This morning I saw news that a Supercomputer based at the University of Edinburgh called “Archer”, currently performing analysis for Coronavirus research, had been taken offline due to a cyber-attack.
Below I’ve provided some additional details on a spate of recent, likely linked, attacks.

Technical Indicators Shared
A number of technical reports were shared yesterday (Friday 15th May 2020):
- A report by the European Grid Infrastructure (EGI) security team reported on two distinct attacks (“Incident One” and “Incident Two” ) that their members observed against super-computers.
- Security researcher Tillmann Werner shared a Yara rule to detect a loader and log cleaner for attacks against supercomputers.
- Security researcher Markus Neis shared hashes for the loaders and log cleaners
The details shared by the EGI in “Incident Two”, Tillman and Markus are all clearly related. They refer to a file called “fonts” used as a loader, and a file called “low” used to clean logs and hide traces of the attacks.
Incident Two, and Attacks in the UK
EGI reports that the attackers were stealing credentials, and logging in from three compromised networks:
- The University of Krakow, Poland
- Shanghai Jiaotong University, China
- China Science and Technology Network, China
Reportedly it is common for users at different High Performance Computing (HPC) facilities to have logins for other institutions – making it easy for attackers to compromise a number of facilities.
Whilst the EGI report was posted yesterday, there were in fact reports of attacks against Supercomputers in the UK by posted earlier on Wednesday by a user on Slashdot:
“I work in HPC in the UK. Yesterday I had to revoke all the SSH certificates on our system because unfortunately some f’ing idiot users have been using private keys without passcodes. These have been used to hop from system to system as many HPC users have accounts on different systems. They are managing local privilege escalation on some systems and then looking for more unsecured SSH keys to jump to other systems. They maybe using one or more methods for the privilege escalation, possibly CVE-2019-15666. Right now the UK national facility ARCHER is off line as they have suffered a root exploit.
The actors are coming from the following IP addresses, 202.120.32.231 and 159.226.161.107, you get zero guesses which country these are from.”
The IP addresses are the same listed by EGI later on Friday, at Shanghai Jiaotong University and China Science and Technology Network.
The user posted on a report titled “US Warns That Chinese Hackers Are Targeting Virus Research” – though it should be noted that EGI reported finding mining malware on servers. If true, it is more likely these are criminal financially motivated attacks than the espionage attacks against research centers that the FBI has warned about this week.
Malware Analysis
The “Loader” and “Cleaner” malware samples were uploaded to VirusTotal from users in the following locations, indicating possible victim geographies:
- Germany
- United Kingdom
- Spain
- Switzerland
Tillman reported that the malware is compiled on victims machines – which explains why we only see a single sample of each piece of malware uploaded to VirusTotal. Normally when investigating cryptojacking attacks against servers you will see the same piece of malware uploaded from a number of victims.
We have identified possible additional victims in the United States (see “Incident Two” below).
Whilst I have been writing this report, Robert Helling has just published an analysis of the loader and cleaner – so I will add some brief additional details below. Robert is a physicist who reports the Leibniz Supercomputing Center in Germanywhere he works was impacted, so he decided to investigate further. For those familiar with The Cuckoos Egg – this is a familiar story!
The Loader is as a very simple program to just call bash, and has setuid set so any command will run as root.
