KAPE (Kroll Artifact Parser And Extractor) and Cado Community Edition are both great free tools for DFIR professionals. You can get a free download of KAPE here, and a free deployment of Cado Community Edition here.
Below we’ve outlined how you can use KAPE with Cado Community Edition, using a canonical example of WannaCry infecting a Windows Server install. If you’d like to follow along with this investigation yourself, you can download the test data (a KAPE collection) from our Github repo. Note: KAPE also has the ability to parse artifacts itself, but in this case, we’ve used the Cado platform.
Set up
We downloaded and ran a WannaCry sample to the desktop as “OpenMe.exe”. This isn’t how WannaCry would typically end up on a system, but it serves for the purpose of this example.
After about ten seconds, the familiar “Oops your files have been encrypted" message popped up on screen, and we ran a collection with KAPE. For this, we ticked the option to collect all artifacts and ran a collection:
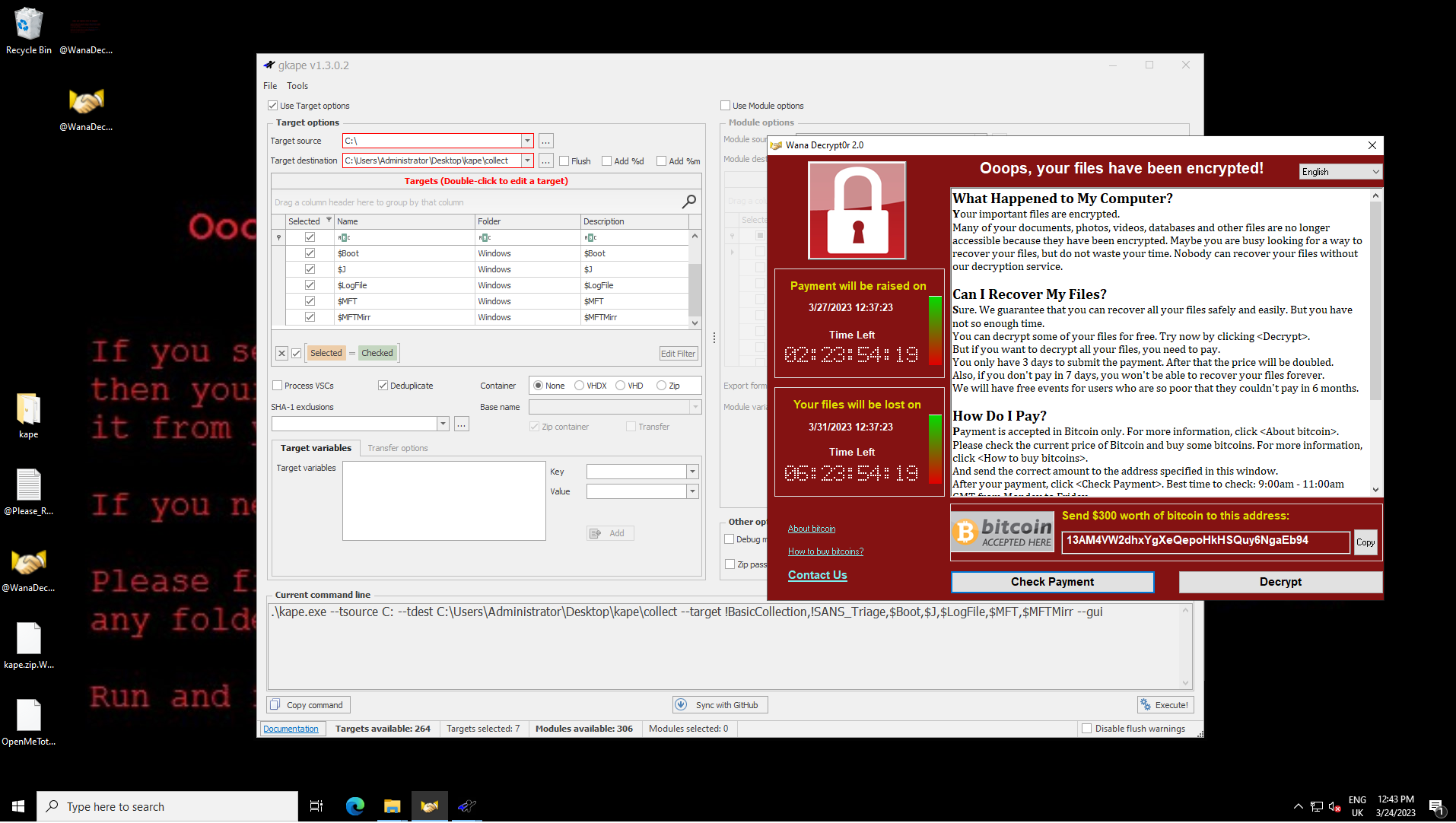
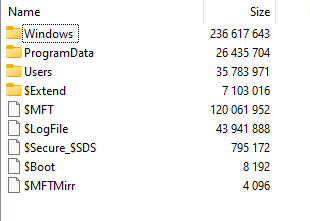
KAPE has the benefit of both being fast and complete - the output for this fairly vanilla Windows system was a 65 mb zip file:
