In the last quarter, the Cado Security team has been working hard to release a number of new features and enhancements to its platform. We’re excited to tell you what we’ve been up to. Here’s an overview of the top product features we released in Q4:
Cado AI Investigator (Cado’s Local LLM)
Cado AI Investigator is a new feature leveraging Cado’s local LLM to further streamline the investigation process. Cado AI Investigator empowers analysts of all levels as well as more senior non-technical stakeholders to gain a high-level understanding of an incident, fast. For example, Cado AI investigator generates a summary of an incident and also has the ability to analyze potentially malicious files. The feature speeds up incident investigations and uplevels security teams to do their best work. Further, because it's built using a local LLM, organizations can rest assured that no data ever leaves their environment.
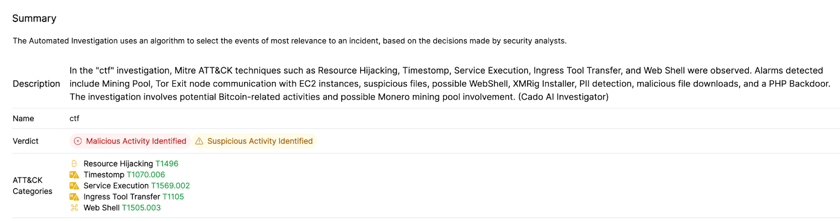
Cado AI Investigator's Summary of an Investigation
DD to E01 Conversion
When responding to high-severity incidents in the cloud, having the ability to confirm forensic findings with multiple tools is important. To this end, users can now convert a disk image from DD/Raw format to E01 format (Expert Witness Format). E01 