Last month James Campbell, Cado Security’s Co-Founder and CEO, and Al Carchrie, Digital Forensics Solutions Engineer, provided some useful insights into performing investigations in the cloud at the SANS DFIR summit.
As data has migrated to the cloud at exponential rates, we’ve also seen an uptick in the number of cloud-based attacks. This means security and DFIR experts are required to perform cloud and container investigations more frequently; but this often feels like an impossible task. While a thorough forensics investigation requires the analysis of both cloud and host data, the lack of automation coupled with the complexity of the cloud often has security teams struggling to get the context they need.
In this session, James and Al share a real-life case study involving AWS Kubernetes. Further, they explore the types of cloud data available and how these sources can augment traditional host forensics to enable security and DFIR experts to understand the true impact of cloud breaches.
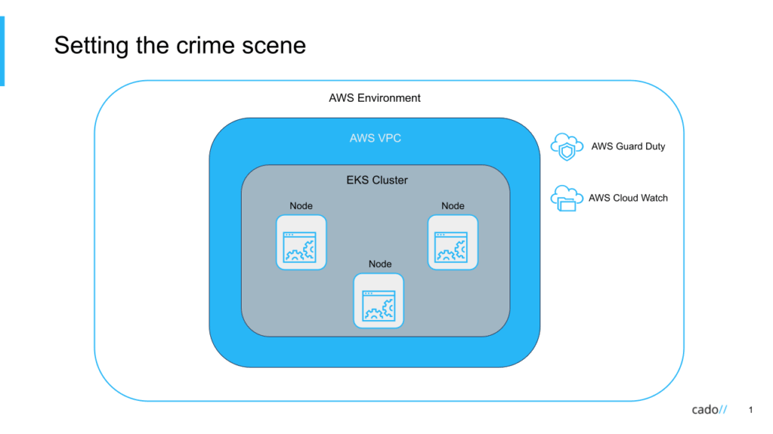
Don’t take our word for it, see for yourself. Conduct your own AWS Kubernetes investigation or simply gain a better understanding of the types of data sources that can be captured in AWS using the data gathered from this session.

