When it comes to forensics investigations, the concept of Chain of Custody is important in ensuring the integrity of evidence, as well as its reliability and admissibility in legal proceedings. However, within the complex cloud landscape, maintaining an unbroken chain of custody introduces new challenges that demand innovative solutions.
Understanding Chain of Custody
Chain of custody records and tracks the custody, control, transfer, and analysis of evidence. It's a paper trail detailing every interaction and access to the evidence, providing absolute assurance of its security and integrity. This documentation is vital in ensuring the admissibility of evidence in legal contexts.
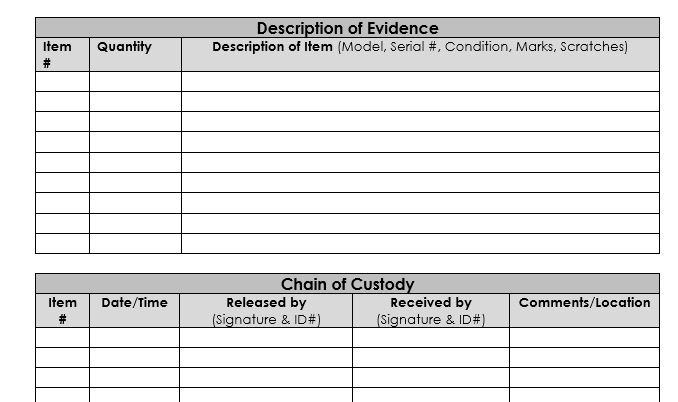
Traditional chain of custody form. Source: NIST
The repercussions of a broken chain of custody can be significant. Inadequate documentation can render collected evidence inadmissible, undermining the entire investigative process and potentially nullifying its use in legal proceedings. Additionally, evolving global reporting mandates are underlining the importance of maintaining an unbroken chain of custody from the outset of any investigation.
Unique Challenges in the Cloud
The cloud environment introduces a multitude of access points to data and resources, significantly complicating the preservation of an unbroken chain of custody. Unlike traditional environments with limited access, cloud landscapes involve various entities—users, third parties, and cloud service providers—accessing data, intensifying the challenge of preserving this chain.
Moreover, the prevalence of multi-cloud strategies further complicates the scenario. Evidence may span multiple cloud platforms and regions, amplifying the complexity of maintaining chain of custody.
Cado Simplifies Chain of Custody
At Cado, we understand the importance of and complexities associated with maintaining chain of custody in cloud environments. To this end, the Cado platform delivers the following capabilities to simplify the process:
- Autonomous chain of custody: In the Cado platform, chain of custody is handled completely autonomously behind the scenes, and does not require any input from the user. This saves analysts time, enabling them to focus on the investigation itself as well as mitigates the risk of human error and ensures compliance with legal requirements by consistently recording and safeguarding evidence.
- Multi cloud support: Cado addresses the challenges posed by multi-cloud environments. Wtih cross-cloud support across AWS, Azure and GCP, enabling the preservation of unaltered evidence in complex environments.
- Centralized preservation: The Cado platform supports the ability to designate a centralized S3 bucket for evidence storage and preservation – even if the evidence is acquired across multiple cloud platforms. By centralizing evidence, security teams only have to manage access to one bucket. This approach enables organizations to minimize the audit trail, which massively simplifies and streamlines chain of custody and ultimately reduces the risk of unauthorized access.
- Standard compliance: To ensure that the whole process stands up to scrutiny, under the hood Cado uses DD, an industry standard and recognized tool, to facilitate the transfer and storage of evidence, as well as the industry standard SHA-256 to ensure evidence is unaltered.
