We’ve recently added some new functionality to cloudgrep, the open source tool to search logs in cloud storage. This includes some fantstic contributions from the community too.
1. Scanning with Yara Rules
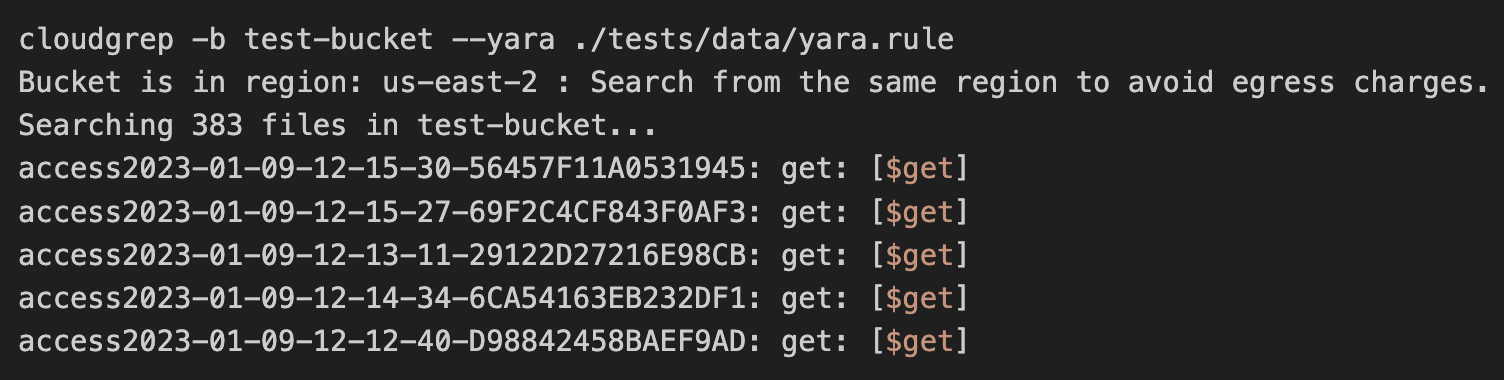
You can now run Yara rules with CloudGrep, like so:
cloudgrep -b my-bucket -y path/to/yara_rules_file.yar
In this example, -b my-bucket specifies the AWS S3 bucket to search, -y path/to/yara_rules_file.yar points to the file containing Yara rules. This is useful for scanning binary files in cloudstorage for malware and other patterns.
2. Output in JSON Format
You can now output any matches in JSON format, making it easier to integrate cloudgrep with other tooling and data-pipelines:
cloudgrep -b my-bucket -q "search query" -jo > output.json
Here, -b my-bucket specifies the bucket, -q "search query" is the search query, and -jo (or –json_output) enables JSON output, storing the output in the file “output.json”.
Many thanks to Daniel Bohannon and Andi from Permiso for this additional functionality.
3. Parsing Custom Format Logs
CloudGrep now supports parsing custom format logs, such as CloudTrail logs.
Command-Line Example:
cloudgrep.py -b my-bucket -q "search query" -lt cloudtrail
This command searches in my-bucket, where -q "search query" is the query, -lt (or –log_type) cloudtrail tells cloudgrep to parse the matching files as cloudtrail.
Many thanks to Daniel Bohannon and Andi from Permiso for this additional functionality too.
Let us know
Let us know if you have any questions on any of the new features, and we’d love to see any more community contributions.
You can grab the latest release of cloudgrep at https://github.com/cado-security/cloudgrep
More from the blog
View All Posts

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

