What is Chain of Custody?
Chain of custody records the custody, control, transfer and analysis of evidence. It's an important concept in the world of forensics and investigation. Simply put, it consists of two parts: a paper trail that shows everyone who’s interacted or accessed the evidence, what they did, and where it was stored; and secondly, it provides absolute assurance that nobody else accessed the evidence. In order to allow the evidence to stand up to scrutiny, the chain must be unbroken.
Let’s walk through a basic example:
- An analyst captures a disk image of a compromised machine and stores it securely
- It is then accessed by a different forensics expert who, after examining the disk, generates more evidence such as a malware sample. They then add the new additional evidence to the secure storage
- The evidence then remains securely stored until needed with associated logs
In this example, chain of custody allows us to know:
- Who accessed and interacted with the evidence at each step of the process
- That the evidence was stored securely and no one else has accessed it
Why is Chain of Custody Important?
Chain of custody becomes extremely important in the context of legal proceedings. In court, companies have to guarantee that any evidence they provide is valid throughout its whole lifecycle – from collection and analysis to preservation and access. For a chain of custody to be valid, there must be adequate and demonstrable data protection, access control, altering, monitoring, and logging.
Chain of Custody in the Cloud
There are a number of differences when it comes to performing investigations in cloud environments versus investigations in traditional on-premises environments which have become quite apparent with the rapid shift organisations have made to the cloud.
Chain of custody, for example, is much more complex in cloud environments, given the number of people who may have access to the evidence: users, third parties and the cloud provider themselves all have access to the data. When performing investigations in the cloud, it is important to preserve unaltered copies of the data and ensure records of its integrity by hashing.
Chain of custody documentation has yet to adapt to a cloud-based world. In a traditional investigation, there is both physical evidence, such as a computer or hard drive, and all the data contained within this physical hardware. On the other hand, in the cloud, there is only data, and this makes maintaining the chain of custody much more complicated.
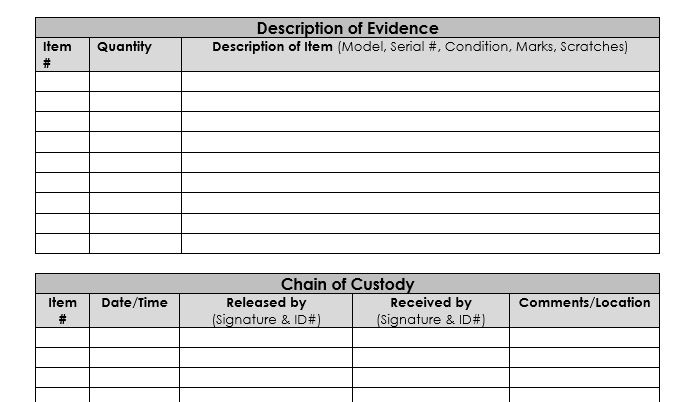
Traditional chain of custody form. Source: NIST
In an on-premises investigation, an analyst would take a copy of the data on the physical media for analysis purposes, so in the event the data needs to be verified (as to its authenticity), it can be compared back to the original copy.
In the cloud, cloud resources and data can span multiple regions and multiple cloud platforms. This means we have to take a different approach. We need to copy the evidence to a secure location to log who has access to the data and use hashing to ensure its integrity throughout the investigation.
There are a number of native tools that you can use to help establish chain of custody when working in the cloud:
Azure
- Azure Activity Logs can be used to record and monitor any activities inside a given environment
- Azure Role-Based Access control can be implemented to manage permissions and access
- Azure Blob storage has access tiers, immutability and server-side encryption to help with evidence storage and preservation
AWS
- AWS CloudTrail allows you to log all activities in your cloud environment
- S3 object versioning and server encryption can be used to preserve evidence
- AWS Identity and Access Management (IAM) enables organisations to control access and permissions
GCP
- GCP audit logs monitor and record activities in the GCP environment
- GCP Identity and Access Management (IAM) enables organisations to control access and permissions
- Google Cloud Key Management Service can be used to manage encryption keys for data stored in GCP services
Streamlining Chain of Custody with Cado
In the Cado platform, chain of custody is handled completely autonomously behind the scenes, and does not require any input from the user. This saves analysts time, enabling them to focus on the investigation itself.
