As you’ve seen there have been a number of reports (Crowdstrike, SentinelOne, Trend Micro, Symantec, Volexity, Huntress) of a supply chain compromise of 3CX, which produces VOIP phone software.
Below we have performed a quick triage forensic investigation of a system we have installed the backdoored installer on. We have also supplied Yara rules for the components under a friendly Apache License (at the bottom) to help you hunt for compromised systems.
Note that our data-set will be missing data you will find on a real compromised system, as the download chain (from Github) is now broken due to a successful taken down request. We deployed the final stage credential theft tool (d3dcompiler_47.dll) manually via rundll32 calling each available exported module. There is also a sleep function to delay the secondary payload. So results may vary a bit from what you will find on a real system!
We have performed the analysis of the system using Cado Response but the results and approach should be transferable.
Installing 3CX
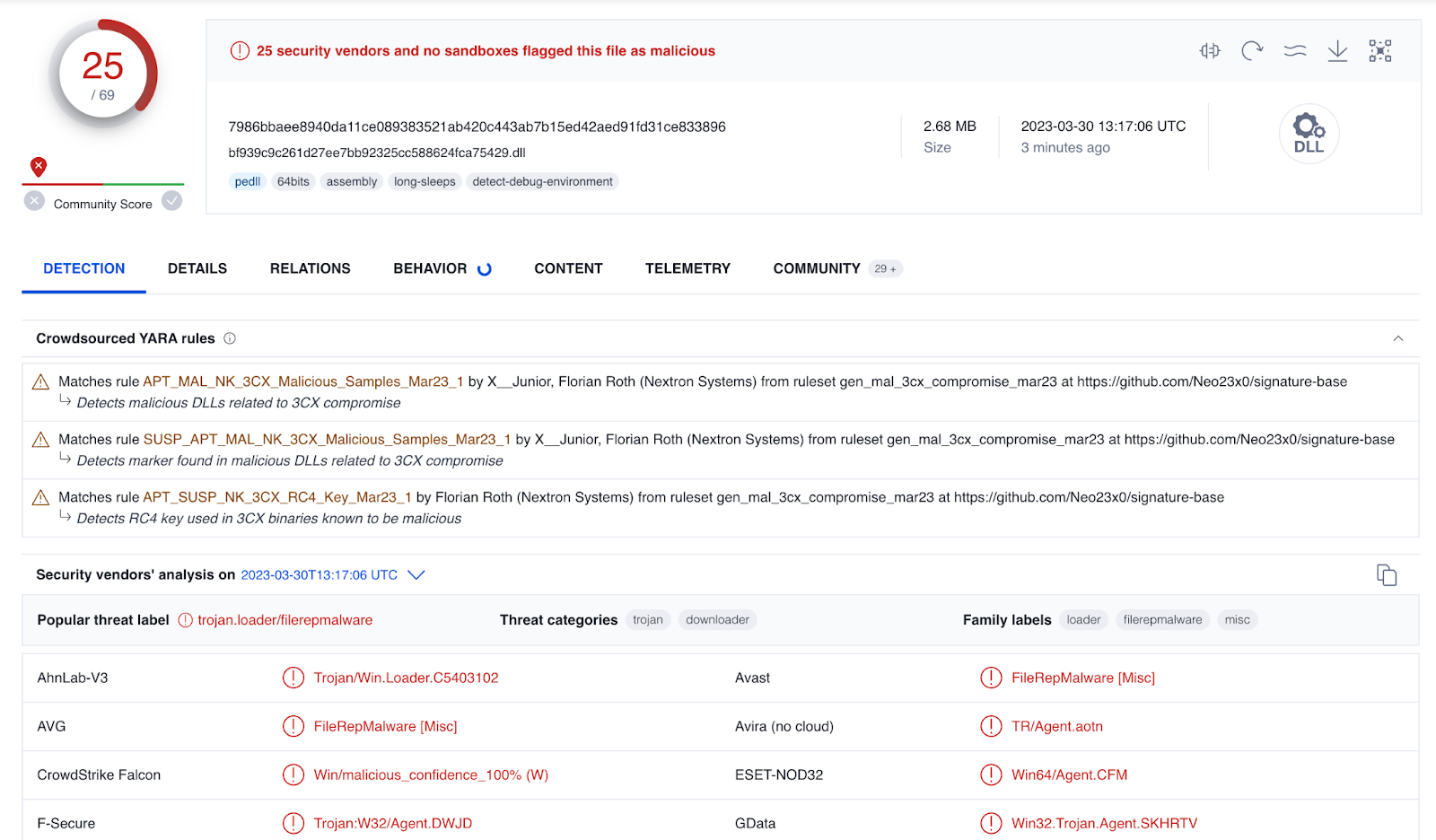
We installed a known-compromised version of 3CX (3CXDesktopApp-18.12.416.msi). After the installation completed successfully, Windows defender detected a malicious component (ffmpeg.dll) as Win64/SamScissors:
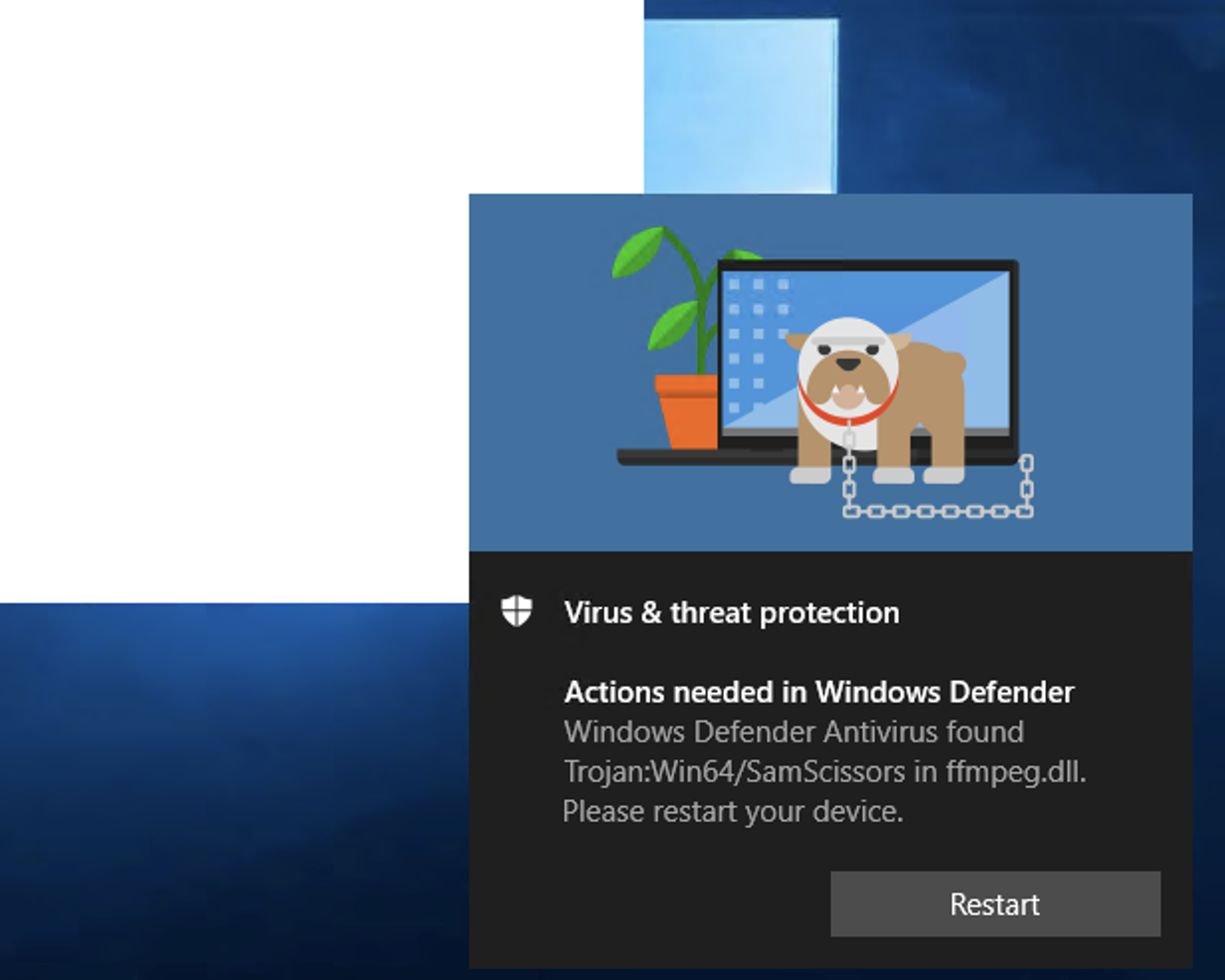
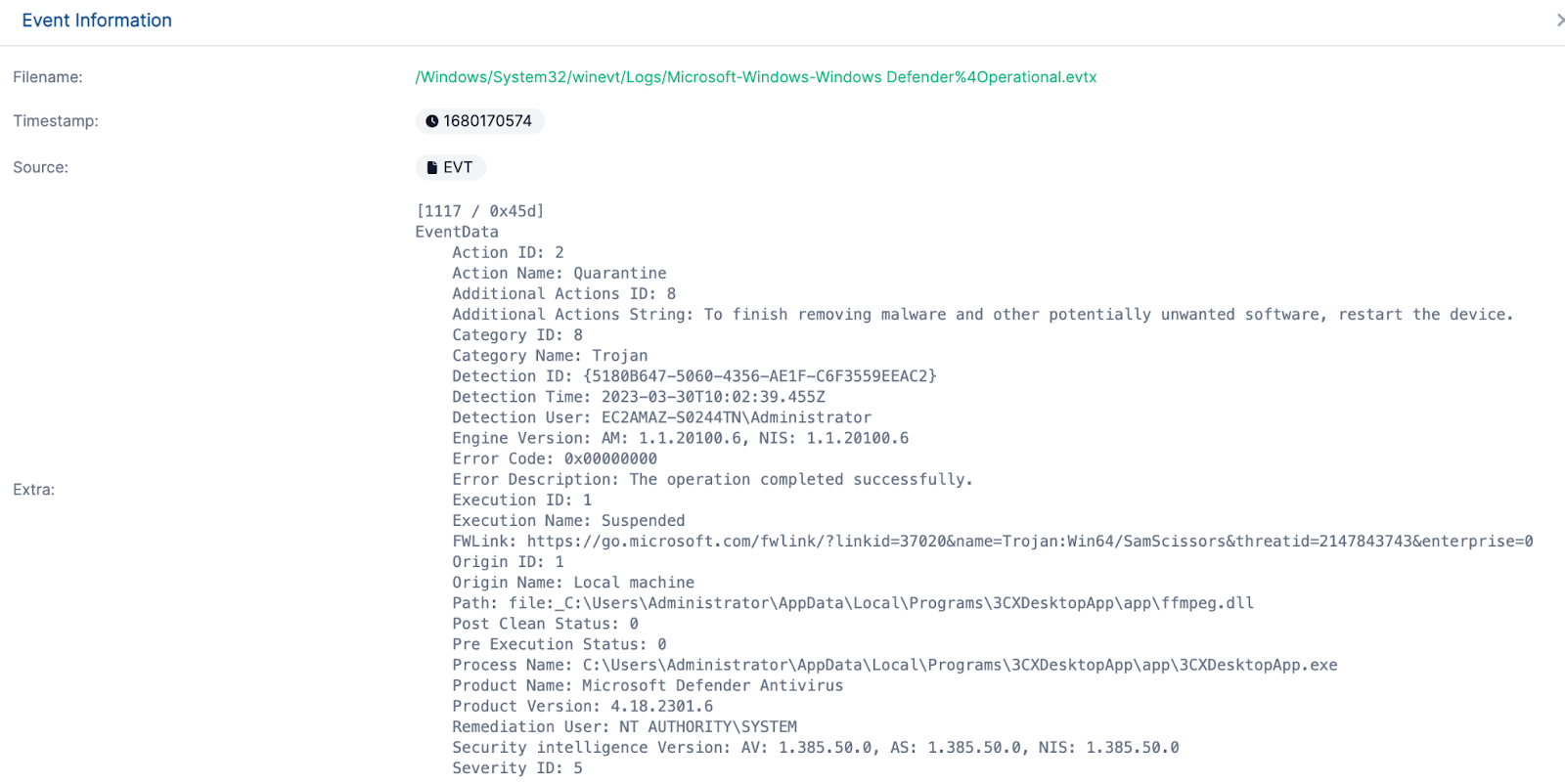
Which you can see in the Windows Defender event logs as expected:
