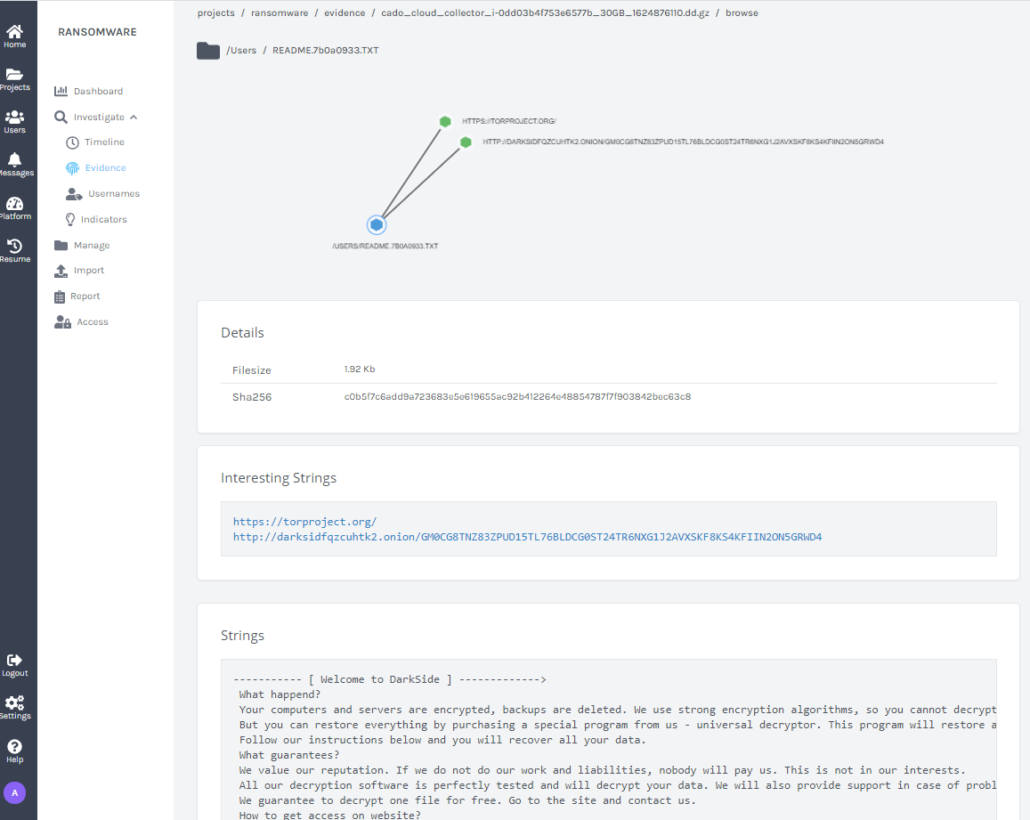
One thing you may have not realised about ransomware is that it's not immediate. While the data encryption process itself is painfully rapid, targeted ransomware attacks generally take place over a longer period of time. Sophisticated hackers take their time to ensure their efforts are as lucrative as possible. To do so, they learn the ins and outs of their victim’s environment and meticulously map out how they can make the most impact. They learn where the servers are and the data backups live.
Two Weeks To Ransom
Today, almost every targeted ransomware attack starts with an initial spearphishing compromise, followed by the installation of CobaltStrike malware. Then the attackers spread across their target’s network with the goal of deploying the ransomware across as much of the environment as possible.