The Cleaner is quite subtle, and removes traces of the attacker from a number of log files. One sample (552245645cc49087dfbc827d069fa678626b946f4b71cb35fa4a49becd971363) decompiles cleanly to show the core functions:
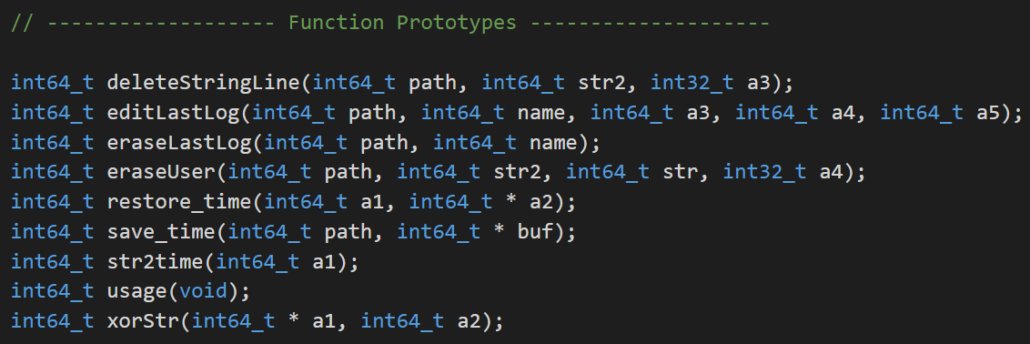
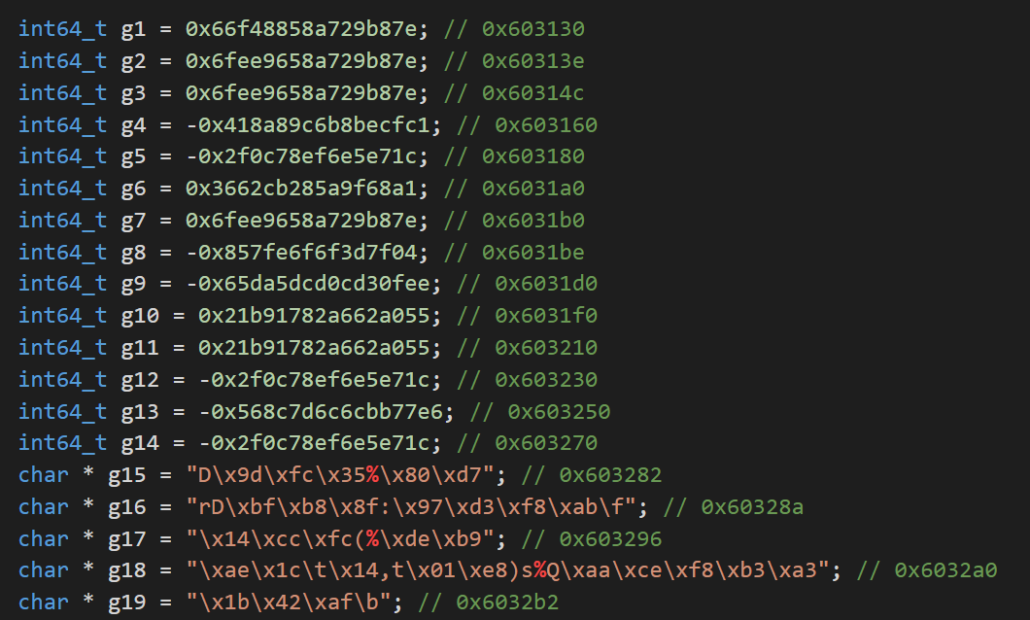
And a number of XOR-encoded strings:
“Incident One” in the EGI Report
So far I have just been talking about Incident Two (and other closely linked attacks) from the EGI report. Incident One appears to be linked by EGI, as both Incident One and Incident Two reported logins from andromeda.up.krakow[.]pl – a compromised host at the University of Krakow. They also likely occurred in a similar timeframe.
There is also an additional link. EGI reports that in Incident One the compromised machines talk to a crypto-currency pool server at 91.196.70[.]109. The server is still online, and is not a “public pool” – it is likely operated by the attackers.
The pool server has a self-signed certificate on it. There are 8 other servers on the internet that seem to have the same certificate at some-point, indicating they had some shared configuration.
- The first server is 91.196.70[.]109 – the server mentioned in Incident Two
- Another server is 159.226.234[.]29 – the server at China Science and Technology Network linked to attacks in both Incident One and Incident Two
- We found an additional server that belongs to a super-computer cluster operated by a well-known University in the United States. We are reaching out to them as they may also be compromised.
We will update this report if we find additional details.
We are busy building a cloud-native forensics and response platform for responding to security incidents.
Be the first to get updates or beta-test our platform by signing up here:
Indicators of Compromise
Please see the EGI report for a list of suspect filenames.
Indicators are available in OTX and below.