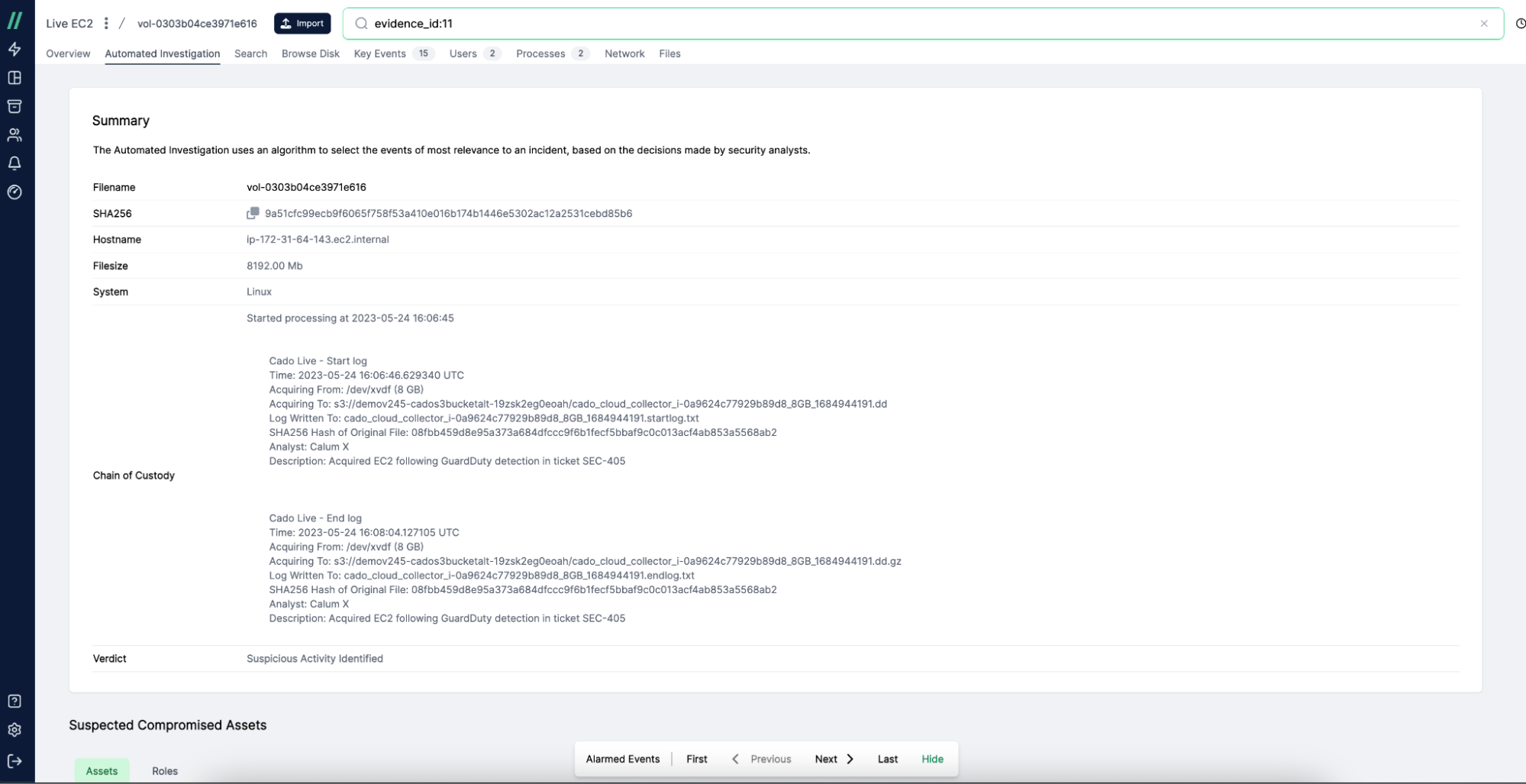
A screenshot showing evidence collected by the Cado platform.
