Happy New Year!
There's no doubt 2020 was a tough year for most and 2021 continues to bring challenges. But like all periods following great change, 2021 will bring opportunities too. The long-promised ‘work from home’ transformation is here to stay. Technological improvements from contactless payments to distance learning have been deployed in months rather than years.
And we’re pleased to be sharing some of the exciting things happening here at Cado Security too:
- We have strategically expanded our team. More news on that coming soon.
- We were named one of the Forbes 20 Best Cybersecurity Startups To Watch In 2021. It was great to see us included amongst other innovative companies on the list. We feel more compelled than ever to deliver on this expectation by sharing plenty of exciting news and announcements as the year continues.
- Our free tools are helping organizations collect and analyze cloud data. Hundreds of organizations have downloaded them in the last 6 months.
- We have kicked off our pilot program, which has been an exciting milestone. If you're interested in our platform feel free to register your interest.
I’ve been reflecting on 2020 and realized: if anyone had told me a year ago that a global pandemic would take place during the same time that I’d be running and building a company from scratch, I would have told them they were crazy. Yet, they would have been spot on. Which in turn, makes me feel even more proud of what Cado Security has accomplished during what was a very tough year for all.
Will 2021 throw us as many curveballs as 2020? I don’t have a crystal ball, however, Chris and I put together some thoughts on a few predictions that we think are sure to come this year:
Did someone say Supply Chain?
Yes, the supply chain. There’s no shortage of 2021 predictions saying that supply chain attacks will be a big deal. Often with an implicit suggestion that there is an easy answer to attacks like the one that hit SolarWinds. Of course - supply chain attacks are nothing new, and they are incredibly difficult to detect.
In the case of SolarWinds - the wider campaign was finally identified through strong processes rather than simple detections. FireEye network administrators investigated the addition of a new two-factor authentication device, then started tracing the attack back to SolarWinds. Less discussed, there was almost an earlier identification thanks to painstaking forensics work by the team over at Volexity. They traced the source of a June 2020 compromise to a SolarWinds machine.
The attackers did a great job blending their backdoor in with legitimate SolarWinds code. The only realistic chance someone would have of detecting the specific backdoored installation itself, would be a full forensic search of key servers for suspicious applications with obfuscated keywords.
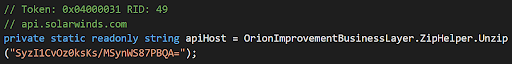
A deep forensic investigation of key servers in your environment won’t guarantee you can identify the next SolarWinds - but it will give you a much better fighting chance. Particularly if you're on the look out for attackers “living off the land”. This is where attackers blend in and utilize normal administrative credentials after initial access has been obtained. Why use fancy malware to hop about once you have access, when you can blend in with the legitimate administrators, utilizing the same credentials and tool sets to get about.
It is incredibly important to perform “deep dive” forensics of serious breaches to understand the root cause. After reducing risks with prevention and best practice, we should be hunting, and performing forensics on our key information and data assets. This gives you a fighting chance to spot the unknowns and more advanced techniques.
Forensic investigations can be a painstaking process for on-premise. But, in the cloud we do not have the same constraints as traditional environments. We can operate without concern of putting too much load on production systems - Cado Response lets us create an identical copy of the suspect system without any performance impact. With this copy we can then throw as much computing power as you want at the problem. With these abilities, you can begin conducting continuous forensics: in-depth analysis as often as you want and on as many systems as you want.
We will publish a separate article soon defining what “continuous forensics” means to us.
The Rise of Cloud
We don’t really need to predict the arrival of cloud computing as it’s already firmly the standard for new infrastructure in organisations. Cloud computing continues to grow at an impressive, but sustainable rate. Whilst we normally focus on cloud infrastructure (i.e. AWS and Azure), software as a service such as Zoom and Microsoft Teams continues explosive growth. Organisations we talk to are now happier than ever to put their sensitive data in the cloud. But there are plenty of issues and risks that you need to be across, as these environments increasingly are becoming attractive targets.
Earlier in 2020 we published the first known identification of in the wild malware that steals AWS keys, and we’ve only seen more since.
Ransomware and Business Email Compromises Continue
Whilst there will undoubtedly be new trends in 2021 - much will stay the same. In particular, ransomware and Business Email Compromise may not make the biggest news, but will likely continue to be the greatest cause of concern for many businesses. These threats pose a great financial and operational risk to even the most mature organisations. It is important to keep up to date on the trends in this space. Don’t forget reducing risks here is both a technical and business challenge.
GDPR Goes Global
It’s hardly been top of the news cycle, but the possibility of the US passing a GDPR style law at the federal level is becoming more likely. On the incident response angle, the key component of GDPR is the 72 hour mandatory breach notification requirement. We can’t stress how important it is to be prepared for when (not if) that big incident happens. Being prepared can drastically reduce the impact and fall out post breach.
Stay Tuned, Folks
So that’s just a high-level run through of key updates and musings around what 2021 might bring.
But stay tuned - we’ll have some big news coming out very soon!