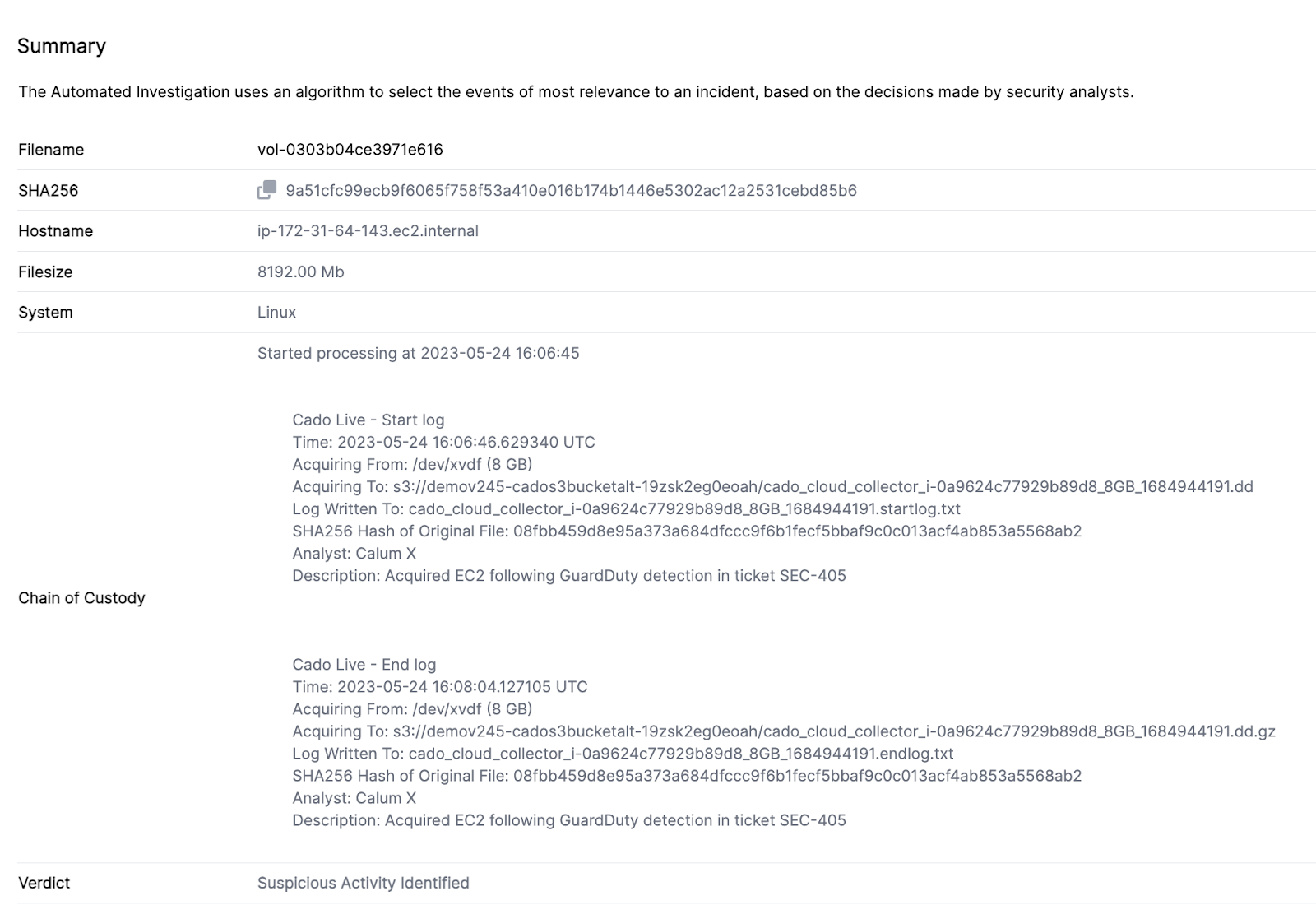
Chain of custody in the Cado platform
Cado logs the entire data collection process, recording the unbroken chain of custody needed to prove the authenticity of any evidence collected. The platform logs the time the evidence processing began, where the evidence was acquired from, and its size. From there, the solution logs where the evidence is being stored.
Interested in ensuring chain of custody in your cloud environment? See how Cado streamlines cloud forensics and incident response processes. Contact us to schedule a demo today.

