In this blog we’ll explore how the Cado Security platform leverages the MITRE ATT&CK Framework to enhance forensic investigations. By combining ATT&CK’s comprehensive knowledge with Cado’s powerful investigation capabilities, security teams gain deeper insights into attacker behavior.
What is the MITRE ATT&CK Framework?
Developed by the MITRE Corporation, ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. It’s a knowledge base that acts as a comprehensive catalog of real-world cyberattack tactics and techniques.
The MITRE ATT&CK Framework provides a universal way of understanding attacker behavior. The framework is broken down into tactics and techniques:
- Tactics: The broader goals adversaries pursue throughout an attack, beginning with “Reconnaissance” and “Initial Access”, and moving on to “Command and Control”,“Privilege Escalation”, “Persistence,” and “Exfiltration”.
- Techniques: The specific methods used by attackers to achieve their goals, including”Phishing” or “Exploiting Software Vulnerabilities.” Each technique within the ATT&CK framework is described in detail, including information on how it’s executed, potential mitigation strategies, and other related techniques.
By mapping these tactics and techniques, ATT&CK provides valuable insights into how attackers operate. This knowledge empowers security teams to:
- Identify and prioritize threats: Understand which tactics and techniques have been employed, allowing analysts to gain a quick understanding of the severity of an incident.
- Improve detection and response: Focus security measures on the most likely attack paths, allowing for faster and more effective incident response.
