
It’s When, Not If
Being impacted by an incident is a ‘when’, not ‘if’ situation. Still, many organizations find themselves constantly in a reactive mode, chasing alerts without an opportunity to pause and evaluate the effectiveness of their incident response program. As a result, it is often during the heat of an investigation when security teams discover major gaps.
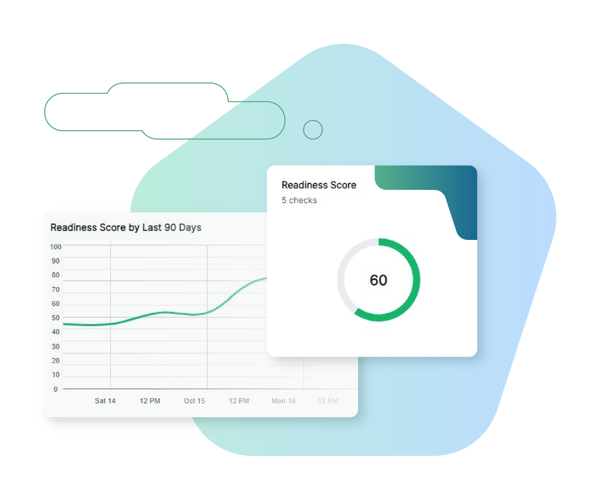
Preparation is Key
Cado Security enables organizations to embrace a proactive approach to incident response. With Cado’s Incident Readiness Dashboard, security teams can proactively run readiness checks, get a readiness score, understand trends over time, and mitigate issues that could prevent the organization from rapidly investigating and responding to active threats.


Hear from our Customer, Agorà Security

“I can now confidently say I know what’s going on in my cloud.”
Cyber Security Incident Response Manager
Global Media Company

“After testing out the product, the decision to purchase was a no brainer. Cado makes things simple.”
Director, Incident Response
Large Video Gaming Company

The Cado Advantage
Cado Security is helping organizations perform incident response forensics around the world.

Browse Other Use Cases
Explore other ways security teams are using the Cado platform to advance their mission.
Cross Cloud Investigations
Respond to incidents identified in AWS, Azure, and GCP in a single pane of glass.
Container & K8s Investigations
Perform container investigations in environments including EKS, AKS, GKE, and Kubernetes.
Endpoint Triage
Automate triage acquisition of endpoint resources to gain immediate event insights and facilitate quick escalation.
BEC Investigations
Analyze SaaS logs alongside other critical sources to investigate compromises such as Business Email Compromise (BEC).
Cloud Detection & Response (CDR)
Marry threat detection with automated forensic collection and investigation to expedite response to cloud threats.