The integrity of all data collected is ensured via a SHA-256 hash and it is stored securely in an S3 bucket alongside the evidence.
The Cado platform supports the ability to designate a centralised S3 bucket for evidence storage and preservation – even if the evidence is acquired across multiple cloud platforms. By centralising evidence, security teams only have to manage access to one bucket. This approach enables organisations to minimise the audit trail, which massively simplifies and streamlines chain of custody and ultimately reduces the risk of unauthorised access.
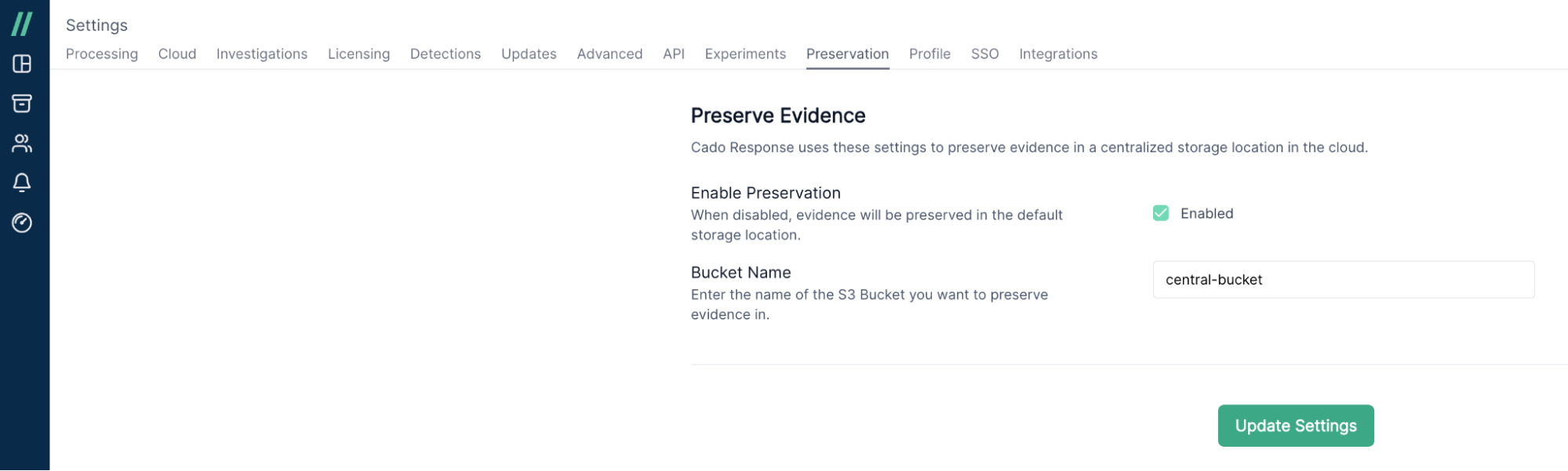
Preserve evidence in a centralised bucket with Cado.
As you can see, Cado logs the entire data collection process, recording the unbroken chain of custody needed to prove the authenticity of any evidence collected.

A detailed look at the chain of custody recorded in Cado.
The platform logs the time the evidence processing began, where the evidence was acquired from (in this case: /dev/xvdf), and its size (in this case: 8 GB). From there, the solution logs where the evidence is being stored.
The Cado platform also tells the user where the logs of the data transfer have been stored, and a SHA-256 hash is generated to ensure the integrity of the evidence. Finally, the platform records the analyst who initiated the capture and a description of the evidence.
To ensure that the whole process stands up to scrutiny, under the hood we use DD, an industry standard and recognized tool to facilitate the transfer and storage of evidence, as well as the industry standard SHA-256 to ensure evidence is unaltered.Interested in implementing chain of custody into your cloud environment? Or streamlining your current forensics and incident response processes in the cloud? Contact us to schedule a demo with our team or check out our 14-day free trial.