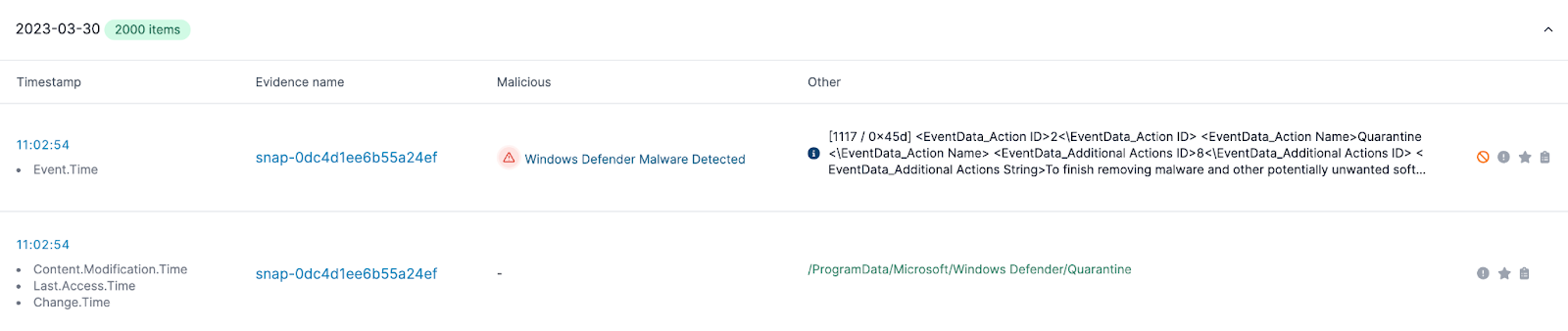
Looking down in the timeline, we see a suspicious file being created on disk (dcwfzkme.sys)
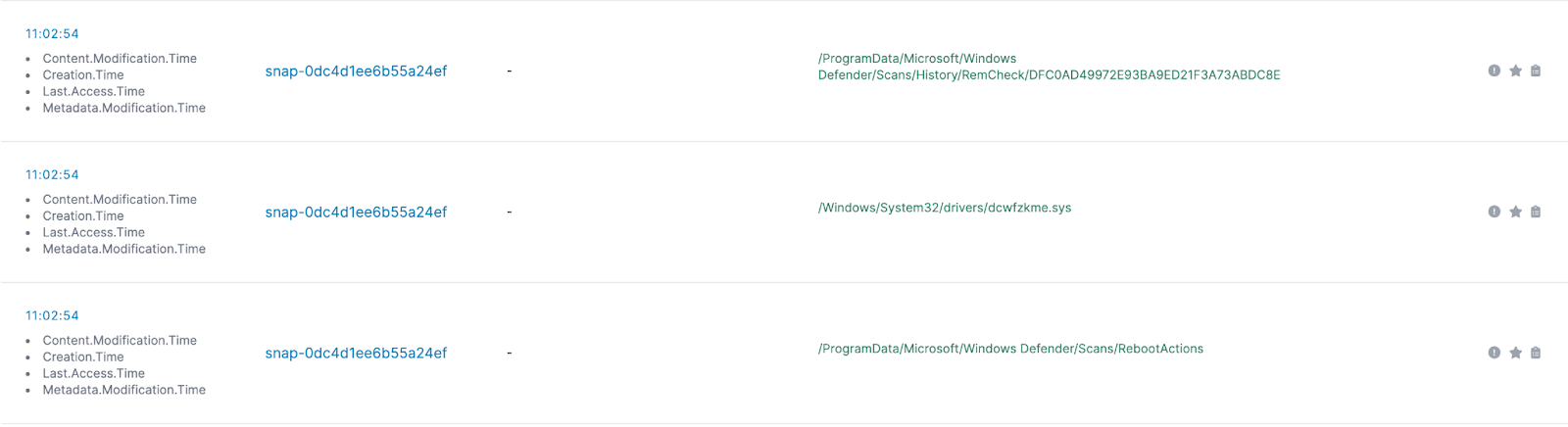
Which we can see on disk:
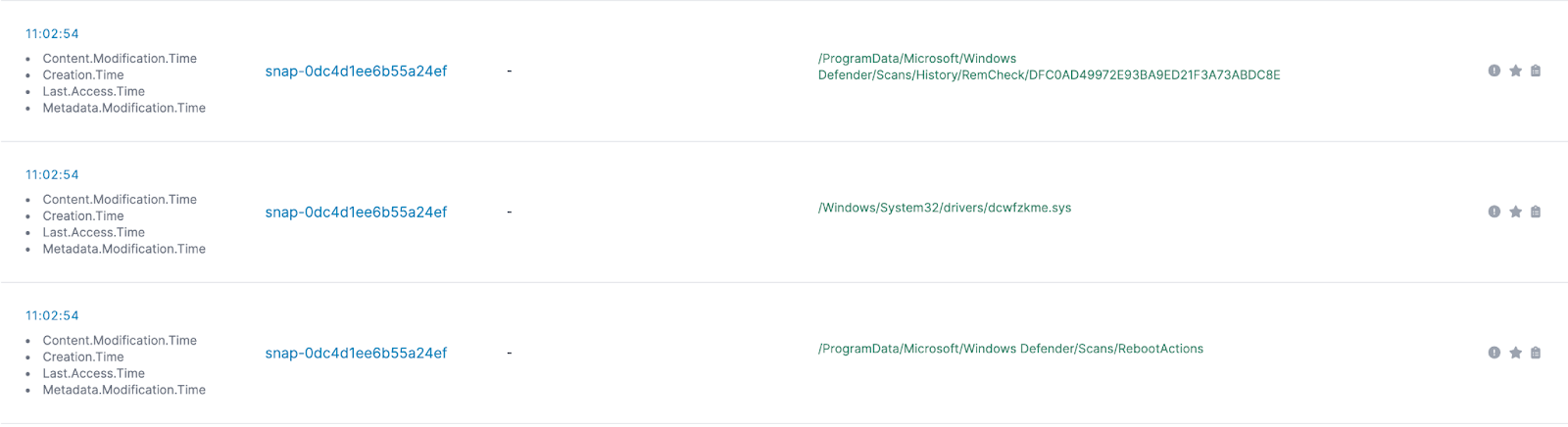
However, looking up the hash shows that this is actually a part of Windows Defender’s legitimate execution - this is just part of how Microsoft’s Boot Time Removal Tool (btr.sys) operates and is a random name. So - let’s ignore that one!