is an industry standard for storing forensic images. This feature can be enabled in Settings within the Cado platform. Users can select “Convert DD to E01” upon evidence capture or fully automate the conversion via API. The E01 format file will be stored in S3 storage. You can also now centrally preserve all forensic collections from all clouds and formats into a central S3 bucket.
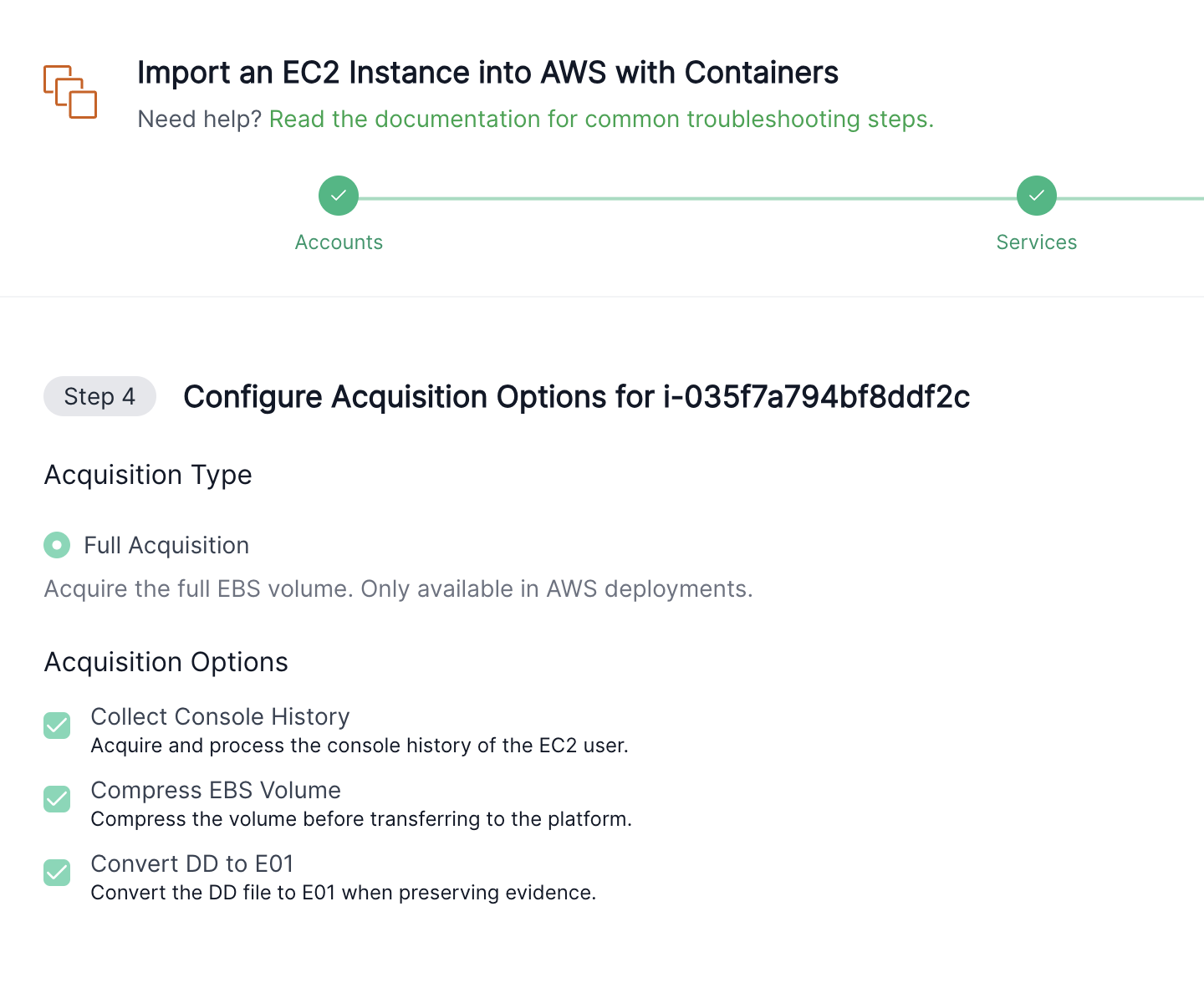
Converting DD to E01
Project Overview Dashboard
Cado’s new Project Overview Dashboard allows security teams to get an at-a-glance view of open projects. The dashboard displays a timeline of investigation and response actions, including project milestones such as open date and data acquisitions. The dashboard also summarizes key project findings by displaying the top MITRE categories, count of malicious and suspicious activities, and number of compromised assets and roles.
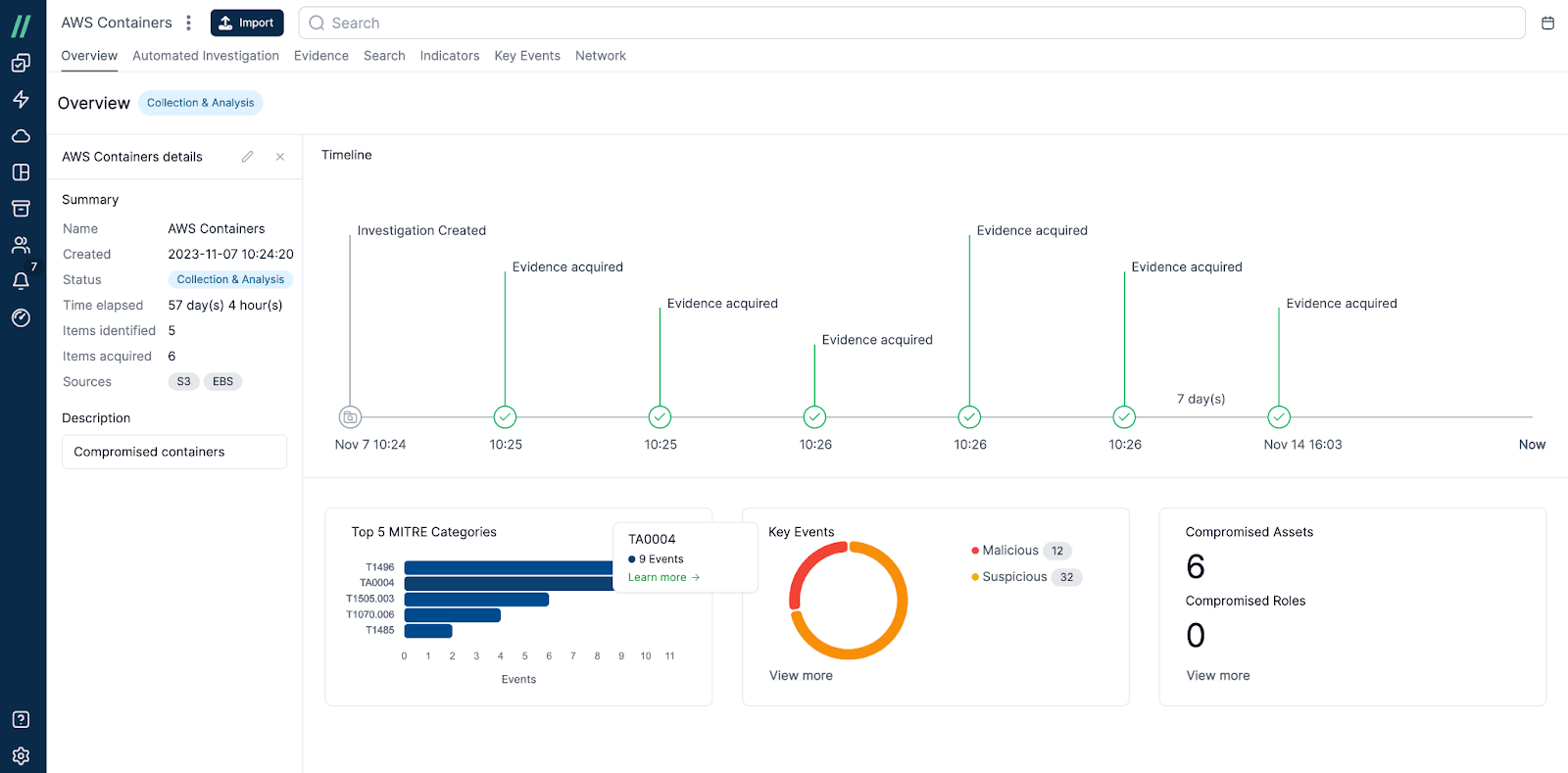
Cado's Project Overview Dashboard
Proxy Support
Cado now supports the ability to specify the URL for the proxy at deployment. This allows the Cado platform to function in environments where proxies are used for outbound communication.
New Evidence Overview Tab
