Attacks Surge in Cloud Environments
Cloud Detection & Response (CDR) focuses on continuous monitoring, threat detection, and incident response capabilities across cloud infrastructure - but, traditional security tools aren't effective in cloud environments, and are often designed for on-premises deployments. These traditional tools are often slow and ineffective at detecting and responding to cloud threats. Cloud environments are highly complex and dynamic, often involving thousands of virtual machines, containers, and other services, making it difficult to secure them with traditional tools.
Cloud Threats Require Cloud Solutions
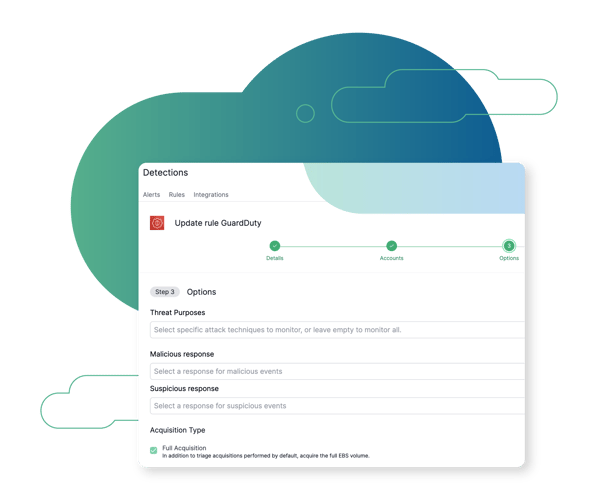
Cloud Native Integration
Through integration with cloud native detection technologies, as soon as a malicious activity is detected, the Cado Platform delivers critical forensic-level context.
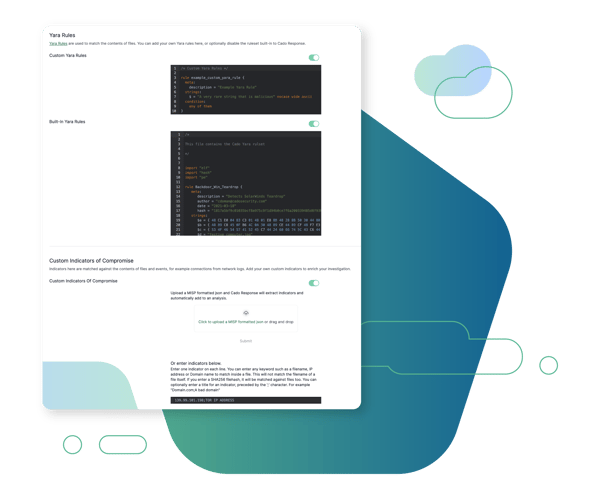
Threat Intelligence Integration
In addition to Cado Security's built in threat intelligence to provide visibility of the latest attacker tools and TTPs, users can import their own threat intelligence to the platform to enrich their investigations.
Browse Other Use Cases
Explore other ways security teams are using the Cado platform to advance their mission.
Cross Cloud Investigations
Investigate incidents identified in AWS, Azure, and GCP in a single pane of glass.
Container & K8s Investigations
Perform container investigations in environments including EKS, AKS, GKE, and Kubernetes.
SOC Triage
Automate triage acquisition of endpoint resources to gain immediate event insights and facilitate quick escalation.
SaaS Investigations
Analyze SaaS logs alongside other critical sources to investigate compromises such as Business Email Compromise (BEC).
Evidence Preservation
Ensure evidence residing in ephemeral environments is immediately captured and preserved before it disappears.

The Cado Advantage
Cado Security is helping organizations implement containment strategies for incident response around the world.








