Recently VX Underground released a toolset they report is from the Conti and BlackMatter ransomware gang:
As TeamTNT themselves pointed out, it’s not clear if they have seen these tools abused in the wild.
At Cado, we’re always a fan of researching the latest cloud and container malware - so we decided to dive in and take a closer look. VX Underground have kindly made the files public, which the ransomware groups “modify ... to deploy ransomware and distribute them amongst affiliates”.
It contains the same scripts we've seen many times before which have been used to:
- Steal credential from AWS, Docker, and Kubernetes
- Install Xmrig mining malware
- Post compromise Weavescope installations
These files are identical to the ones we (and other researchers) pulled from the following domains in August and September 2021 (they do not show any signs of customization):
- http://45.9.148[.]182
- http://teamtnt[.]red
- http://chimaera[.]cc
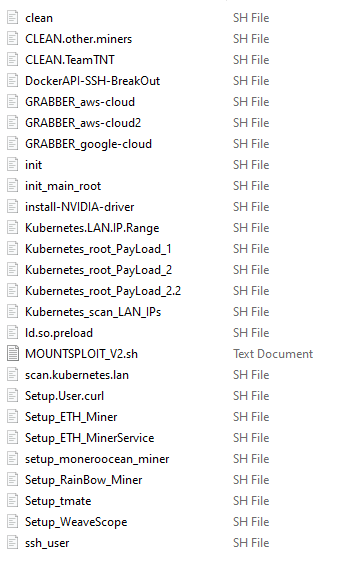
In particular, they match files previously identified by 1ZRR4H and grabbed by the user r3dbU7z on Twitter.
When vulnerabilities are discovered there is a typical process of first being used by malicious miners, then by the more serious ransomware gangs. We wouldn’t be surprised to see that same happening with TeamTNT’s arsenal of cloud and container attack scripts - but we also haven’t seen any direct evidence of that yet.
We’ll be talking about some novel cloud and container attacks at BlackHat Europe this week! Visit our booth # SU5 and register for our briefing session:
They Hacked Thousands of Cloud Accounts Then Sent Us Weird GIFs
- Virtual session: Wednesday, November 10 | 3:20pm-4:00pm
- In-person session: Thursday, November 11 | 1:30pm-2:10pm (Room BC, ICC Capital Suite 12, Level 3)

