When you identify an incident, the clock starts ticking. The business needs answers fast, and if you’re a public company, part of the critical infrastructure, or there’s a PII data breach, you have a very limited amount of time to get your story together before you decide if and how to notify the authorities.
Many organizations rely on an XDR to answer critical questions in the aftermath of an incident, but in many cases there are gaps. This is because XDR must be deployed and running at the time of the incident. This provides a challenge for a number of reasons:
1. Many legacy systems do not have the resources to run an XDR agent with significant memory and processing overhead.
2. Many systems are not completely or consistently managed by the IT department, and don't adhere to corporate standards, so may not have XDR installed
3. XDR agents are often not suited to highly performance-sensitive, elastic cloud systems running in platforms like Kubernetes
Chances are that a significant proportion of the computing resources in your organization fall into one or more of the categories above. So when an incident occurs, you’ll have some major gaps in coverage, which could prove fatal when trying to stitch together the elements of an attack. To make matters worse, in the case of cloud-native architectures, the attacker’s footprints may be gone by the time you get around to investigating if you’re using traditional tools.
Cado delivers a different approach to cloud incident response. The solution does not use a running agent; instead, companies can deploy a disappearing agent, or pre-install dormant binaries for when it is needed to pull back essential data about what has occurred on the system. This could be in the event of an incident, or in a threat hunting scenario.
Also, once you suspect a system has been compromised, the Cado platform allows you to perform full system capture, rebuild and automatically analyze file systems and volatile data at the time of capture so that you can get the full picture of everything that has happened. This not only shows the egregiously bad activity on the system, but everything malicious actors did - including exactly what data they accessed and what they modified.
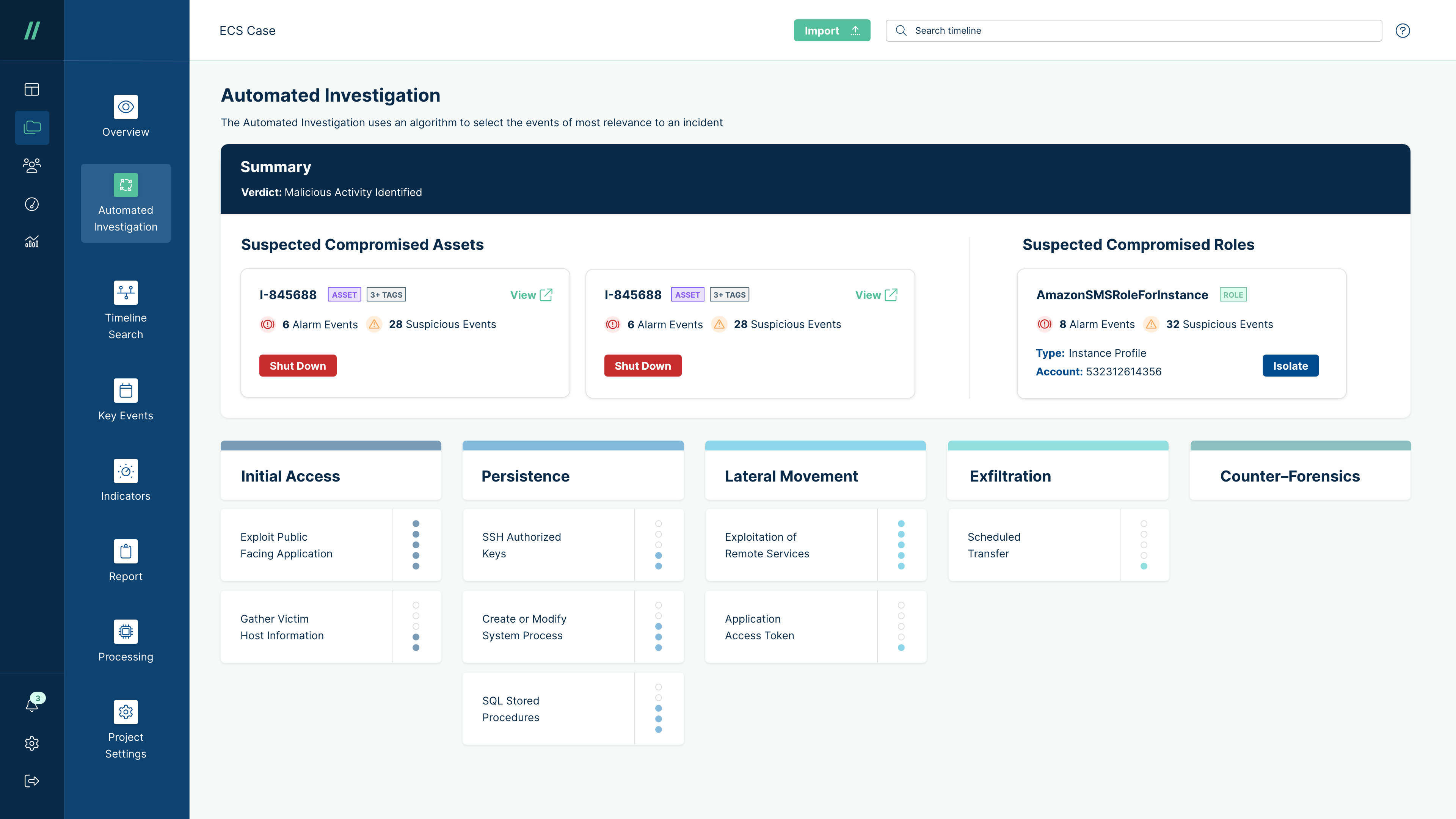
What's more, using Cado's automation capabilities, in a cloud environment, you can prepare for an incident ahead of time, and completely automate this process so that when an incident occurs you have exactly the data you need, in a readable format, when you need it. Not only that, Cado preserves the original evidence as part of a full-blown forensic investigation. This exponentially cuts down the incident response time helping you get ahead of the attack, and deal with any legal fallout.
Interested in seeing the Cado platform in action? Schedule a demo with our team or check out our 14-day free trial.