- Evaluate security tools: Compare the capabilities of different tools against the techniques they’re designed to detect and prevent.
- Strengthen defenses: Identify gaps in an organization’s security program and prioritize mitigation strategies based on real-world attack methods.
The MITRE ATT&CK Framework is widely used by the cybersecurity community and is leveraged for threat intelligence, red teaming, blue teaming, threat hunting, and security tool development purposes. The framework is continuously updated with new information to keep up with the constantly evolving threat landscape. The goal is to ensure security teams always have access to the latest knowledge needed to stay ahead of cyber threats.
MITRE ATT&CK Framework and Cado
The Cado platform automatically aligns incident data to MITRE ATT&CK tactics and techniques to help guide an investigation. As an example, we will take a deeper look at a resource hijacking attack. In this case, the attacker uses techniques such as timestomping, ingress tool transfer, and service execution to deploy crypto mining malware on a compromised EC2 instance.
Cado’s Project Overview tab provides security teams with a high-level overview of any given investigation. Within this dashboard, security teams can quickly see the top five MITRE categories relevant to the incident. In the case of this resource hijacking attack, the Cado platform found that the top MITRE categort associated with this incident is TA0004, with 12 events relating to this category. TA0004 is the MITRE ATT&CK Framework ID for Privilege Escalation Tactics. The next category associated with this incident is T11496, this is the MITRE Attack Framework ID for Resource Hijacking.