KAPE has the option to collect directly into S3, though in this case we copied it over manually and imported into the Cado platform:
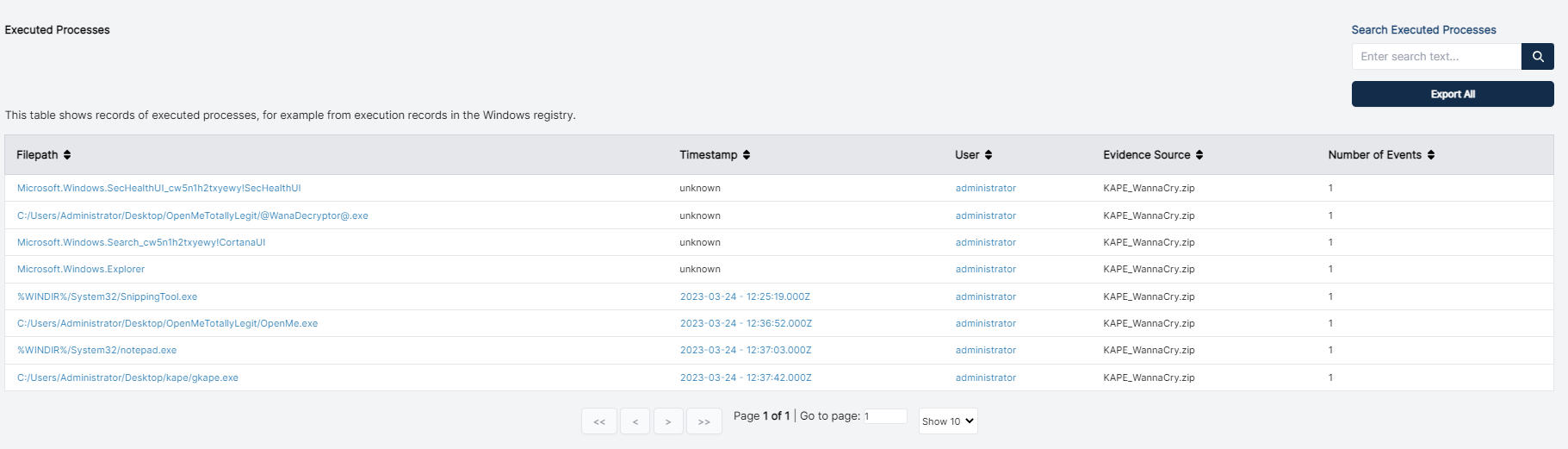
Processing the Zip file takes about 10 minutes, after which we have a few leads to start with. This is a vanilla system so the execution of “OpenMe.exe” sticks out like a sore-thumb:
Pivot #1 - Time