So - let's disable Defender and reinstall…
Post Installation
One obvious thing is ffmpeg.dll as discussed and identified already, now viewable on disk:
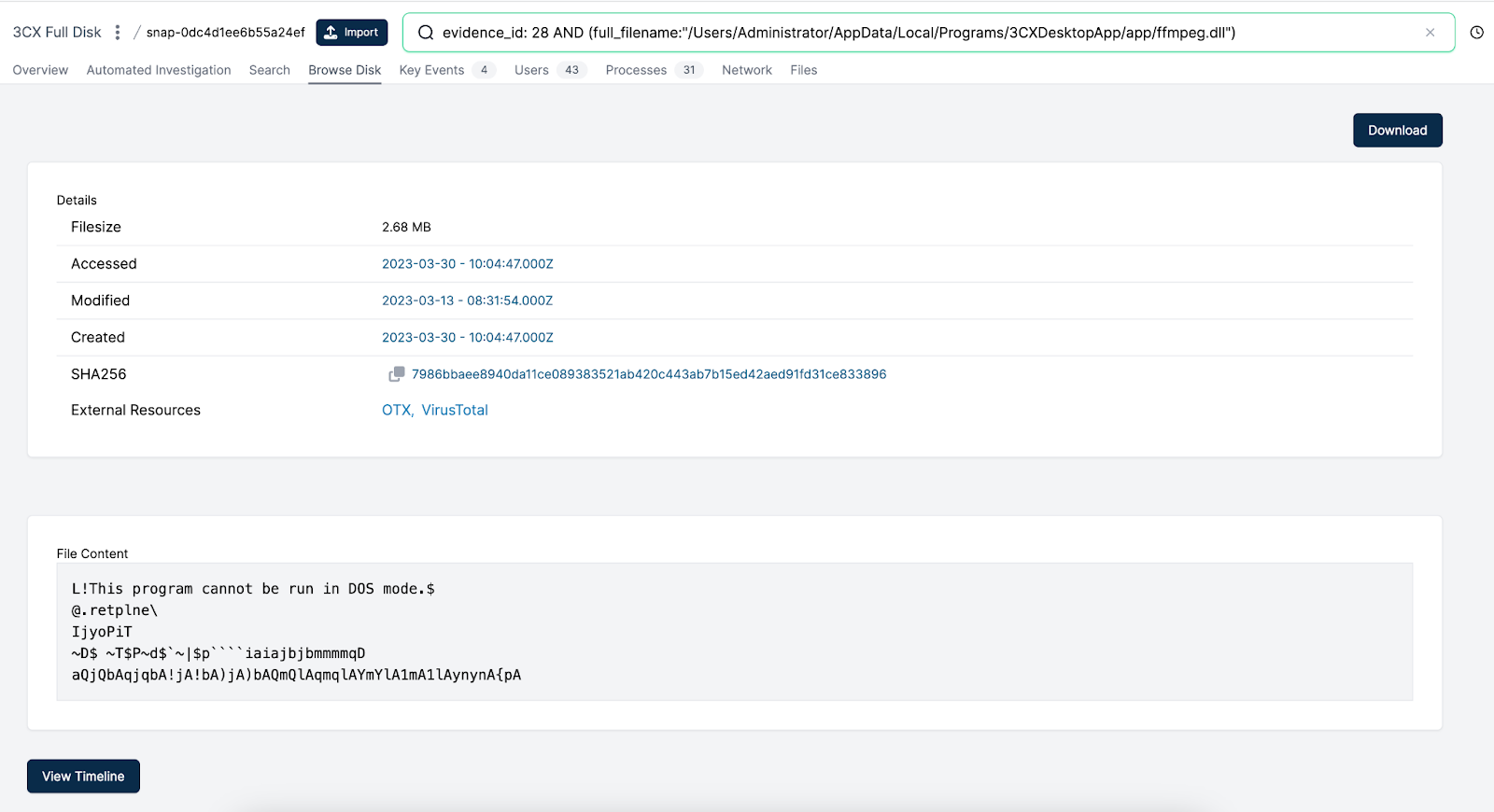