The ransomware operators themselves are quite open and honest about how their successful business model operates by providing a “free pen-test” report after their target pays the ransom:
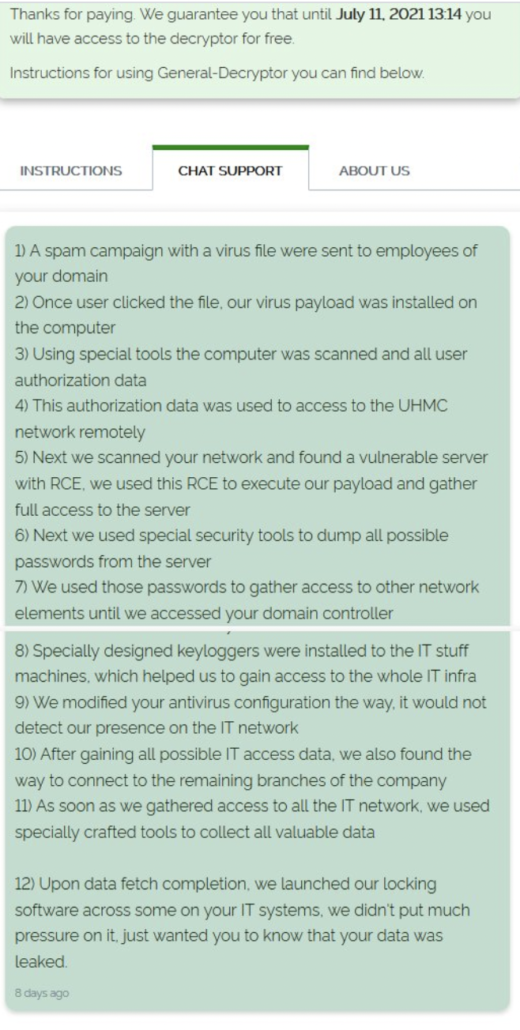
executed to successfully ransomware one of their targets.
As you can see from the 12-step example above, these attacks take time. We typically see that it takes approximately two weeks from first access to ransomware execution (see e.g. 1, 2, 3).
The good news is that with the right investigative tools in place, organizations have a critical window of opportunity to shut down the attack before the ransomware has a chance to detonate. Let’s take a closer look at how forensics can help organizations take down the attackers before the ransom.
When You Get an Alert for CobaltStrike
When you get an alert for CobaltStrike in your Security Operations Center, the clock starts ticking.
It’s important to stress that the compromised machine should not be wiped by default prior to conducting a detailed investigation. Wiping the machine will make the possibility of stopping the ransomware attack unlikely. In order to understand how the attackers got in, and more importantly, if they have moved laterally or stolen data, a full forensics investigation is required. First, we want to check if this is patient zero and if there is evidence of a spearphish. If so, it’s important to understand if other users have received similar messages and investigate and block those messages accordingly.
Lateral Movement
It’s extremely critical to check for signs of lateral movement as it’s very likely that the attackers have migrated to other systems in the environment. Once inside the network, attackers typically live off the land, leveraging stolen passwords and legitimate admin tools to move to additional workstations and eventually servers. These methods make the attack even more difficult to detect using traditional controls, so it’s important to dive deep into the data to understand the full scope. Relying on automated alerts and detections alone in this situation is not enough. Have you checked for connections to other systems surrounding the initial compromise? Are there signs of password dumping tools on the system? Did the user store plain text passwords on the compromised system? From here, there will likely be certain remediation steps that can be taken, such as resetting potentially compromised passwords.
Data Theft
A new technique ransomware gangs have recently started employing is exfiltrating data, in addition to deploying the ransomware itself. This doubles the attacker's chances that the victim will pay the hefty ransom they’ve requested. If you have the ability to monitor for significant upticks in traffic leaving your network, this can be a warning sign. In addition, large amounts of company data sitting in unexpected folder locations or large zip archives of company documents sitting on publicly accessible web-servers can indicate staging for data exfiltration.
“T Minus One” a.k.a. “Mimikatz on the Domain Controller”
Finally, the attacker will find a way to deploy the ransomware across the organisation at scale. For this stage of the attack, it’s important to pay particular attention to any unusual activity on domain controllers or servers that are used to deploy software or patches across the estate.
If You’re Too Late…
Unfortunately, most ransomware investigations start after the ransomware has been deployed. However, there are still important actions you can take to mitigate the damage to your business and expedite recovery. Stay tuned for a blog dedicated to ransomware investigations post breach.