The root of any investigation is the “pivot", and pivoting on the execution time of “OpenMe.exe” shows a number of clearly related events:
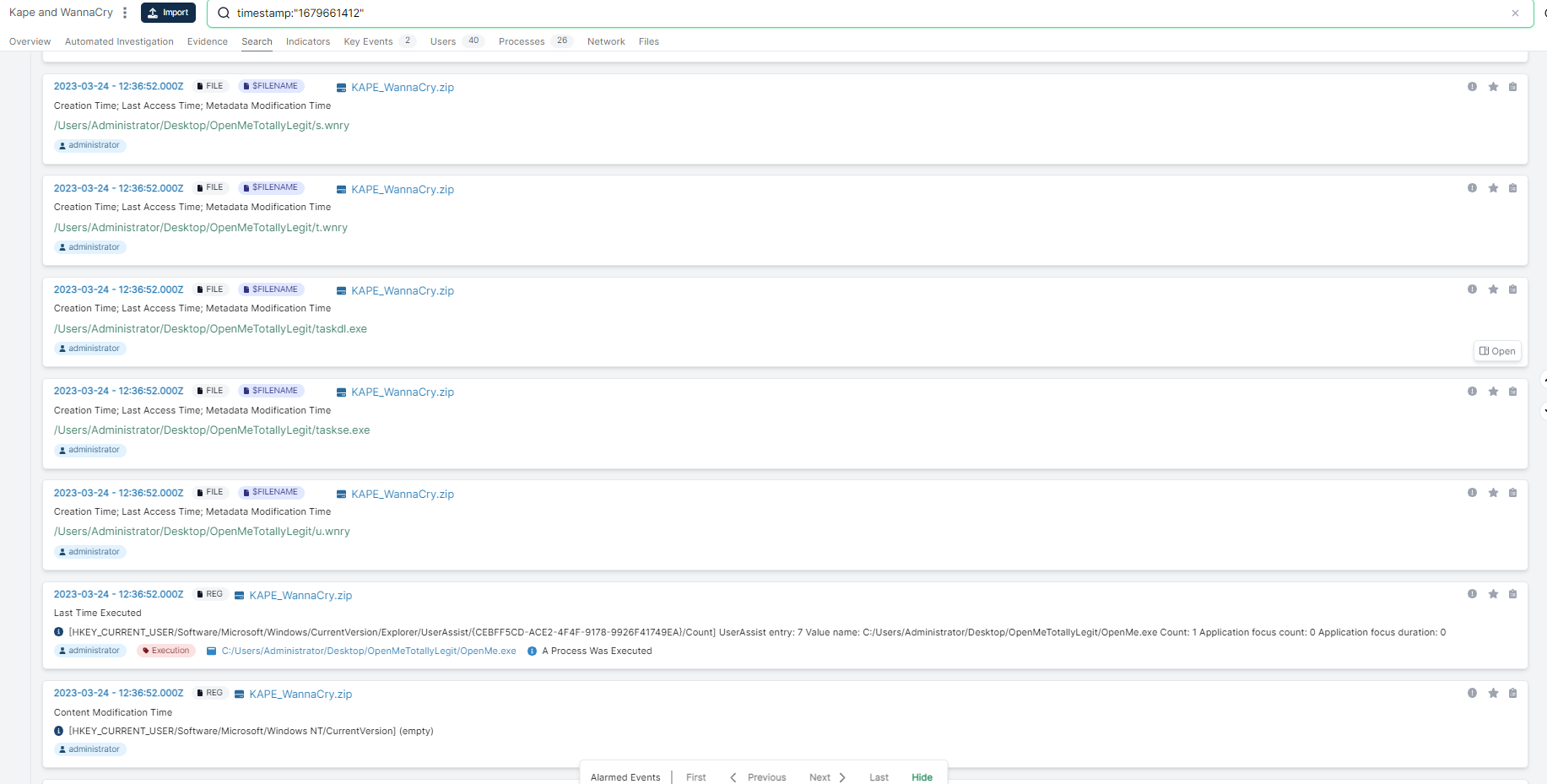
This includes the known WannaCry indicators taskdl.exe and taskse.exe. This comes from a number of locations, such as the parsed MFT and Registry as well as more esoteric forensic artifacts such as OLE data.
