A match made in heaven, cloud computing and DevOps provide the scalability, accessibility, and automation required to implement new software at cloud-speed. Prototypes can be developed in just weeks, versus months or years. Sounds like a dream, right? It would be – if cyber security had kept pace with the speed of innovation.
Cloud Breaches are Hard
Today, when a cyber incident occurs, security teams often have little choice but to resort to their existing detection platform in an attempt to piece together what happened. But, these tools weren’t designed for a dynamic cloud environment encompassing virtual machines, containers and serverless environments. This means security teams often respond to an incident without understanding its full scope and they leave elements behind that attackers can leverage. For example, recent research shows 80% of Ransomware victims that pay out are attacked again. This is happening because security teams aren’t conducting a proper and thorough investigation to completely remove an attacker's access.
Automating Cloud Forensics & Incident Response
To adequately manage risk in today’s cloud-first world, security teams require deep visibility across the next generation of technology. This is where automation comes in. While getting forensic data in the cloud may seem like a daunting task, cloud providers now make a range of automation options available, and it is these automation techniques that make it possible for security teams to effortlessly dive deep. With visibility beyond what a detection platform can provide, security teams are able to make more informed incident response decisions – and therefore, better manage risk across modern environments.
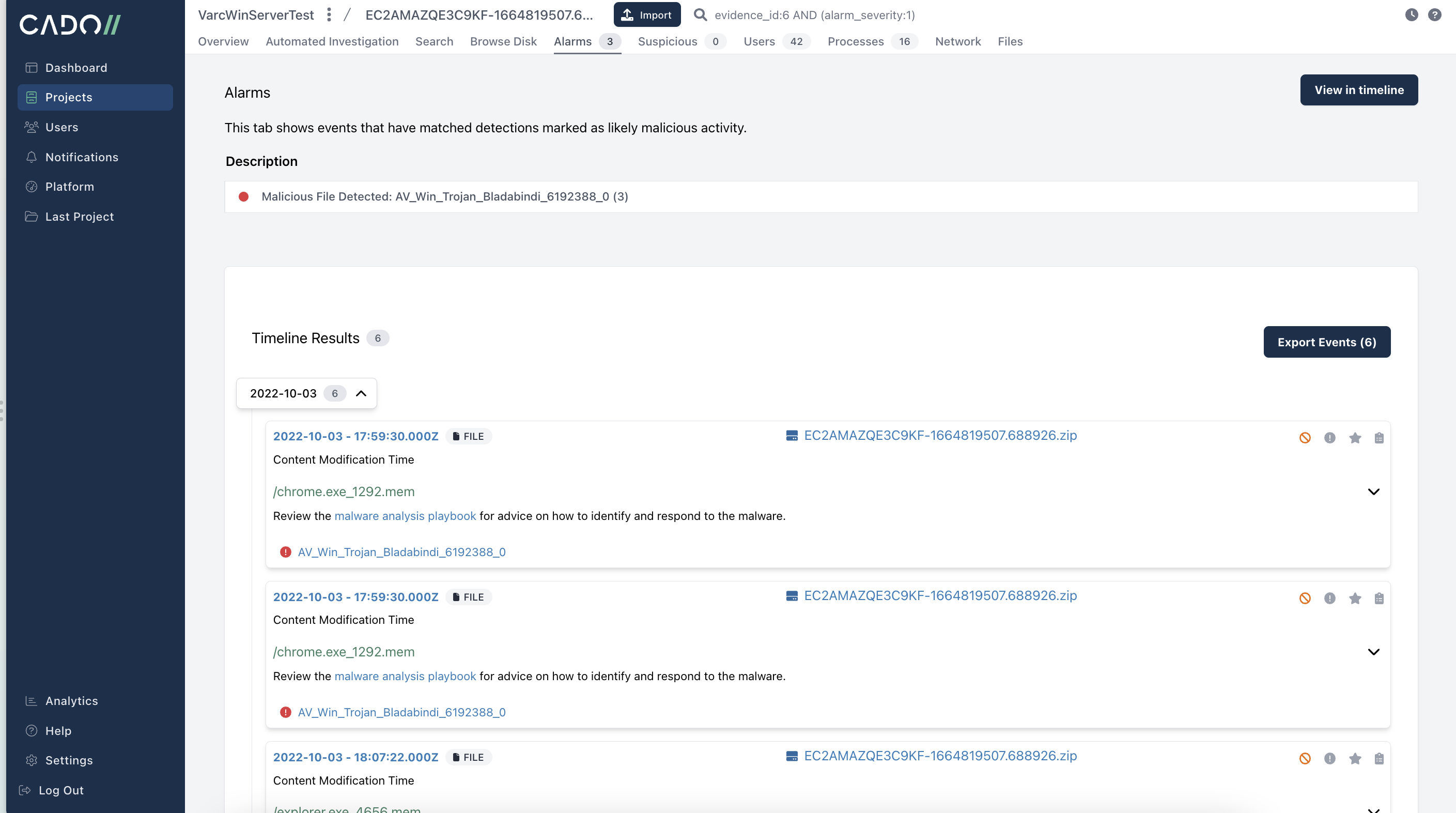
Cloud computing has influenced a true renaissance in how we manage and deliver applications and services; however, this digital transformation also poses new security challenges – especially when it comes to forensics and incident response. The cloud is complex. Cloud VMs, containers and functions can be extremely difficult to access, or worse, disappear in the blink of an eye. In this modern cyber world – where new blind spots provide attackers with a greater window of opportunity – it is essential that security teams have the proper visibility to investigate and respond to potential compromises.
Check out our latest white paper that covers five reasons why you need Cloud Investigation and Response Automation to ensure your organization is equipped to efficiently understand and respond to cloud threats.

