When it comes to measuring the performance of your Security Operations Center (SOC) a key metric that should be taken into account is Mean Time To Respond (MTTR) – the average time it takes for your SOC to resolve a security incident.
Why is MTTR Important?
The longer an attacker is active in your environment, the more the potential cost of a breach is to your business.
Crowdstrike talks about a 1-10-60 rule, where you need to detect an incident within a minute, contain it within 10 minutes, and eradicate it within 60 minutes. Outside of that, once the attacker “breaks out” and is able to move laterally then it becomes exponentially more expensive to contain, both in terms of remediation effort and impact on the business.

What Does This Metric Actually Tell Us?
If you find that your SOC has a high MTTR, it's likely that you need to make changes to your incident response procedures. This could involve streamlining your procedures or investing in new tools that will help your team resolve incidents more quickly.
In a cloud world, exponentially higher scale and rate of change mean that your approach to MTTR needs to evolve. Common reasons organizations have a high MTTR include:
- Access to cloud resources are managed by another team: In many large organizations, there are dedicated cloud teams that manage and operate the cloud infrastructure. Sometimes, these teams are even outsourced adding another layer of complexity and required support. As the owners of the cloud infrastructure, these teams typically require a security professional to open a ticket to request permission to a cloud resource. This frustrating additional task significantly slows down investigation and response.
- You’re using legacy incident response solutions: Today, when a cyber incident occurs in the cloud, security teams often have little choice but to resort to traditional/open-source tools. However, these tools weren’t designed for dynamic cloud environments – this is evident with every step of the process from collection to analysis (and the level of difficulty significantly increases in multi-cloud environments). Without cloud-specific incident response solutions, responding to threats is extremely complex, manual and time consuming.