Pivot #2 - On the Username “administrator”:
We can also pivot on the username. Let’s pivot from this process screen onto the user “administrator”. From here, we can quickly see process execution events:
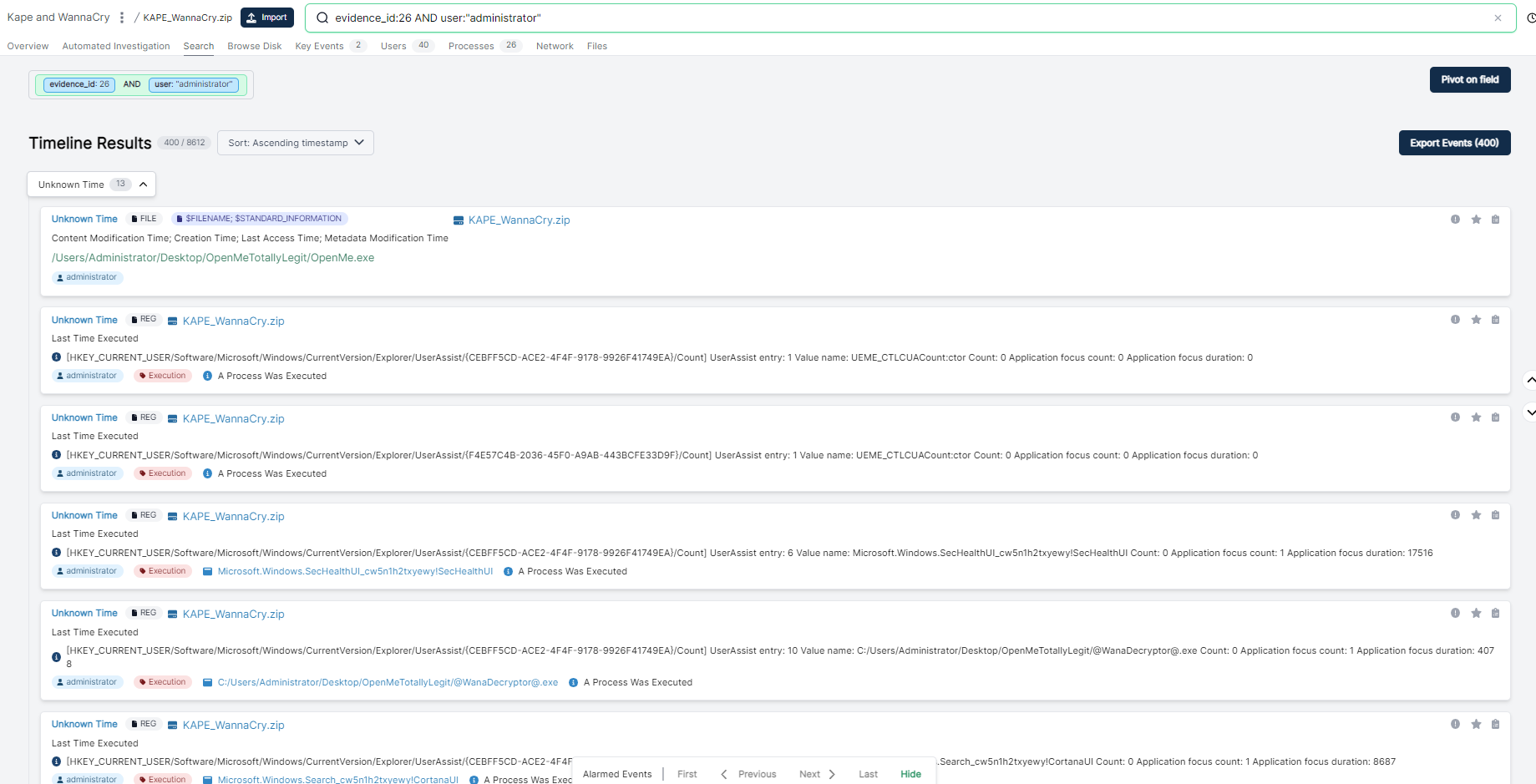
As well as parsed out sqlite databases from Windows:
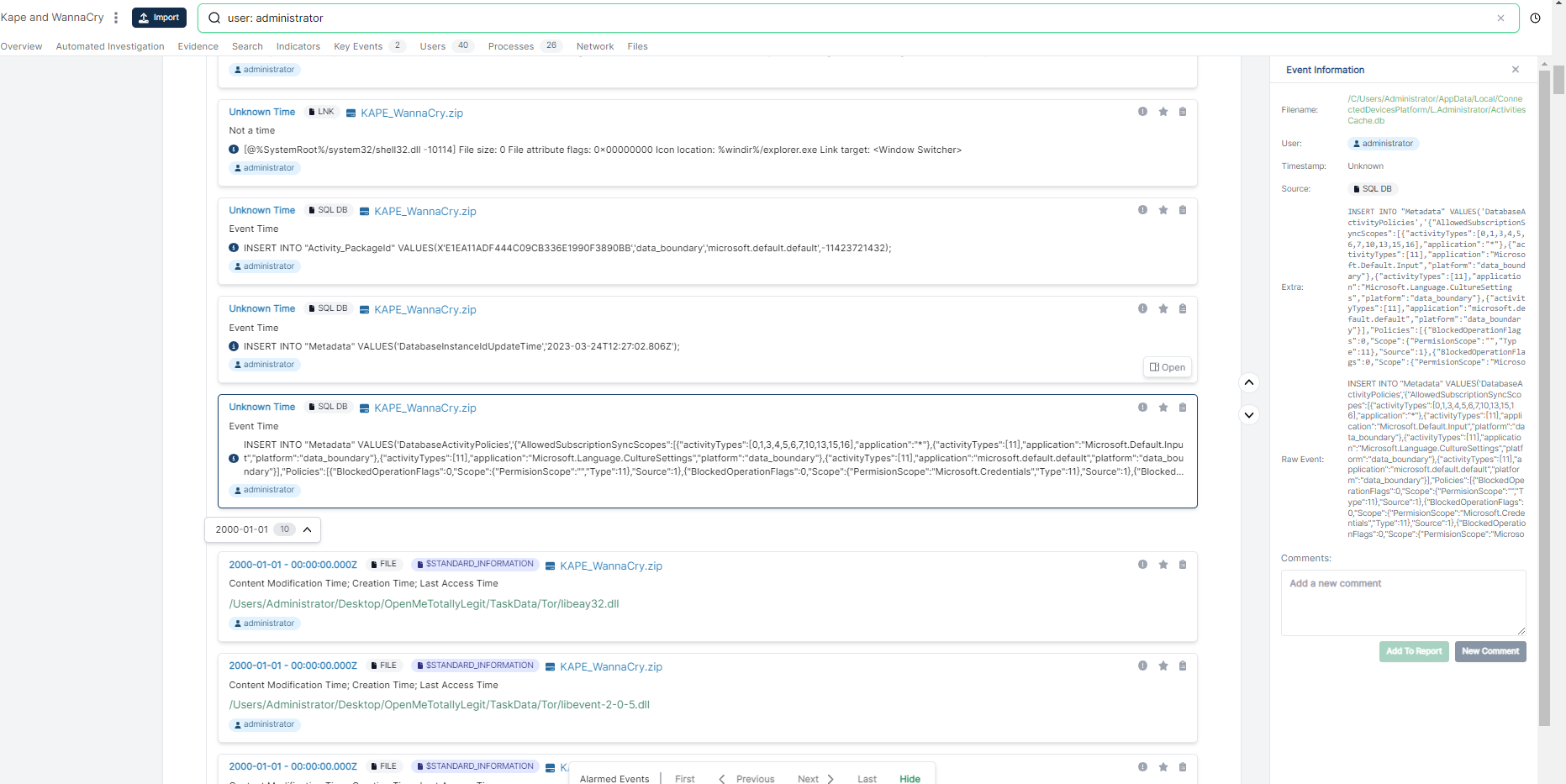
...and a bunch of other events. So let’s dive in on the period in