Cado’s Evidence Overview tab has undergone a refresh this quarter to deliver an improved user experience. From card layout to a tabular view, security teams can more easily understand the source of the data and filter and sort to gain additional context, such as number of key events per data source and more.
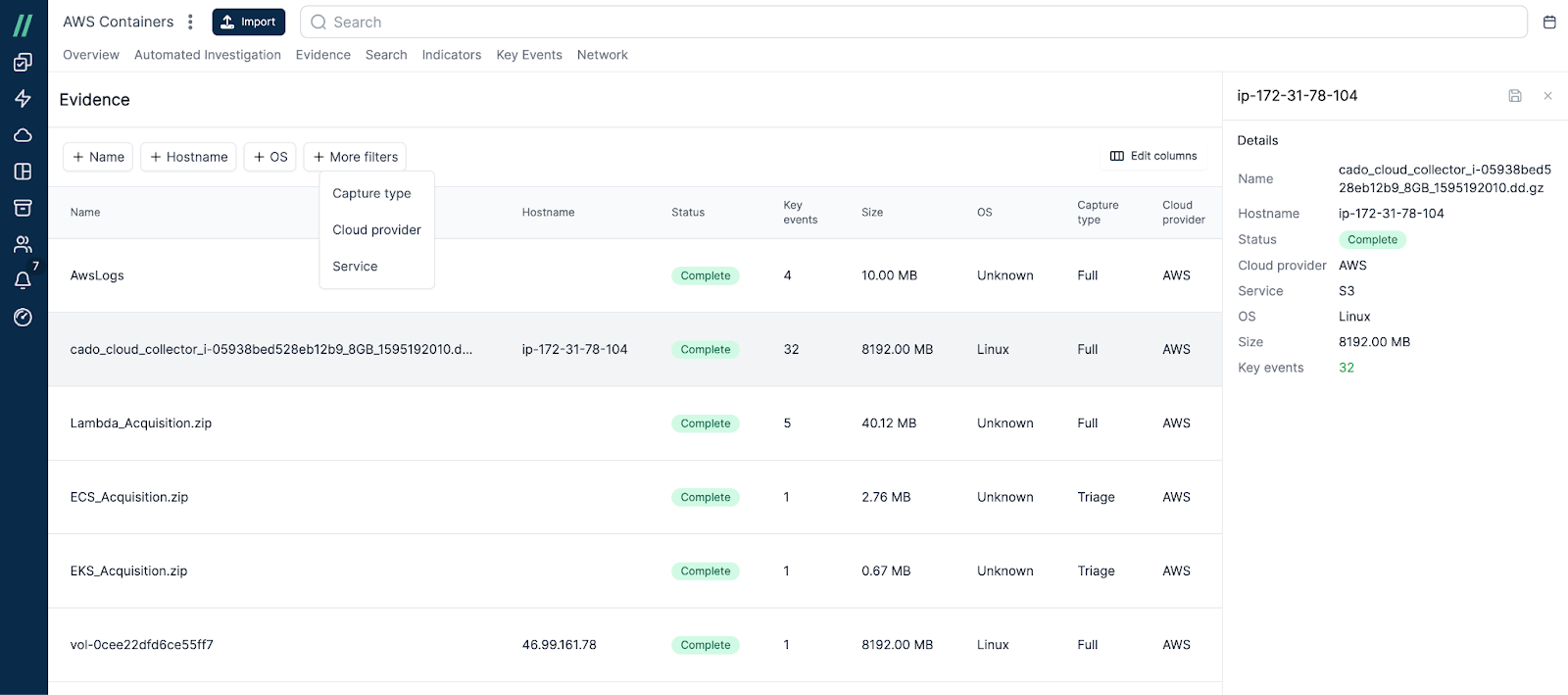
Cado's Evidence Overview Tab
Azure Triage
Azure support has now been added to the Cado platform's triage capture capability. Cado’s triage capture capability is a faster alternative to full disk capture, trading depth for speed. This feature is often used by security teams when they need to quickly validate the scope of an investigation. In this case, security teams can perform a triage capture across a larger number of machines to validate whether or not there are signs of malicious activity before performing a full disk capture. This feature helps security teams speed up investigations and reduce MTTR in Azure environments. Cado Security's Azure triage capture package of forensic evidence includes:
- All system logs, including application and authentication logs
- Master File Table to understand what files were where in the system
- Configuration files and registry to show how the system was set up
- Volatile data at the time of capture, including data about running processes and memory of running processes
