
Your Customers Need Answers Fast
Organizations struggle with their ability to adequately manage risk in complex environments. Managed Security Service Providers (MSSPs) help address this need, but also require the latest technology to provide the best level of support possible. Further, with more attacks targeting cloud, container, and serverless resources, MSSPs need tools that provide insights into these environments, and quickly.
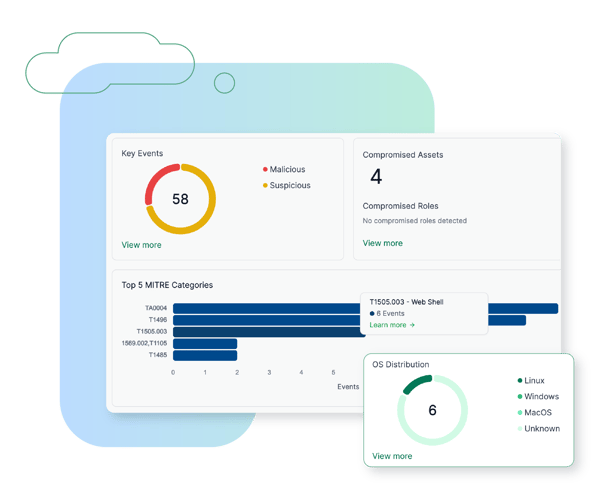
Embracing the Future
Cado Security enables MSSPs to leverage cutting-edge investigation and response capabilities. With Cado, MSSPs can provide swift triage for their clients and deliver new service offerings, such as investigations in container environments. The Cado platform quickly deploys in AWS, GovCloud, Azure, or GCP and provides cross-cloud support.


Hear from our Customer and MSSP, Agorà Security

“We use Cado Security for many investigations. Cado not only speeds up the process of acquisition and analysis, but it helps us by having more information to dig through and go deeper into the investigation.”
Matteo Brunati, CEO
Agorà Security
Top Cado Use Cases
See how MSSPs are using the Cado platform to provide faster incident response for their clients.
Cross Cloud Investigations
Respond to incidents identified in AWS, Azure, and GCP in a single pane of glass.
Container & K8s Investigations
Perform container investigations in environments including EKS, AKS, GKE, and Kubernetes.
SOC Triage
Automate triage acquisition of endpoint resources to gain immediate event insights and facilitate quick escalation.
SaaS Investigations
Analyze SaaS logs alongside other critical sources to investigate compromises such as Business Email Compromise (BEC).
Cloud Detection & Response (CDR)
Marry threat detection with forensic context to expedite response.
Evidence Preservation
Ensure evidence residing in ephemeral environments is immediately captured and preserved before it disappears.







