There are plenty of cloud comparisons out there, but there is still a debate on which platform is more secure. As in life, there are pros and cons to everything. Here’s what our security experts think of each platform:
Amazon Web Services (AWS) and Microsoft Azure are both reputable and reliable cloud platform vendors that have served some of the largest companies across the globe for nearly a decade. Most importantly, as the appetite for cloud has continued to grow, security has remained a core value of each. Over the years, AWS has built a strong ecosystem of third-party developers and security vendors, allowing customers to customise the solution based on their unique needs. Azure also supports various integrations, although Microsoft has heavily invested in building their own security tool set.
Let’s further explore the benefits of each platform across three key areas of security: access management, threat detection and threat response.
Access Management
The core of Amazon Web Services (AWS) identity and access management is AWS IAM, which was designed from scratch back in 2011. Since its inception, the company has continuously evolved its IAM capabilities. Ten years ago, IAM started with relatively fine-grained access controls by reducing bad practices such as root user accounts and long-term access keys. Today, AWS IAM now authorises over 400 million API requests every second, and offers extremely fine-grained access controls.
On the contrary, Microsoft Azure Active Directory can be a great option for those who are already familiar with the Microsoft product suite. In terms of ease of use, this can simplify operations as it allows security to be managed from a central location. Further, from a cost perspective, it is only natural that Microsoft customers lean towards adopting additional Microsoft capabilities that may already be included in their current licensing.
Threat Detection
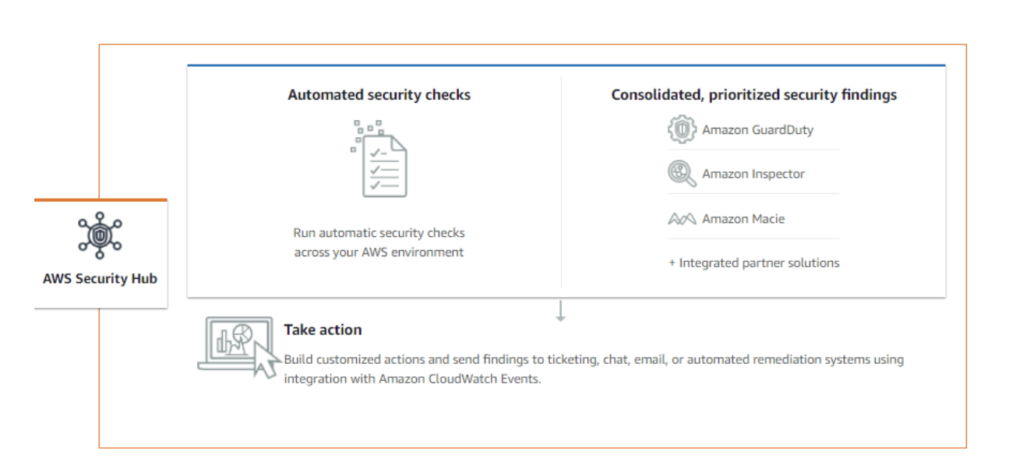
From a threat detection perspective, Amazon Web Services (AWS) offers GuardDuty which primarily focuses on network-based detections and is effective in detecting some of the most common attacks. In addition, AWS offers a solid ecosystem through their Security Hub to provide its customers with the option to adopt additional cloud protection capabilities.
Alternatively, Azure offers a centralised toolset for monitoring and responding to threats. Microsoft is making a big push to the “automated SOC” and has delivered orchestrated integrations between their various detection and response tools. Controls such as Defender ATP have proven effective, but may require extra budget unless you are already on an E5 license.
Threat Response
And finally, Cado’s bread and butter, forensics and incident response. What do you actually do once you’ve detected an attack and need to identify the root cause?
Behind the scenes, AWS is built to stop the most common causes of cloud breaches. For example, if you accidentally push your access keys to Github, AWS will proactively detect and stop this in an effort to prevent exploitation.
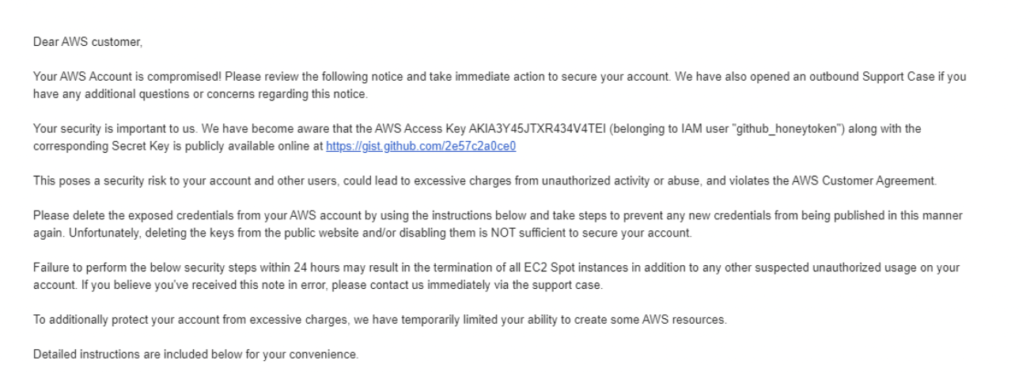
A screenshot of the AWS automated compromised key detection (we tested the AWS compromised key detection by posting a honey-token to Github)
However, acquiring forensic copies in AWS can be challenging. It’s a manual process, requiring security teams to take roughly 20 steps. Further, if you intend to acquire third-party disks on your network, or data cross-account, the process can be even more time intensive.
Microsoft makes it slightly easier to obtain a disk image by providing a simple link for download. However, in either service, once you’ve downloaded the disk images and are ready to investigate, you are left on your own. Rather than the modern cloud-based security tooling you may be used to, you are presented with classic, outdated forensic desktop application tools that don't scale.
The Bottom Line
The good news is whether you’re on AWS, Azure or some combination of both, you can easily investigate threats with a cloud-native digital forensics platform like Cado. We take the complexity out of cloud investigations so security teams can focus on what matters most.