- Web histories to understand which web URLs were accessed
- Active network connections
Incident Readiness Dashboard Enhancements
In October last year, Cado launched its Incident Readiness Dashboard to enable security teams to take a more proactive approach to incident response in the cloud. The Incident Readiness Dashboard delivers the ability to proactively run readiness checks, see readiness trends over time, and identify and mitigate any issues that could prevent an organization from rapidly responding to active threats. Since its initial release, we’ve made a number of user interface improvements to further enhance the experience of interacting with the readiness feature set.
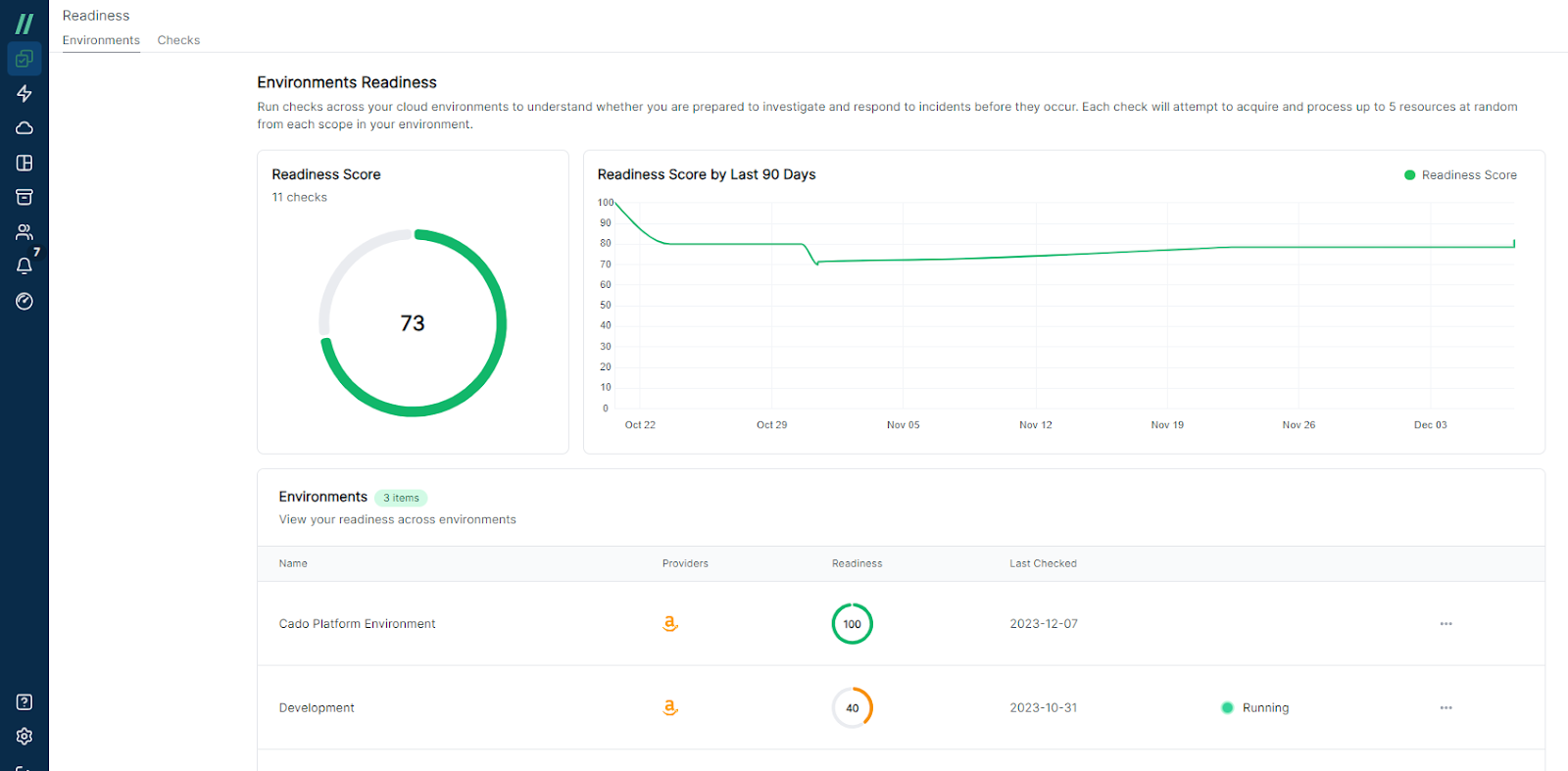
Cados Incident Readiness Dashboard
Cross Cloud Support Enhancements
With a large percentage of organizations adopting a multi-cloud strategy, having the ability to seamlessly capture and investigate forensic evidence across multiple Cloud Service Providers (CSPs) is key to a robust incident response strategy. Cado Security has extended its cross-cloud support even further this quarter, with the ability to now natively deploy the Cado platform in GCP with the ability to collect and analyze data from AWS and Azure. This rounds out Cado’s overall offering with greater support across the top three CSPs. To recap, Cado customers can now choose from the following multi-cloud set ups:
