Cado Security recently delivered its second Cloud Threat Findings Report, detailing recent discoveries by the Cado Security Labs team over the last six months. The report findings are based on real-world techniques seen in the wild by attackers targeting cloud environments. This blog outlines some of the key findings from the report.
Key Report Findings
Attackers continue to exploit web-facing services in cloud environments
A common theme in the malware campaigns the Cado Security Labs team has reported on over the past six months is the exploitation of various web-facing services to achieve initial access in cloud environments. This includes services like Docker, Redis, Kubernetes, and Jupyter, all of which are frequently deployed in the cloud. It has become increasingly evident that attackers have developed advanced technical knowledge of how these services are deployed and how to exploit them. An example of an emerging malware campaign targeting Jupyter Notebooks is Qubitstrike, which was discovered in October 2023.
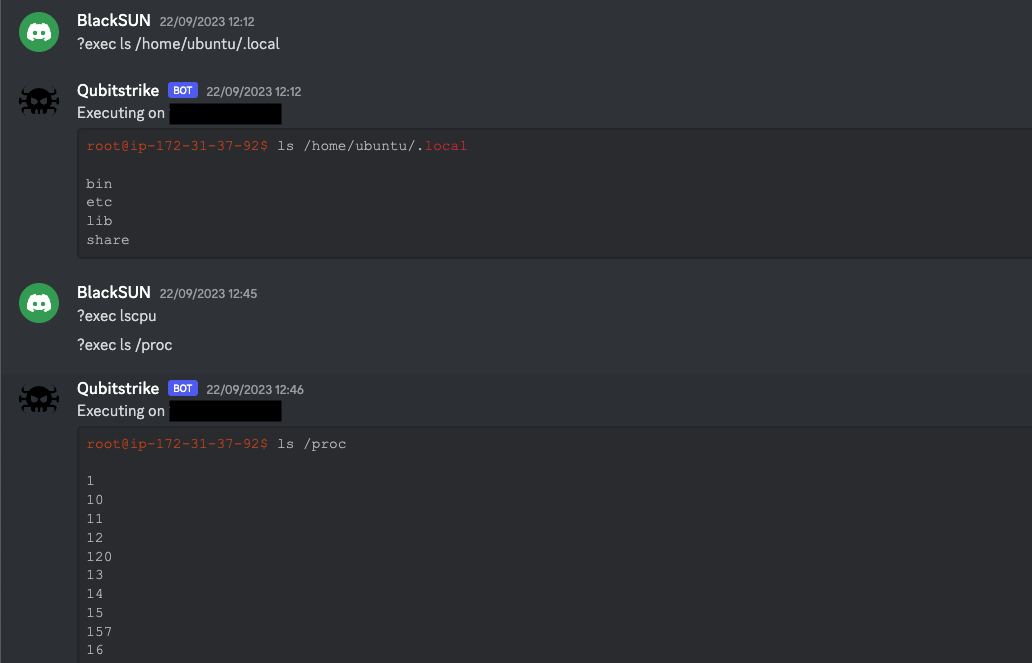
Qubitstrike utilizing Discord for C2 Operations
Cryptojacking is no longer the sole focus of cloud attackers
The vast majority of cloud and Linux campaigns the Cado Security Labs team analyzes involve hijacking resources for mining cryptocurrency, usually Monero. While crypto-jacking is a very real and significant threat, The Cado Security Labs team has started to see a diversification in objectives displayed by recent Linux and cloud malware campaigns. One such campaign that demonstrates this is Legion, a cloud-focused hack-tool written in Python. Legion was first discovered in April 2023 and its primary objective is to automate the hijacking of various cloud SMTP services, to carry out mass-spamming attacks.

Splash screen for the legion Malware
Rust malware continues to proliferate
Modern compiled programming languages, like Rust and Golang, offer several benefits to malware developers, such as allowing them to compile for multiple operating systems and architectures, without having access to the operating systems or architectures themselves. In last year’s cloud threat findings report, the Cado Security Labs team discussed the emerging trend of ransomware developers targeting Linux systems, a trend aided by the ease with which modern compiled programming languages allow cross-platform development. Recent cross-platform ransomware campaigns, such as Blackcat, have utilized Rust for their primary payloads. We’ve also seen Rust leveraged in other recently discovered non-ransomware campaigns, such as P2Pinfect.
Who is Cado Security Labs?
Cado Security Labs, the research and development division of Cado Security, conducts industry-leading intelligence and cloud security research. By analyzing the cloud threat landscape, the team drives innovation within the Cado platform and delivers novel findings to the security community to enable security professionals to better handle complex attacks targeting cloud infrastructure.
The team's research forms the basis for valuable resources such as technical playbooks, cheat sheets, and blog posts, empowering the security community with up-to-date knowledge of emerging trends and tactics being depleted by attackers.
Cado Security Labs conducts in-depth malware analysis, documenting behaviors and indicators for use by security professionals.
These are just some of the many findings detailed in Cado's latest threat report, to find out what other findings the Cado Labs team has brought to light over the past six months you can download the full report here. And if you want to see how Cado is helping global organizations implement an IR program for the cloud and what it can do for your organization schedule a demo with one of our team.