question. We can narrow in on events from the user “administrator” from the last week pretty easily:
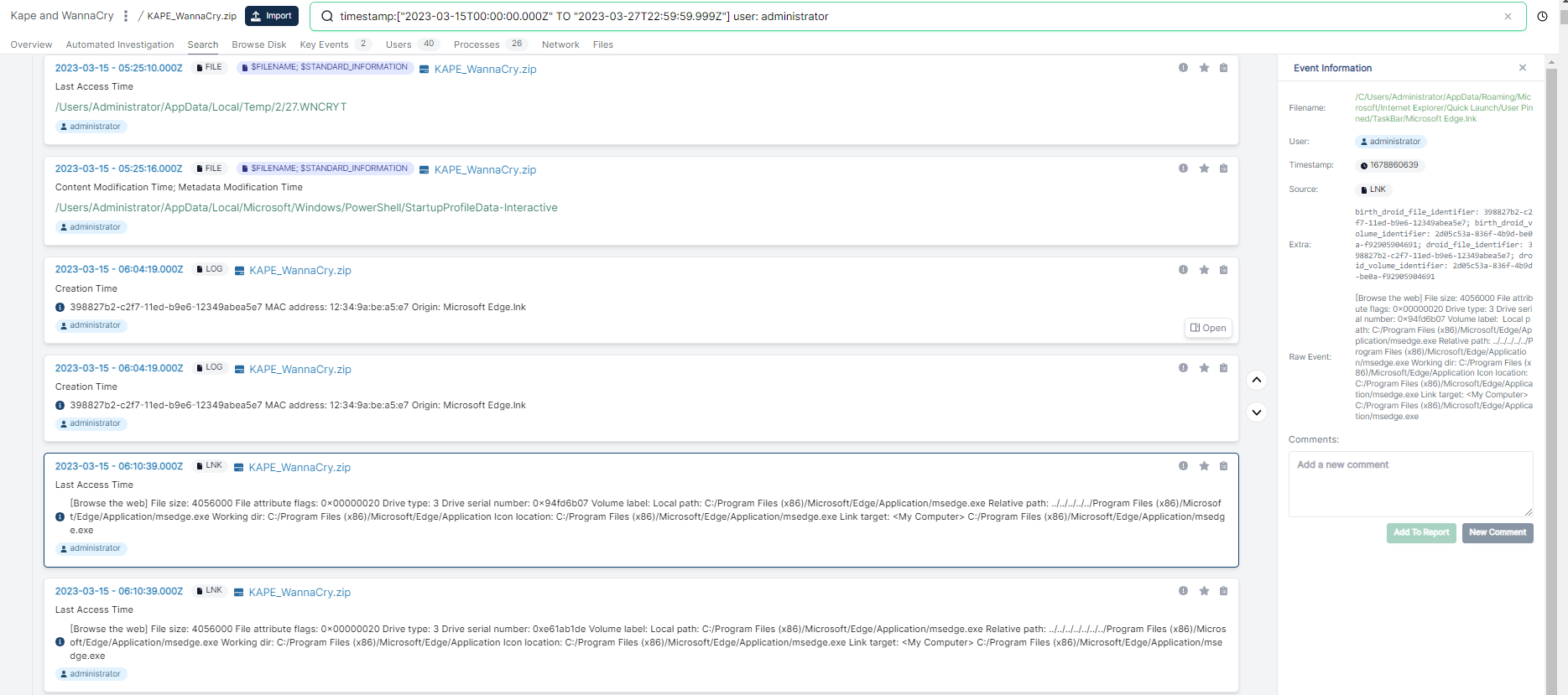
This returns some more relevant events:
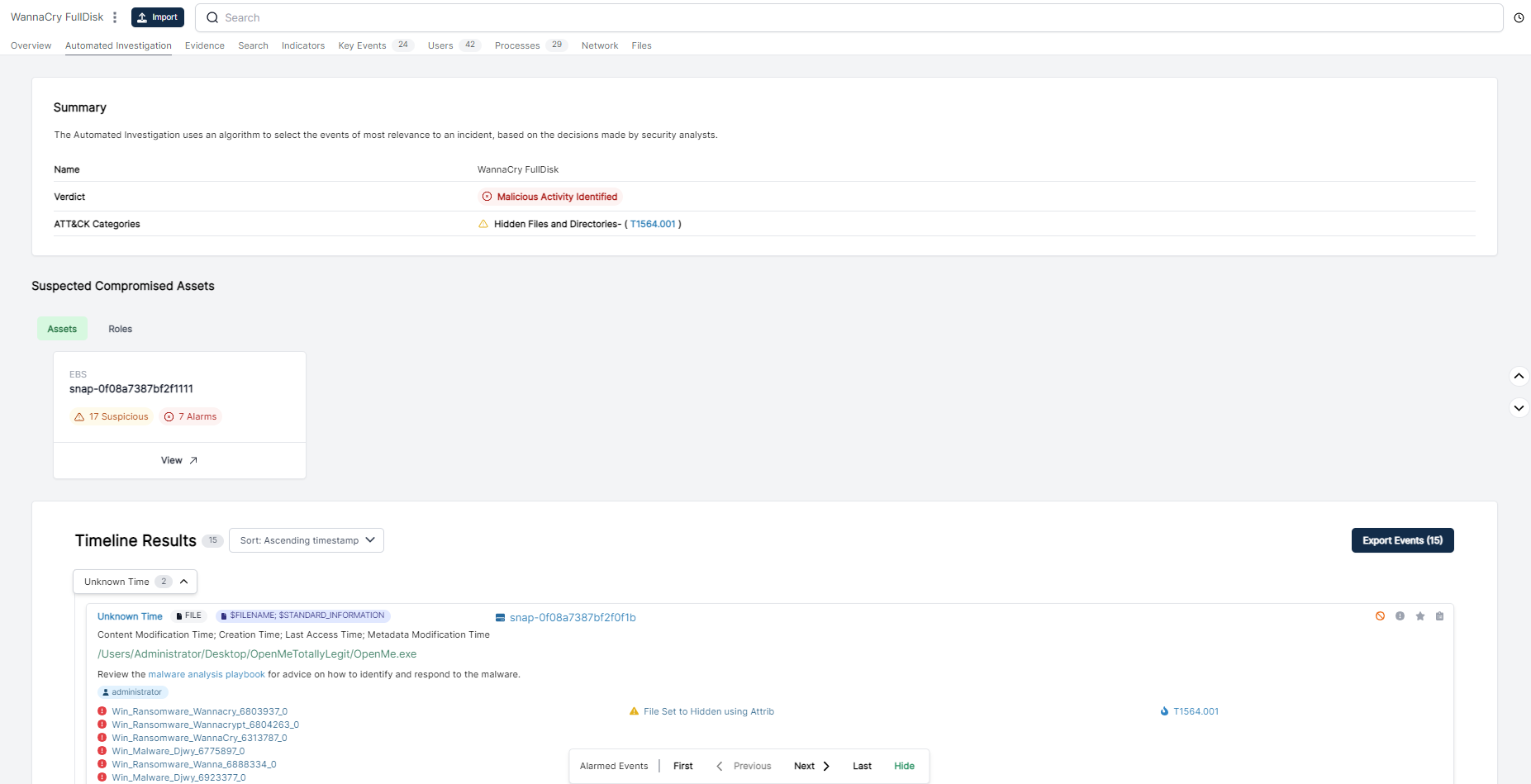
Vs Full Disk
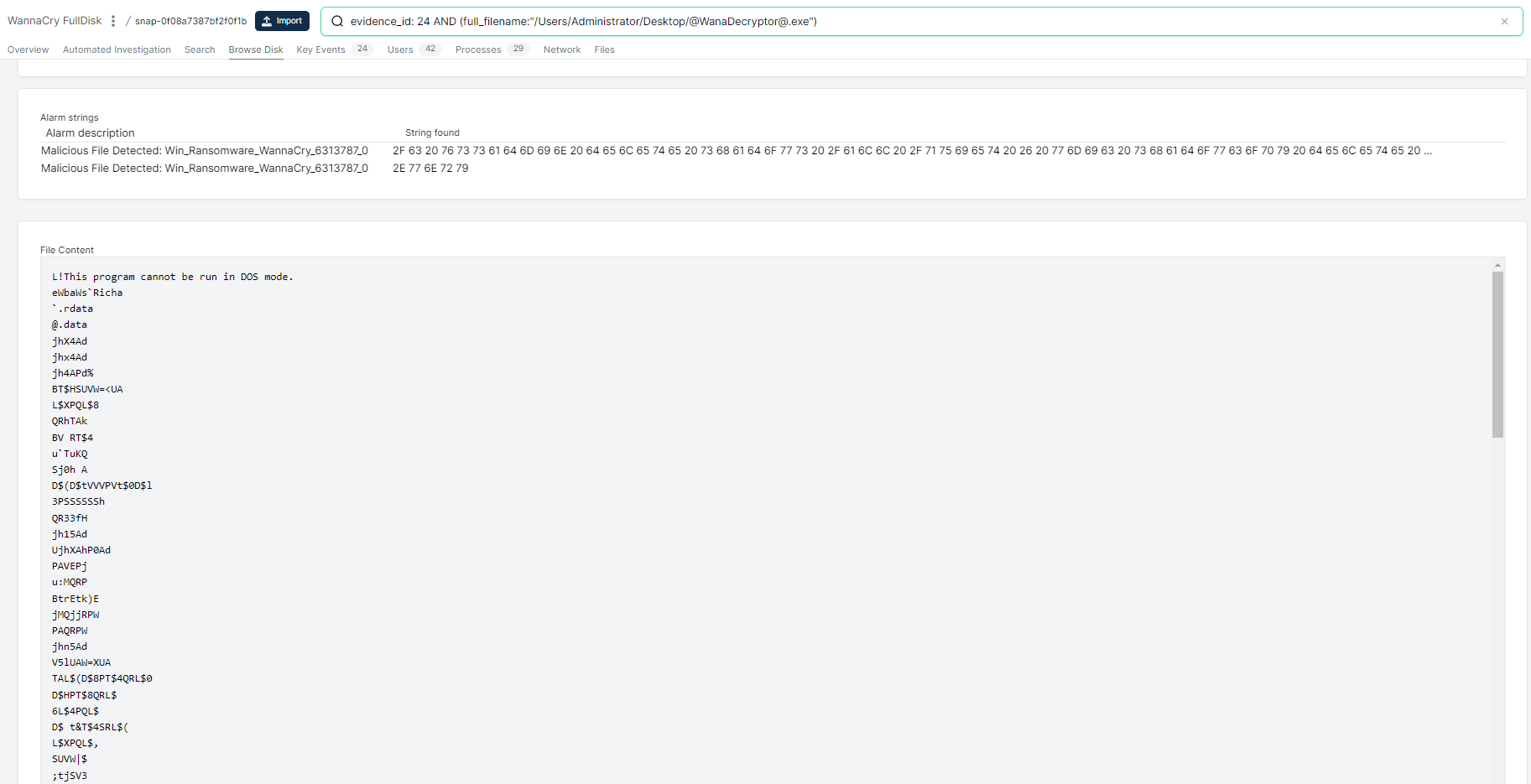
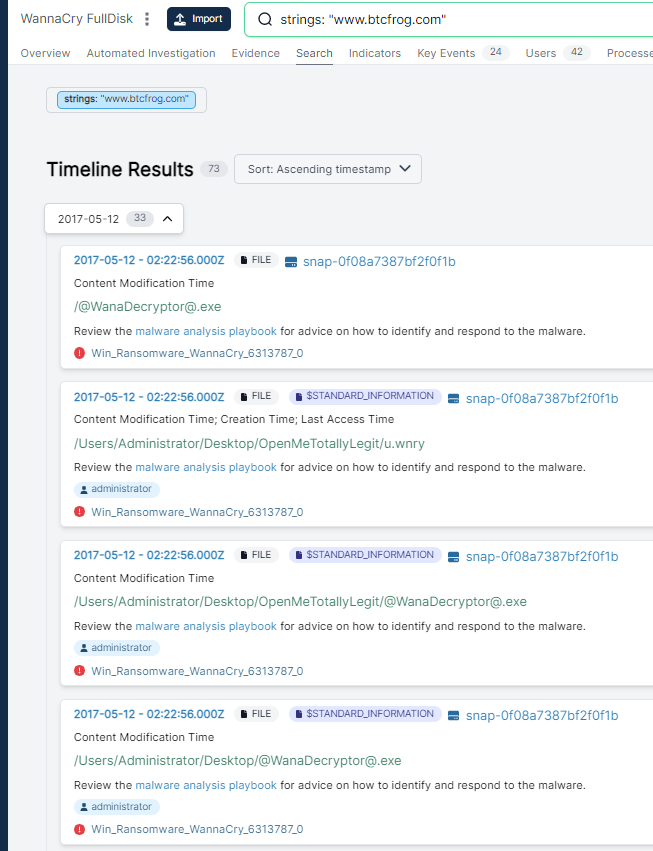
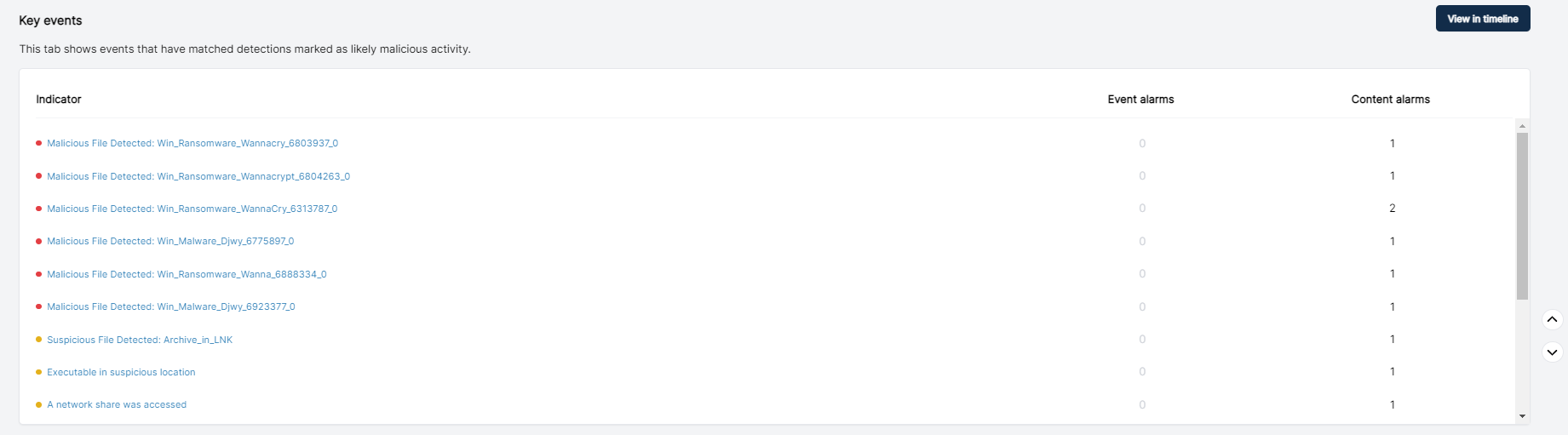