Loader
MD5 fe9a46254cf233fcafeada013d0ec056
SHA-1 72690c644f7c7970b9ce9c2c9b9da31463ea0916
SHA-256 0f8a1c0f706d8e70f3240abd788a193426302322916cf4e9358d05116f6231ec
MD5 5ed00cb88d218db8d09352d9058c400c
SHA-1 bb926f5fb4554fe0397bdfbe5cc6115419d6c408
SHA-256 0efdd382872f0ff0866e5f68f0c66c01fcf4f9836a78ddaa5bbb349f20353897
MD5 02570c3a85fc1ccea9858ecacdc3a954
SHA-1 05cb49439377ea1de61808098eb0d1e3c88854ab
SHA-256 9647038806905ce7a46e1b783746c623c1c03fcc60a6bd18564bda5625ac4780
MD5 11a186cd20d74f5dc0febe3d7904c52d
SHA-1 dac49da1b718235621028343a7f3f9b5b227828c
SHA-256 820ff5da47023d6a92d37497094a51aca81b0b149715436b57fe117d94ec3fe0
MD5 dd771b769ceeba0fc1d514a6e6530a70
SHA-1 f9bfce6adb6541a08f62e69636d0e90f6f663852
SHA-256 94b17888b735fa75bb6939b542446c22e1108a46cecdffce4f8b579d8a877c3a
MD5 bf16df15225bc83a56b0cf0ec9012360
SHA-1 1f130e158765b9d5c87571212d48bab86dd30e49
SHA-256 807d836d496d0ac61dbec07b757579985d65ec6187b35155de7d342f760d6b79
Cleaner
MD5 780f236fb3646534832b2da9d5cf6eb0
SHA-1 05baffad9ad7225e8043e79677d0a50e586e683b
SHA-256 552245645cc49087dfbc827d069fa678626b946f4b71cb35fa4a49becd971363
MD5 c764ba53fa9c5a24a88a1d2e17be6943
SHA-1 e6bd973fc2bb7efd7b1c588acc31d74da4c1428c
SHA-256 4551fb76aa8806bc3d4f8622f5a1535887742aea99cdd227de300699425978b2
MD5 ce7240b8bbb2bee8f300321eef46a41e
SHA-1 e19c37bf7bb64dbc16a143614972d05f437c203c
SHA-256 74d21900332836e8509a5484413a525239b135f99af70f804d67136082ca6e9c
MD5 d42553bd420e80ec31df5da2d5b932e0
SHA-1 3a9fe697cf78d95351d95d61618866aa6490300a
SHA-256 eec6129780d3e1645ce19efd96c1e18aa08778c8472189f1d65bc46d449cfc82
MD5 65dde869c0e1455de24aadf5aa4538a2
SHA-1 0b2178adaf4fa70c4919835a3df96e521b8c94f7
SHA-256 e8627037ff667021e11da5f6e707d173f86edc6bb789c204f25ff5c4ccd21910
MD5 a0ec7d355dc9e7f232fb47bf401c3138
SHA-1 efb59da51029a294bbba9fe011a0f4aed8aec097
SHA-256 bd887ab361470f775e4834a99a1f21d20c6b4a5d13e75455e15bd1041407a33f
MD5 261f16ec5d72078f6e3c21551ceaecb2
SHA-1 5d2c21ad38deac2135cc0e3801265b33ec6e7b0b
SHA-256 c5e3b0ae057ad47ba91b3ccc32cd03cb5f64d26552b0ba1cb971f6a33ef12afb
MD5 0b522e54bf3f276496793c44bec7362b
SHA-1 08bca1448e43861a5173f4c6e111728f36c78d43
SHA-256 1d95d3b2f265aa142c8d2aca45c50a23265f5153650d2447e8c58cadbbb92deb
Anti-Virus detections
-
ESET: Linux/Agent.IT
-
Kaspersky: Linux.Loerbas.gen
-
APT_LNX_Academic_Camp_May20_Loader_1
Yara Rules (by Tillerman)
rule loader {
string: $ = { 61 31 C2 8B 45 FC 48 98 }
condition:
all of them
}
rule cleaner {
strings:
$ = { 14 CC FC 28 25 DE B9 }
condition:
all of them
}

