On a normal day, digital forensics and cyber incident response (DFIR) experts know it is tough getting hold of the forensic data they need. During this unprecedented time it is even harder to acquire data in a timely and reliable manner. Experts need to consider how to tackle forensic collection in a time of a distributed workforce, particularly when working remotely for clients.
In the DFIR world it is hard to get the balance right between getting the data you need quickly, and doing it in a forensically sound manner.
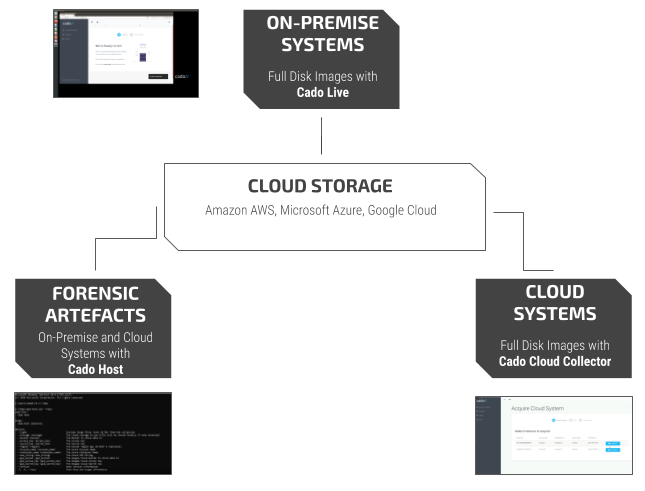
To help tackle this, we are going to be releasing three sets of free tools to the security community over the next month. These tools make acquiring forensic data into cloud storage significantly easier. We will also be releasing tools to analyse systems running in the cloud.
So what are some considerations when it comes to performing data capture? And how do you keep the balance between speed, convenience and forensic integrity?
In an ideal world you can’t beat a full forensic capture of the necessary data and investigation. However at times you need quick answers and this may not always be feasible, so a quick triage is usually a first option.
To triage, or deep dive?
There are many EDR solutions and similar out there that allow for some level of quick triage of a system. As part of this group of triage tools we will be releasing Cado Host for free. Cado Host enables you to capture key forensic artefacts in order to do a quick forensic triage of a system.
The triage approach is certainly one that is useful when it comes to speed, and getting quick answers. Most breaches normally require some level of triage to either temporarily isolate a threat, or determine what you may be dealing with. After the initial triage is complete it is always worth considering the situation and determining if you need to move to a detailed forensic investigation.
These considerations include:
- Are you dealing with a sophisticated, or savvy threat?
That would potentially know how to cover some if not all their tracks, that a full investigation may uncover.
- Is there something missing, when you feel something should be there?
This could be a sign that either the right data is not being collected, or anti forensics techniques have been deployed.Know how your tools work under all circumstances, and never assume it is giving you everything.
- Is there the possibility that this would turn into a legal, enforcement, or regulatory issue?
If so – triage and data collection from endpoint tools are unlikely to cut the mustard here. You should consider taking a forensically sound copy of the systems impacted – and an appropriate evidentiary chain of custody. After all, you would hate to be the reason either the bad guy gets away, or be the cause of losing a legal case…
- Is the system impacted changing, need to be replaced, or being reimaged?
It might become apparent later that you need to go back and look at a system as it was part of a bigger picture you didn’t know about at the time. It is good practice to store a forensically sound image of a system. Even if not analysed, it is there if you need to go back and analyse it in detail at a later date.
More often than not the initial machine triaged in major breaches I have investigated have not been the root cause, or the sole system impacted. The last thing you want to do is blow away your one and only tether required to identify the root cause.
A deep dive investigation can be more difficult than a quick triage. Particularly when it comes to forensically capturing the data and systems required.
To help the community we will be releasing the Cado Live and Cado Cloud Capture tools free, to make it easier to remotely capture systems in a forensically sound manner.A little later, we will also be releasing our main Cado Response Platform that will make remote response and forensics even easier for DFIR, IT and security teams.
Please feel free to sign up to our private beta, and we will give you updates when this is ready later down the road.
For the Community – Tool Preview
We would love to hear your feedback, and as a first step we are putting out a request for what host artefacts DFIR and Security professionals want collected by a forensic tool.We’re having that discussion over on LinkedIn and Twitter – so please let us know!
Now onto the tools we will be releasing…
Cado Live
Just image the Cado Live system to a USB drive and boot the compromised system. Then you can securely image the full system up to AWS S3, Azure Storage or Google Cloud Storage!
Are you working with a client on the other side of the world? You can instruct them how to create the Cado Live USB, or courier a USB stick to their office. You can then easily forensically image their systems remotely by just asking them to plug in a USB stick and follow some simple steps.
Cado Cloud Capture
Cado Cloud Capture is a tool to make acquiring forensic images of AWS EC2 instances significantly easier.
You can use it to make a forensic copy of a system into Amazon S3, then either analyse it in the cloud or download the image for further analysis.
Cado Host
Cado Host is a tool to quickly capture live forensic data and upload it directly to cloud storage such as Amazon AWS, Microsoft Azure or Google Cloud.
It runs on Windows, Linux and OSX and collects a long list of forensic artefacts.
Do you have any suggestions on what gets collected? Let us know on LinkedIn and Twitter.
You can manually deploy it on a single system of interest. You can also deploy it across a fleet to centrally collect data for threat hunting and forensic analysis.