- Native deployment within AWS with the ability to acquire evidence from Azure and GCP
- Native deployment within Azure with the ability to acquire evidence from AWS and GCP
- Native deployment within GCP with the ability to acquire evidence from AWS and Azure
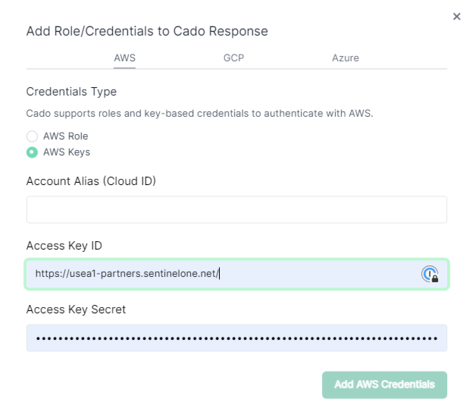
Adding Cross-Cloud Accounts in the Cado Platform
Automation Rule Enhancements
Cado’s in-product automation rules empower security teams to automatically perform collection and remediation actions based on various triggers. Automation rules empower security teams by eliminating the lag time between incident detection and investigation, thus significantly reducing response times. Most recently, Cado has added two new trigger options, the ability to trigger automated acquisition based on GuardDuty rule Severity, and the ability to trigger automated acquisition based on GuardDuty rule ThreatPurpose. These enhancements aim to give security teams more control over their automated incident response process. Further, the ThreatPurpose trigger also allows for alignment with the MITRE framework.