Browsing to the folder level of ffmpeg.dll, we see a few other key files:
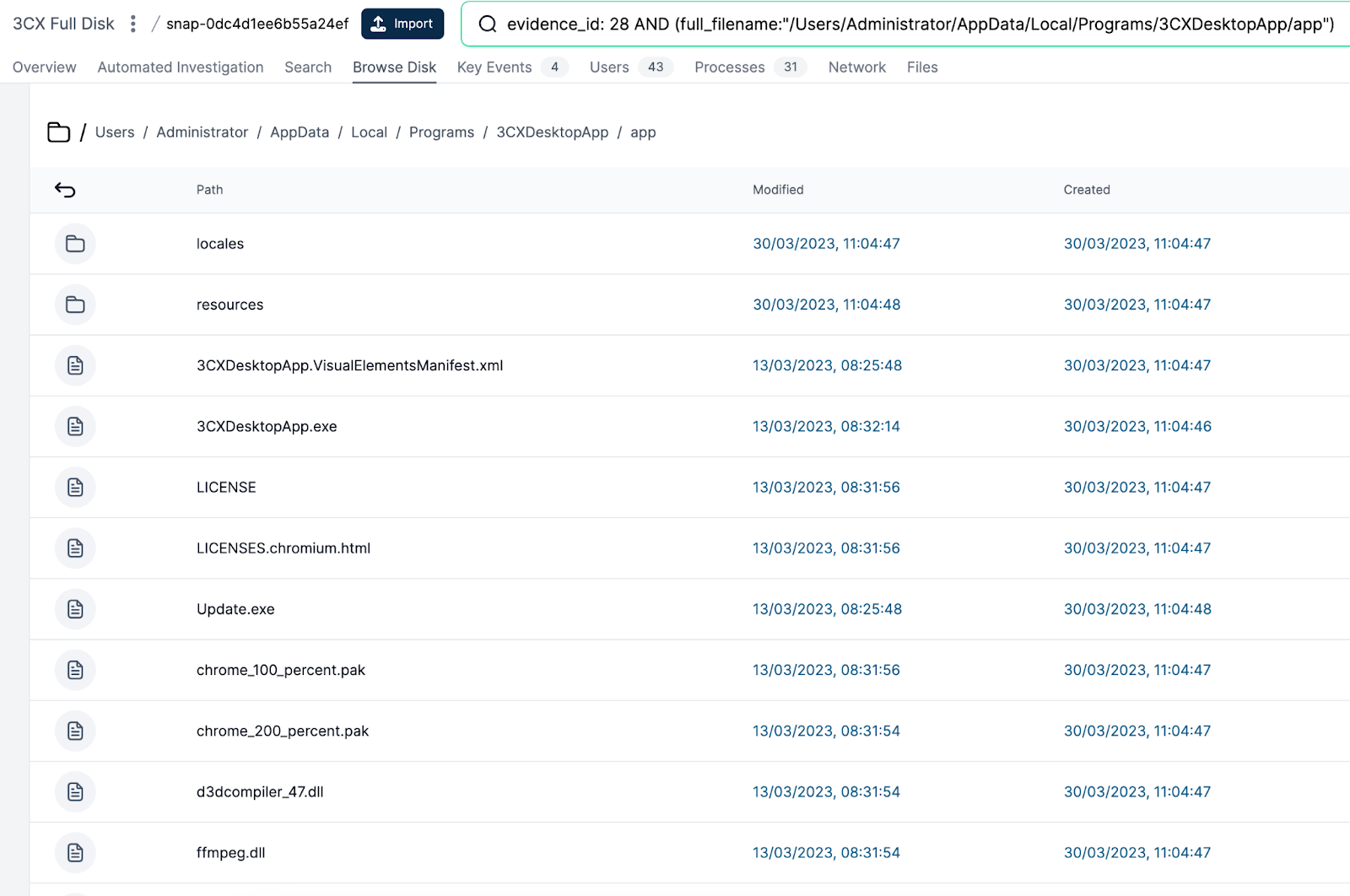
Ffmpeg.dll we have spoken about and is used to side-load encoded data from the other file in the folder - d3dcompiler_47.dll.
