Chaos Without Context
Analysts are constantly under pressure to reach a high conviction verdict about an alert in a matter of minutes. But, high false positive rates and lack of contextual information exacerbates this issue. Triage typically needs to be performed manually, and constantly - leading to a high rate of burnout among analysts. Add in the ephemeral nature of the cloud for further challenges, and you've got a recipe for chaos.
Depth in a Click is Possible.
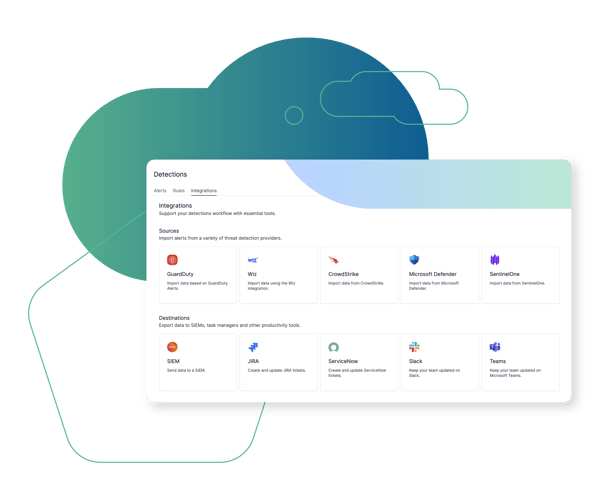
Consistent and Automated Acquisition
Users don't need to know what data they require, where it resides, and how to access it - nor do they need to manage complex playbooks. Cado Security automatically ingests alerts and contextual data, as well as performs fast triage acquisition of impacted resources to provide a fully contextualized dataset for deep visibility.

Make Sense of the Chaos
Cado Security's leading automatic investigation allows you to make sense of the plethora of data and alerts, distilling this down into critical context and key events. Our AI generated attack summary provides a a concise summary of the dataset to accelerate your understanding.
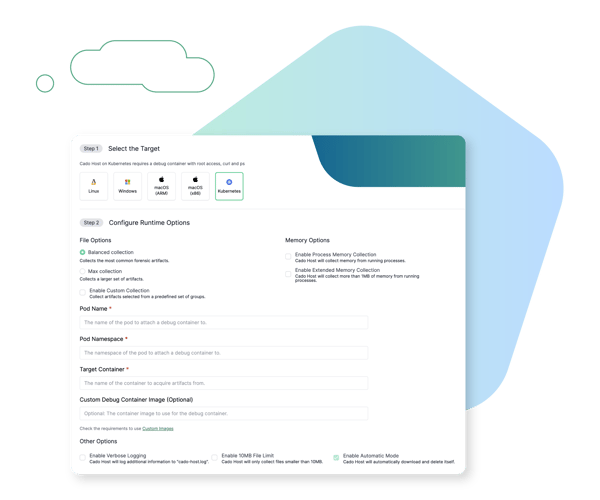
Hybrid Environment? No Problem.
Cado Security's data acquisition methods are built for cloud, on-prem, and SaaS environments. Our automation will facilitate data capture before it's gone forever.
Browse Other Use Cases
Explore other ways security teams are using the Cado platform to advance their mission.
Cross Cloud Investigations
Investigate incidents identified in AWS, Azure, and GCP in a single pane of glass.
Container & K8s Investigations
Perform container investigations in environments including EKS, AKS, GKE, and Kubernetes.
SaaS Investigations
Analyze SaaS logs alongside other critical sources to investigate compromises such as Business Email Compromise (BEC).
Cloud Detection & Response (CDR)
Marry threat detection with automated forensic collection and investigation to expedite response to cloud threats.
Evidence Preservation
Ensure evidence residing in ephemeral environments is immediately captured and preserved before it disappears.

The Cado Advantage
Cado Security is helping organizations around the world achieve results.