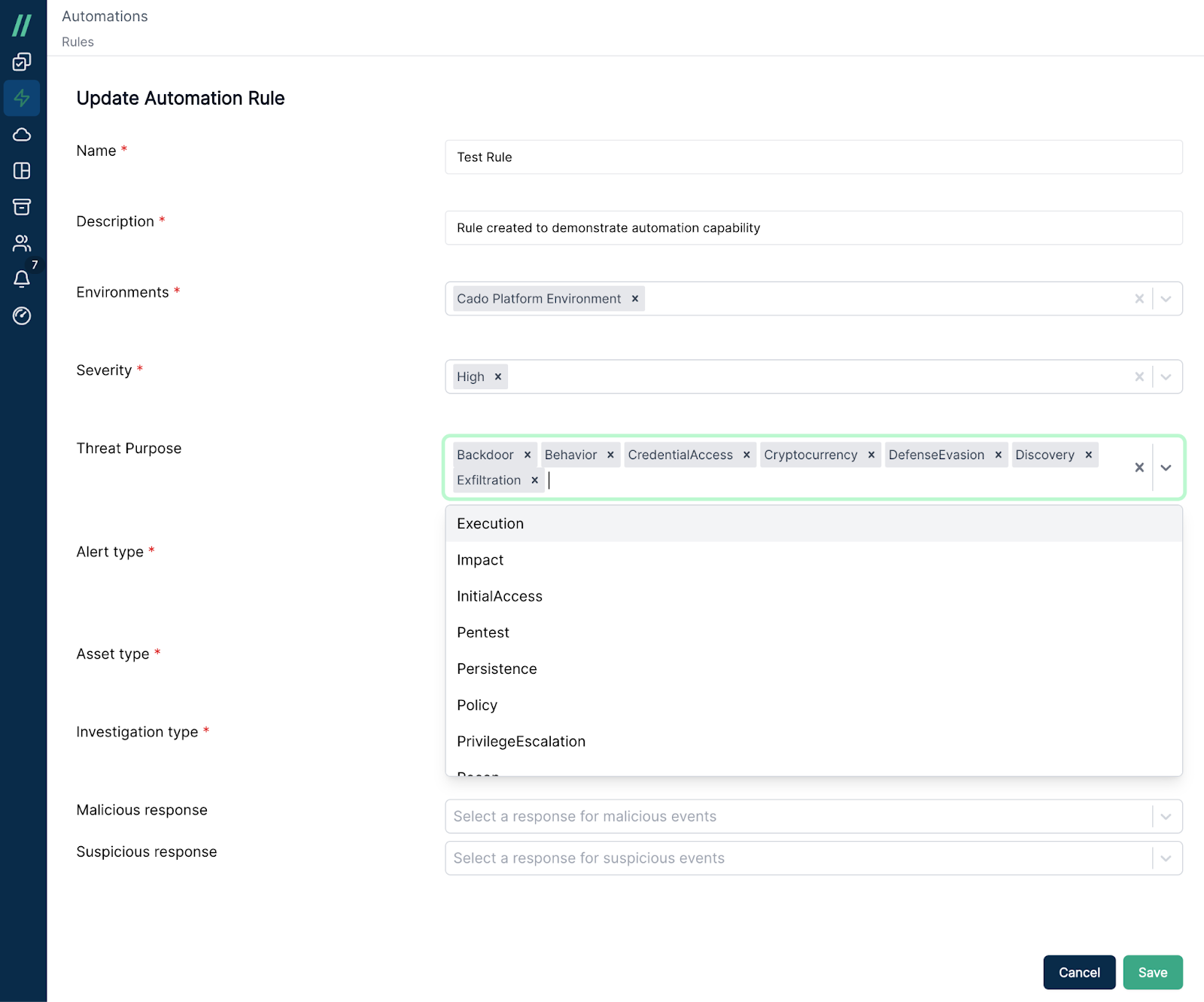
Creating Automation Rules in the Cado Platform
We look forward to hearing from our customers, free trial, and community users -- let us know what you think about these new capabilities! As we move into the next quarter, we remain fully committed to developing features that will empower our customers to do their best work. Stay tuned for more exciting updates soon!
If you are interested in getting a more detailed look into what Cado has been up to, contact our team to see a demo.
More from the blog
View All Posts

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