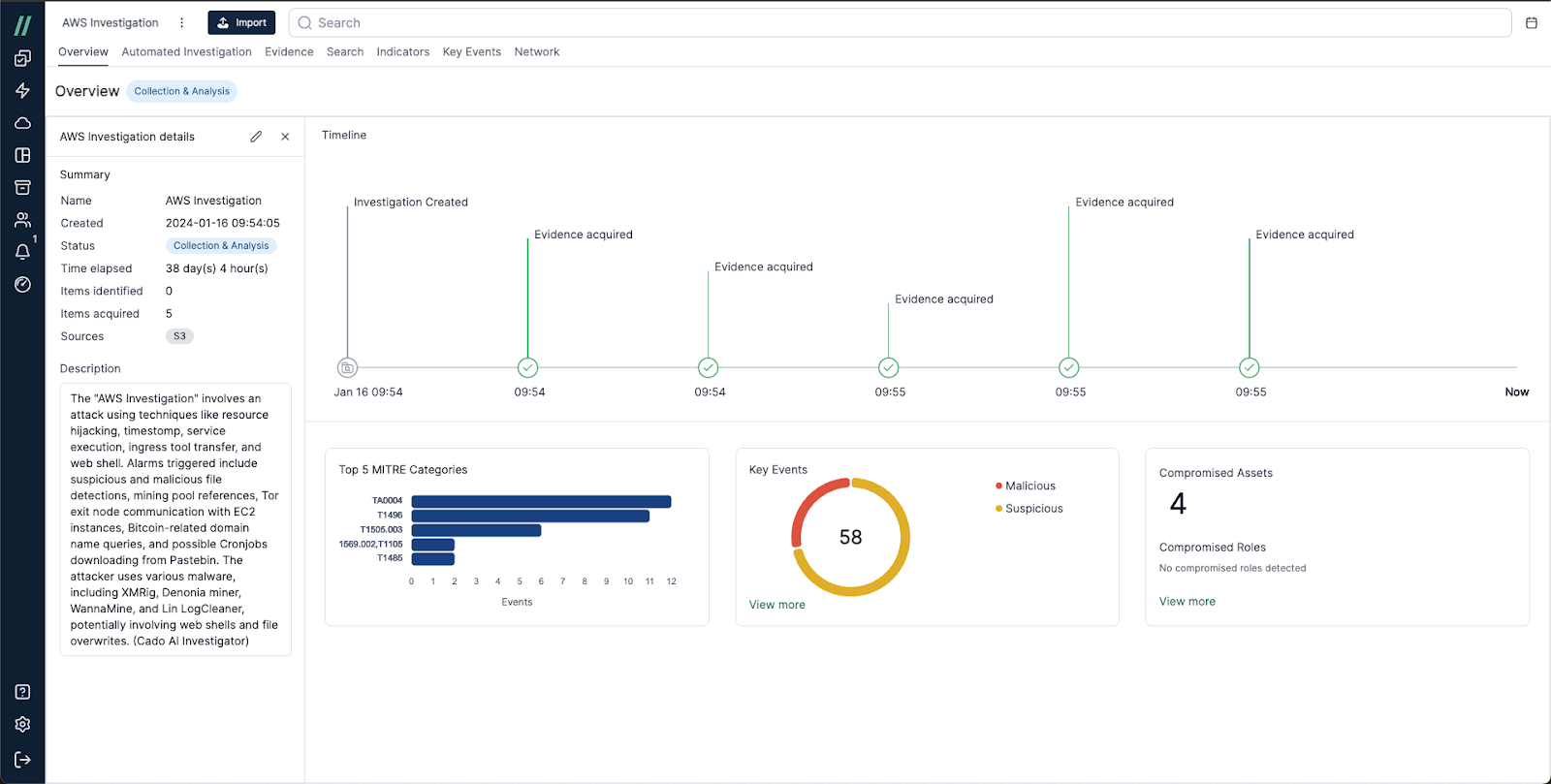
Cado’s Overview Tab
Pivoting to Cado’s Automated Investigation tab, we can see even more details about the ATT&CK Categories that align to this investigation. For example, we can see the corresponding ID’s, which link directly to the MITRE webpage for more detail on that specific ATT&CK category. The alignment to MITRE Attack categories allows analysts to quickly understand exactly what happened in a given incident.
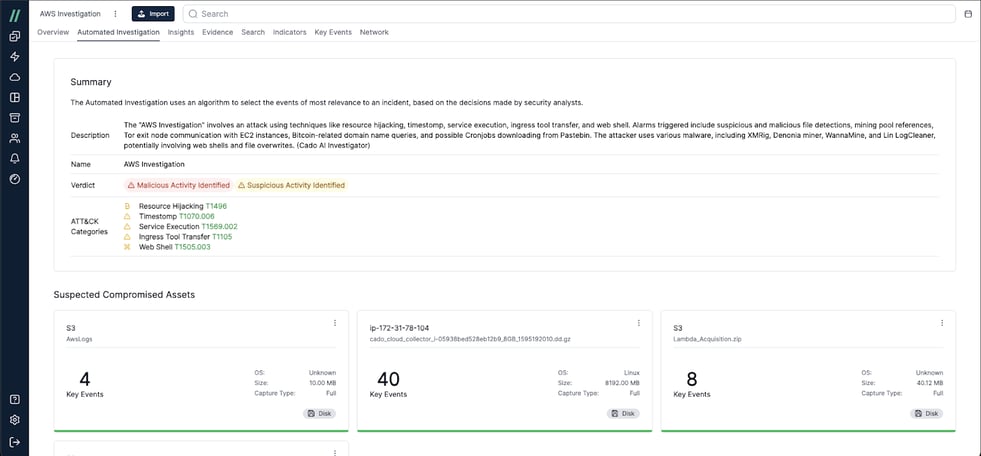
Cado’s Automated Investigation Tab
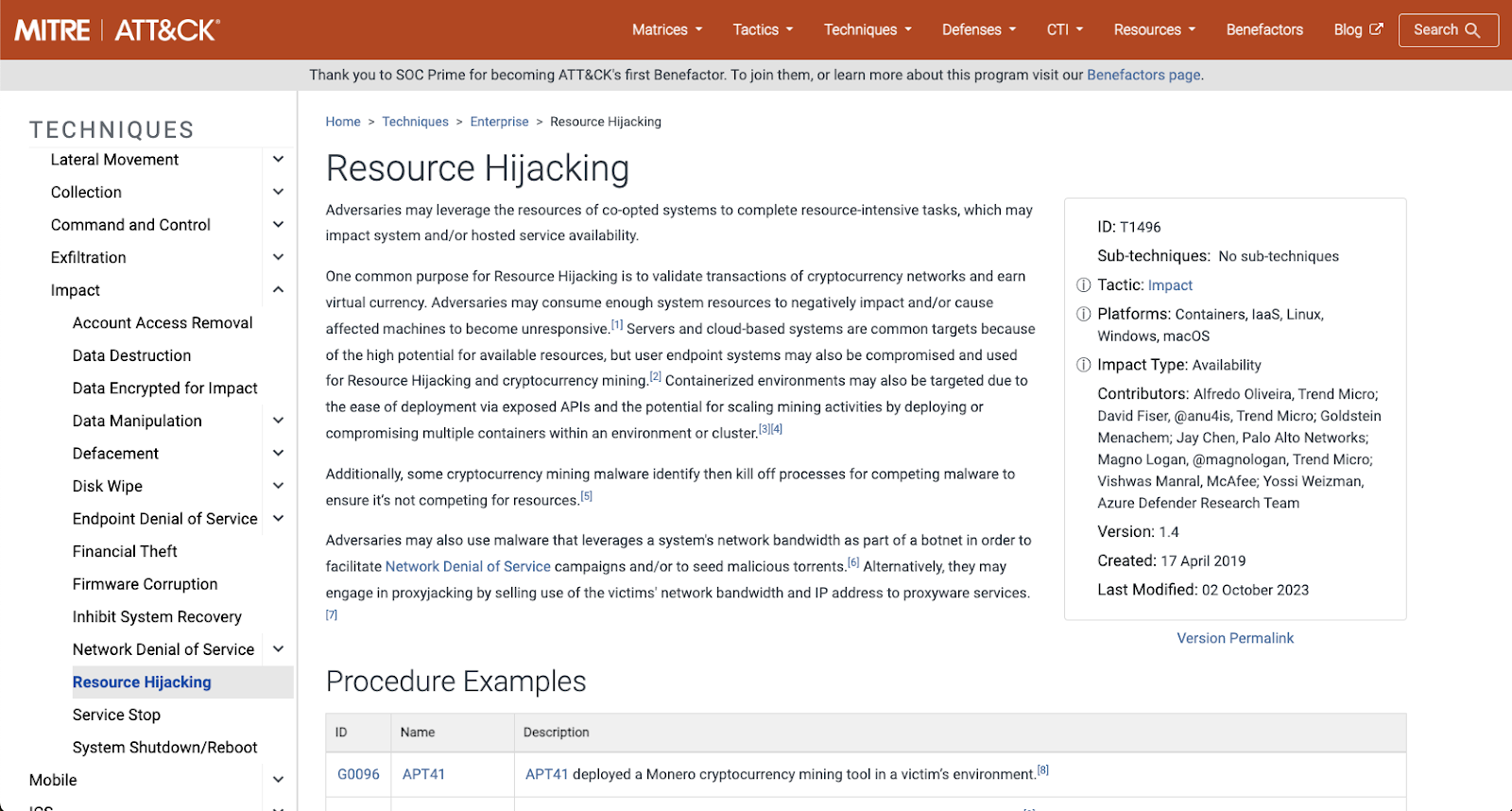
The Mitre Attack Framework page for the T1496 technique (Source)
Elevate Your Forensics Expertise with Cado Insights
At Cado, we aim to empower analysts of all levels to perform advanced forensics investigations in the cloud. To this end, the Cado development team has invested considerable effort in the way data is presented and aligned. In addition to aligning incident data to MITRE ATT&CK categories, the Cado platform leverages generative AI and automation to deliver additional incident insights, including:
- A summary of the investigation generated by Cado’s Local Language Model (LLM) also known as Cado AI Investigator
- A verdict on the investigation and whether or not malicious activity is suspected or has been identified
- A list of all assets that are suspected to have been compromised
- An overview of detected malicious and suspicious events
- A full timeline of events to help facilitate root cause analysis and easy pivoting based on key events, time stamp, user etc.
