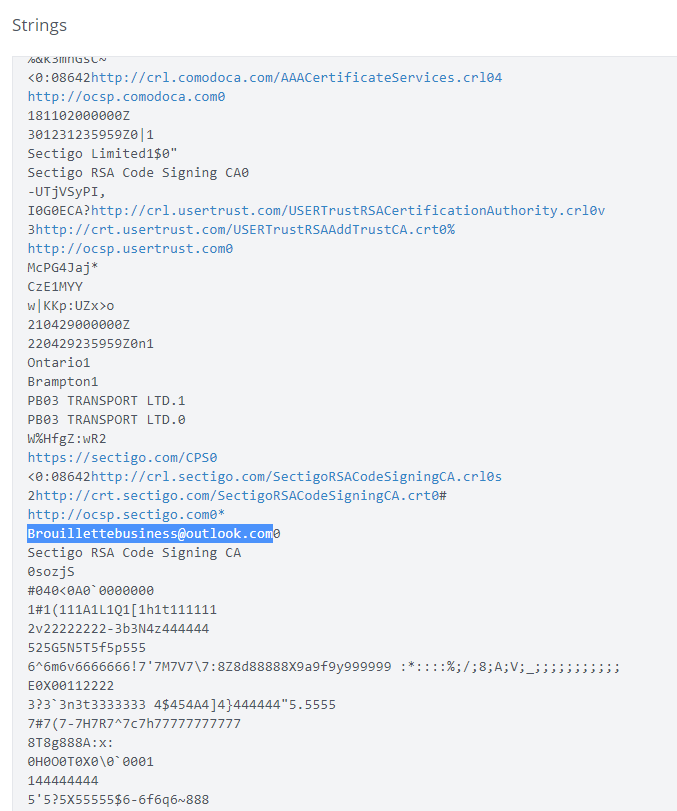
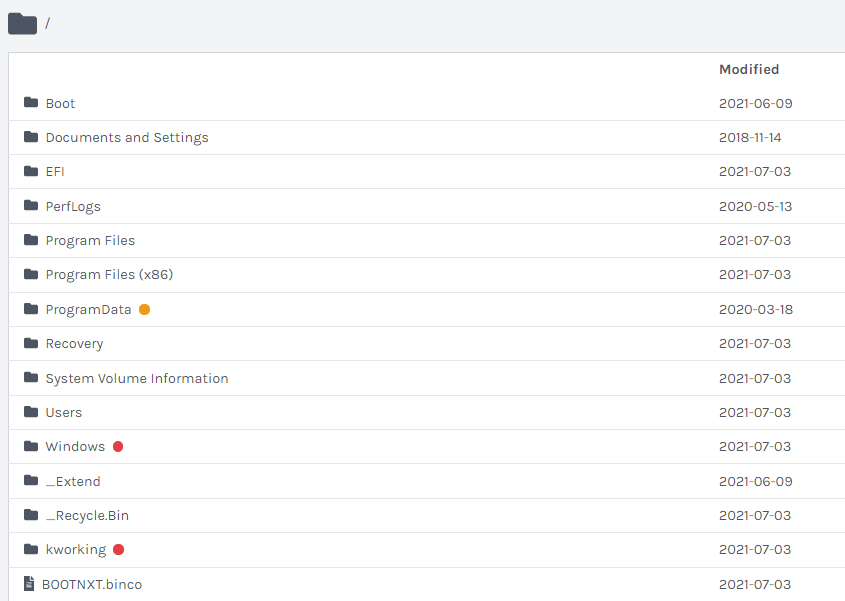
And as expected the malicious files are dropped in the Windows and Kworking directories:
And outside of the malware itself, we can see the PowerShell commands used to deploy the malware:
If you would like to test out Cado Response yourself you can grab a demo here.