- Ephemeral means data disappears in the blink of an eye: One of the biggest challenges security teams face is securing ephemeral environments consisting of container-based and serverless resources. These resources spin up and down continuously making it almost impossible for security experts to investigate an incident and understand which assets and data have been compromised. If malicious activity occurs between the time one of these resources is spun up and down, that data is lost forever.
How Can Cado help?
Cado helps security teams lower MTTR by taking a proactive approach to incident response. With the Cado platform you can:
- Define accesses to your cloud environments ahead of time so that when an incident occurs your Incident Response team can get the data they need when they need it
- Set up automation rules so that when a detection system like AWS GuardDuty, or an XDR like SentinelOne triggers an alert, you can automatically collect the data you need - up to and including a full disk and memory image of the affected system
- Quickly process and analyze VMs, containers and serverless functions to get a full picture of what went on.
Cado’s new Automated Investigation tab gives security teams a summary of what happened, and also lets analysts see which cloud assets have been compromised.
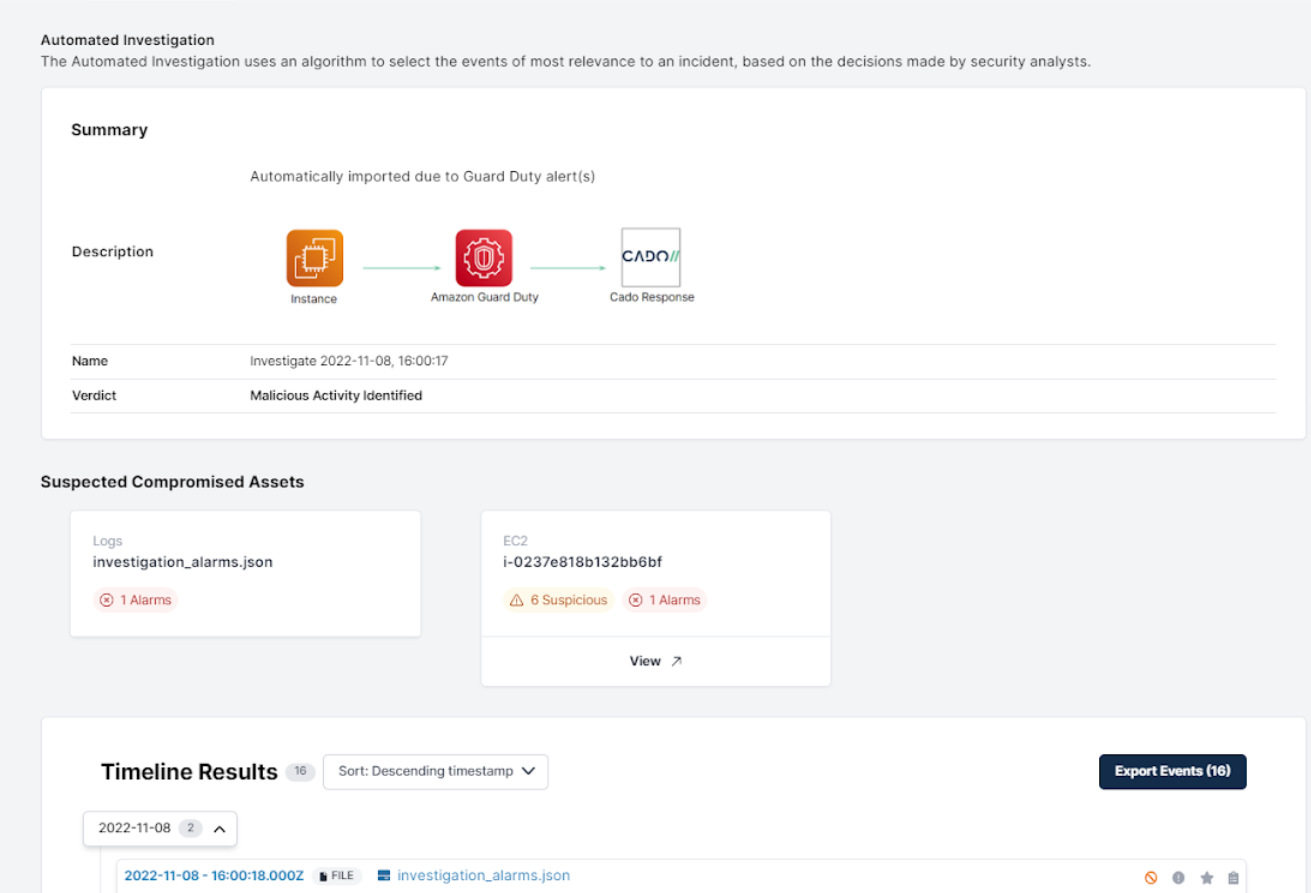
What’s more, for cloud instances that have been acquired, analysts can:
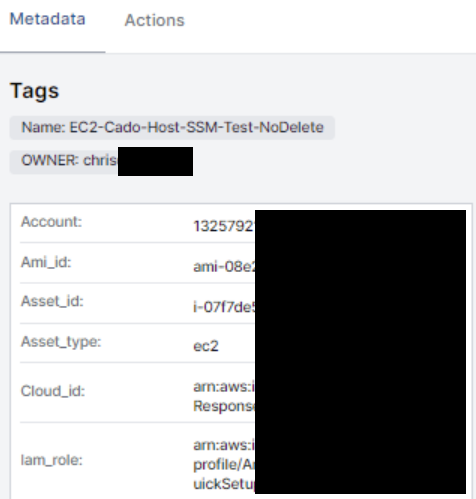
View Cloud Asset Context: Cado automatically displays the metadata associated with the compromised asset, including its role, tags, region, IP address etc, giving security analysts the context they need to understand more about the asset and inform next steps.
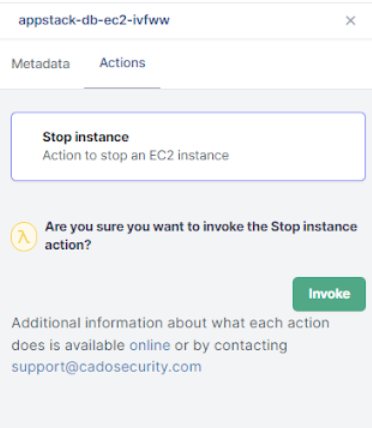
Take Single Click Response Actions: With Cado, security analysts can take response actions against a compromised asset, such as shutting the instance down, directly from the Cado application
By automating and streamlining the end-to-end incident response process – from data capture to processing and analysis, Cado empowers security teams to exponentially reduce the time it takes to investigate and and respond to an incident, lowering the risk to the business and raising the credibility of your security team.
Interested in seeing how other organizations are benefiting? Contact us to see a demo or check out our 14-day Free Trial.