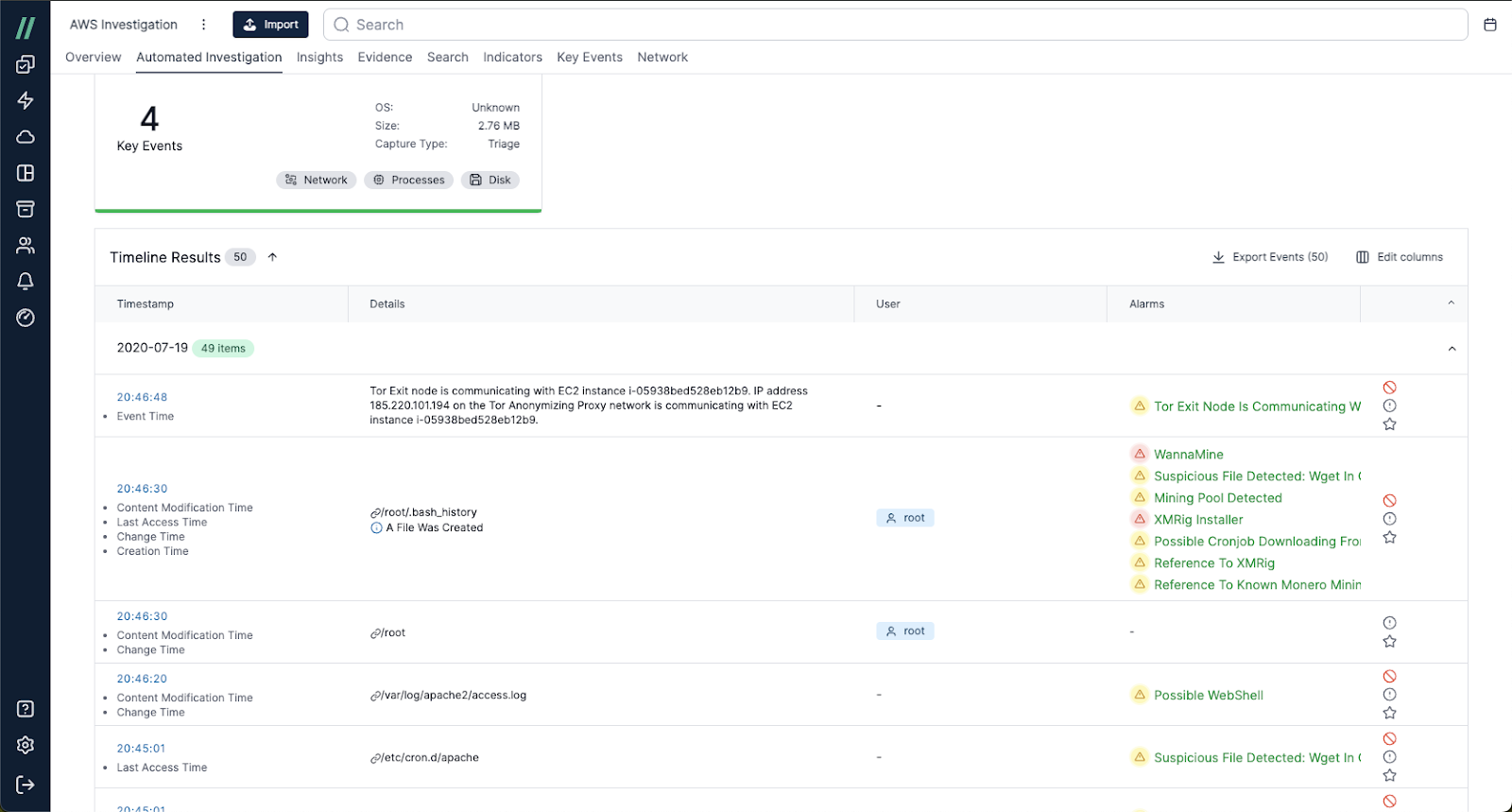
The Cado Timeline
Interested in learning more? Contact us to schedule a demo with our team!