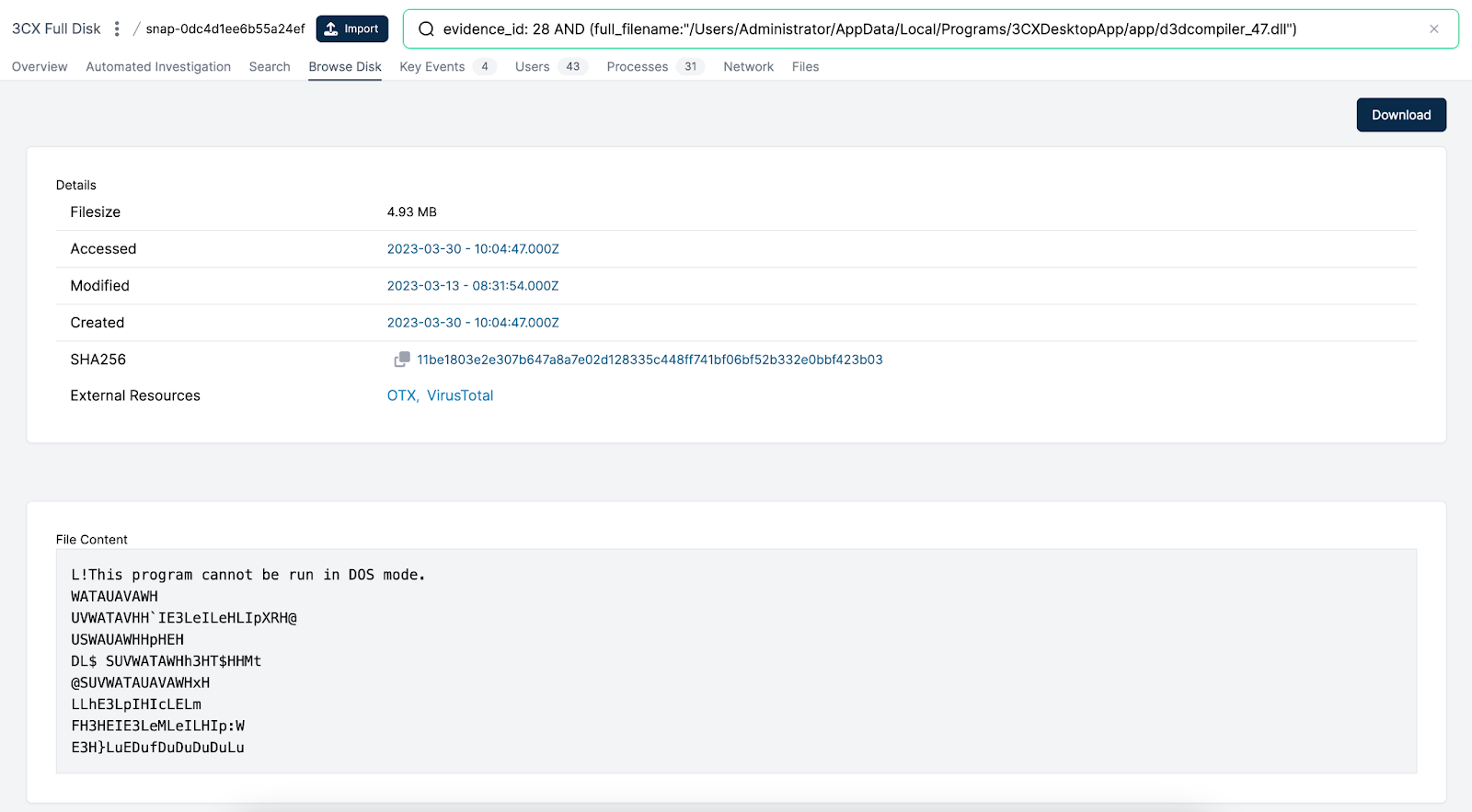
Update.exe is used to update the application, and has been seen pulling down the compromised version.