Obviously there is a down-side to triage collection, which is that you miss some depth. I performed a full disk capture of the same system using Cado. Acquiring full disk gives you the ability to browse, search and download any files from the impacted system:
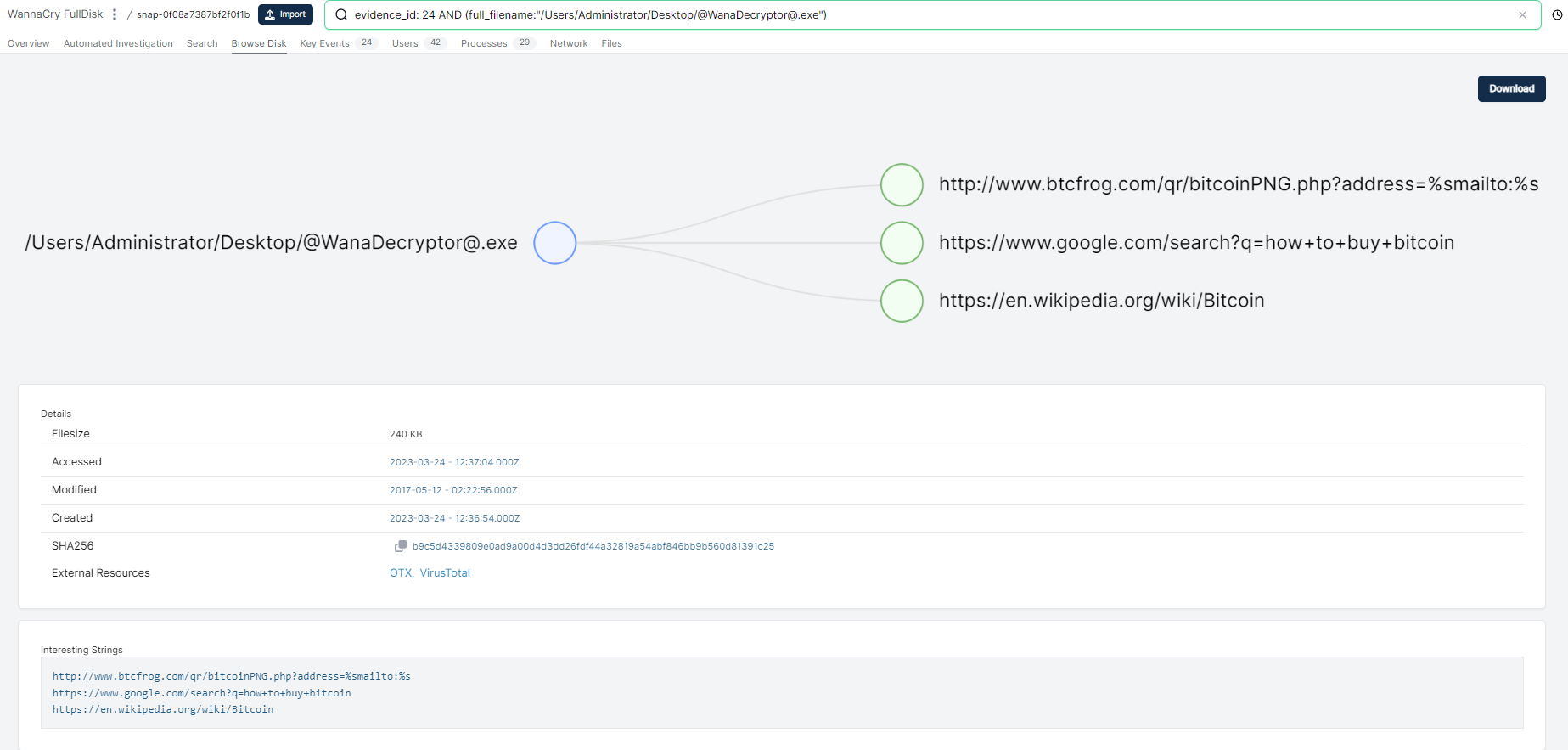
More Information
You can get a free download of KAPE here, and a free deployment of Cado Community here.
Let us know how you get on!
M

