Last week, we hosted a webinar on cloud and Kubernetes memory forensics.
Many of today’s sophisticated hackers leverage techniques that run in memory only — such as fileless malware, rootkits and process hollowing — flying completely under the radar without the proper visibility.
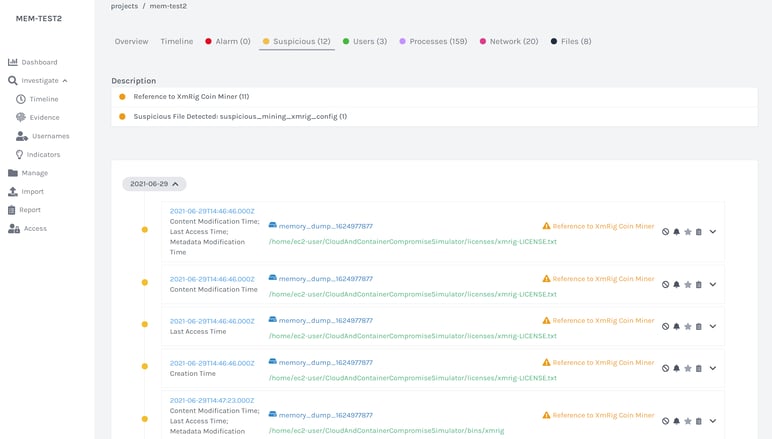
Conducting memory forensics of cloud and Kubernetes environments provides security teams with enhanced visibility and context to identify the root cause and determine scope and impact of compromises. Memory Forensics helps security teams:
- Gain visibility of run-time information (running processes, loaded libraries and drivers, command line history, open files, etc.)
- Detect rogue processes, fileless malware and code injection
- Add context into timeline activity such as when malicious activities began
- And more…
When it comes to conducting cloud and Kubernetes forensics, here are some of the top questions our listeners asked following the webinar (and our answers):
1. Kubernetes forensics - can it really be done?
Yes! While conducting forensics in Kubernetes and containerized environments can be tricky, it is possible. However, automation is key here, as you have to be quick. Due to the dynamic and ephemeral nature of containerized environments, you need to be able to capture incident data as soon as malicious activity is detected to ensure the data isn’t lost forever. This is best achieved by integrating your digital forensics solution with your SIEM/SOAR or EDR/XDR solution.
2. How difficult is it to preserve memory artifacts of cloud assets?
Cado's mission is to take the complexity out of cloud investigations. As part of this, the Cado Response platform completely automates the process of capturing and storing memory from AWS EC2 instances to ensure preserving memory artifacts isn't difficult.
3. What are the log sources you see as most useful for detecting and investigating threats in AWS in general?
AWS has numerous log sources which can help you detect and investigate threats. Some of these include: CloudTrail, CloudWatch, Guard Duty, AWS Load Balancers/VPC Flow Logs, S3 Access Logs
- CloudTrail logs retain account activity related to actions across your AWS infrastructure
- CloudWatch collects monitoring and operational data in the form of logs, metrics, and events so you can get a unified view of your resources, applications and services that run in AWS
- Guard Duty is AWS’ threat detection service that monitors for malicious activity across your account
- AWS Load Balancers/VPC Flow Logs contain NetFlow log data of network traffic in your VPC
- S3 Access Logs provide detailed records about requests that are made to a bucket
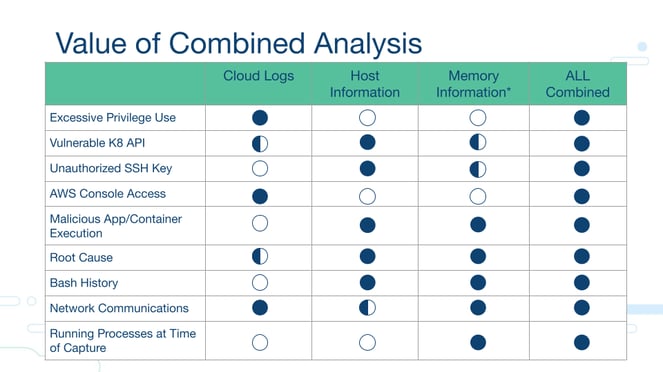
Simply put, the more data sources you can analyze in aggregate, the better your investigation will be. Adding cloud context to traditional host-based analysis is the only way to grasp the full extent of what happened. And, to make life easier on the analyst, we recommend pooling multiple data sources into a single pane of glass. Complete context is key to fully remediating an incident as well as satisfying legal and regulatory requirements.
4. How is cloud forensics technically different from the normal forensics we perform?
The major difference between cloud and physical forensics is the acquisition process. With cloud, you no longer have physical disks and the requirement to utilize a hardware writeblocker to preserve the integrity of the disk image. Further, by utilizing a cloud-native digital forensics platform, organizations can benefit from greater visibility, scale and speed:
- Visibility: As modern DFIR platforms are completely agentless, security teams can capture and investigate data across systems without worrying about production downtime. This is especially useful for investigating crown jewel designated systems.
- Scale: Moving data processing to the cloud enables security teams to normalize massive amounts of data captured across countless assets simultaneously, saving hours to days.
- Speed: By automating the most tedious parts of a forensics investigation, including data capture and processing, security analysts have more time to concentrate on what matters most: investigating and responding.
5. I live in a GDPR-sensitive part of the world, and I need to have full control of my data. How does Cado handle this?
The Cado Response platform and any data stored within the platform resides in your cloud environment and within a region you choose to ensure that your unique data privacy requirements are met.
To learn more about conducting cloud and kubernetes memory forensics, view the webinar recording or conduct your free Cado Response investigation today.