Whilst the analysis above has been performed on a dead disk (in this case for speed an isolated EC2 system) we can also perform a live collection which shows the open files for the 3CX application at the time of collection:
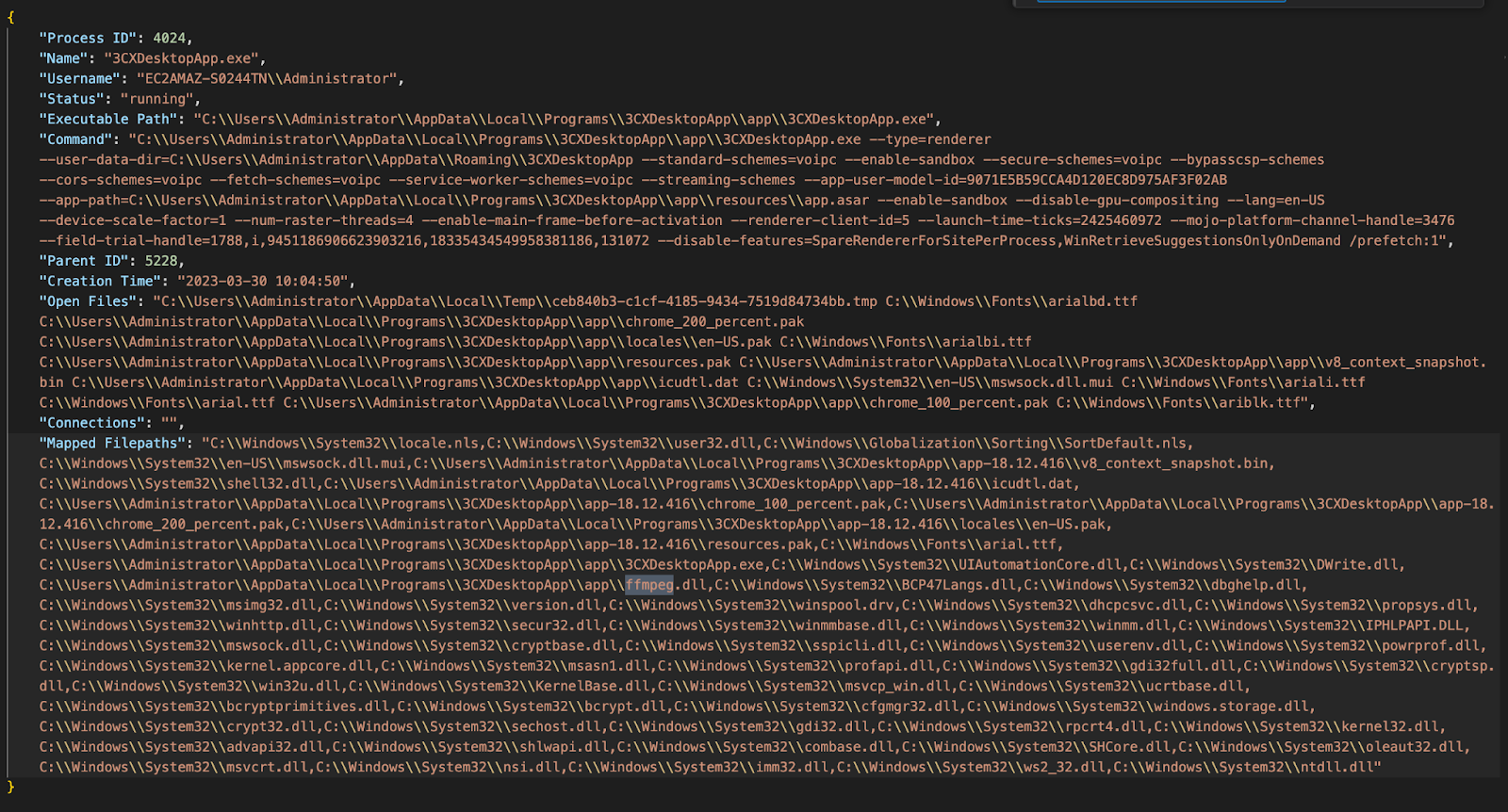
For now that’s it - I was hoping to show the forensic artefacts showing the credential stealing but it hasn't been executed in this environment.
If you’d like to follow along…
If you’d like to try out Cado Response, you can get a free trial here.
Indicators of Compromise and Yara Rules
rule APT_Trojan_Win_3CX {
meta:
description = "Detects malicious ffmpeg dll used in 3CX supply chain attack"
author = "mmuir@cadosecurity.com"
date = "2023-03-30"
license = "Apache License 2.0"
hash1 = "7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896"
hash2 = "c485674ee63ec8d4e8fde9800788175a8b02d3f9416d0e763360fff7f8eb4e02"
strings:
$rout1 = { 4C 8D 4C 24 48 4C 89 F1 4C 89 EA 41 B8 40 00 00 00 FF 15 9C 3E 24 00 85 C0 74 22 4C 89 F0 FF 15 27 8E 3B 00 4C 8D 4C 24 48 45 8B 01 4C 89 F1 4C 89 EA FF 15 7B 3E 24 00 EB 03 45 31 F6 }
$rout2 = { 48 8B 05 E2 EA 24 00 48 31 E0 48 89 44 24 28 48 C7 44 24 20 00 00 00 00 81 FA BE FF FF 7F 0F 87 A2 00 00 00 89 D6 48 89 CF 8D 56 40 48 8D 4C 24 20 E8 B3 94 01 00 }
$rout3 = { 44 0F B6 CD 46 8A 8C 0C 50 03 00 00 45 30 0C 0E 48 FF C1 48 39 C8 }
$xor = { 33 6A 42 28 32 62 73 47 23 40 63 37 00 }
condition:
pe.characteristics & pe.DLL
and all of them
and filesize < 3MB
}

