The question of an incident occurring is an 'if' not 'when' scenario. Thus, an organization's level of preparedness to investigate and respond to cloud threats becomes critical in managing risk effectively.
What Does it Really Mean to be Proactive?
A proactive approach to incident response means security teams continuously assess their readiness before an incident occurs. For example, security teams should test key steps in the IR process, such as their ability to access and gather critical evidence items across cloud resources, to proactively identify any issues that may prevent rapid investigation and response. This level of proactivity also allows security teams to continuously refine their incident response program and preemptively address any existing gaps without wasting crucial time during an incident. Even in scenarios where organizations engage third-party security services or incident response firms, it is very important that internal teams are prepared so that they can provide answers to crucial questions that these external vendors will have.
An Example: When it Pays to be Prepared
Let's dive into an example that sheds light on the value of preparedness. Targeted ransomware attacks, for example, typically:
- Begin with a spear phishing compromise;
- Followed by malware installation, often something like CobaltStrike;
- From there, attackers spread across as much of the network as possible before deploying the ransomware itself.
This process (before the deployment of ransomware itself) generally takes about two weeks. This is a window of opportunity for security teams. In the event the team is well prepared, a deeper dive investigation upon the detection of CobaltStrike would reveal that something much larger is going on here. Further, rapid response would significantly reduce the likelihood of a full-scale ransomware attack.
Preparedness enables security teams to kick off investigations without delay during an active attack, allowing them to answer critical questions:
- Has lateral movement occurred?
- Is there any evidence of data exfiltration?
- Are connections established to other systems?
- Are password dumping tools present?
- Have users stored plain text passwords on compromised systems?
Relying solely on automated alerts is not a sufficient solution. There is a need to go deeper to better understand the scope and the attackers intent. Critical data sources should be collected and analysts including disk images, memory, and cloud-provider logs across all affected resource. Without these key data sources, it can be impossible to identify the root cause of an incident.
How Cado Helps Organizations Implement IR Preparedness
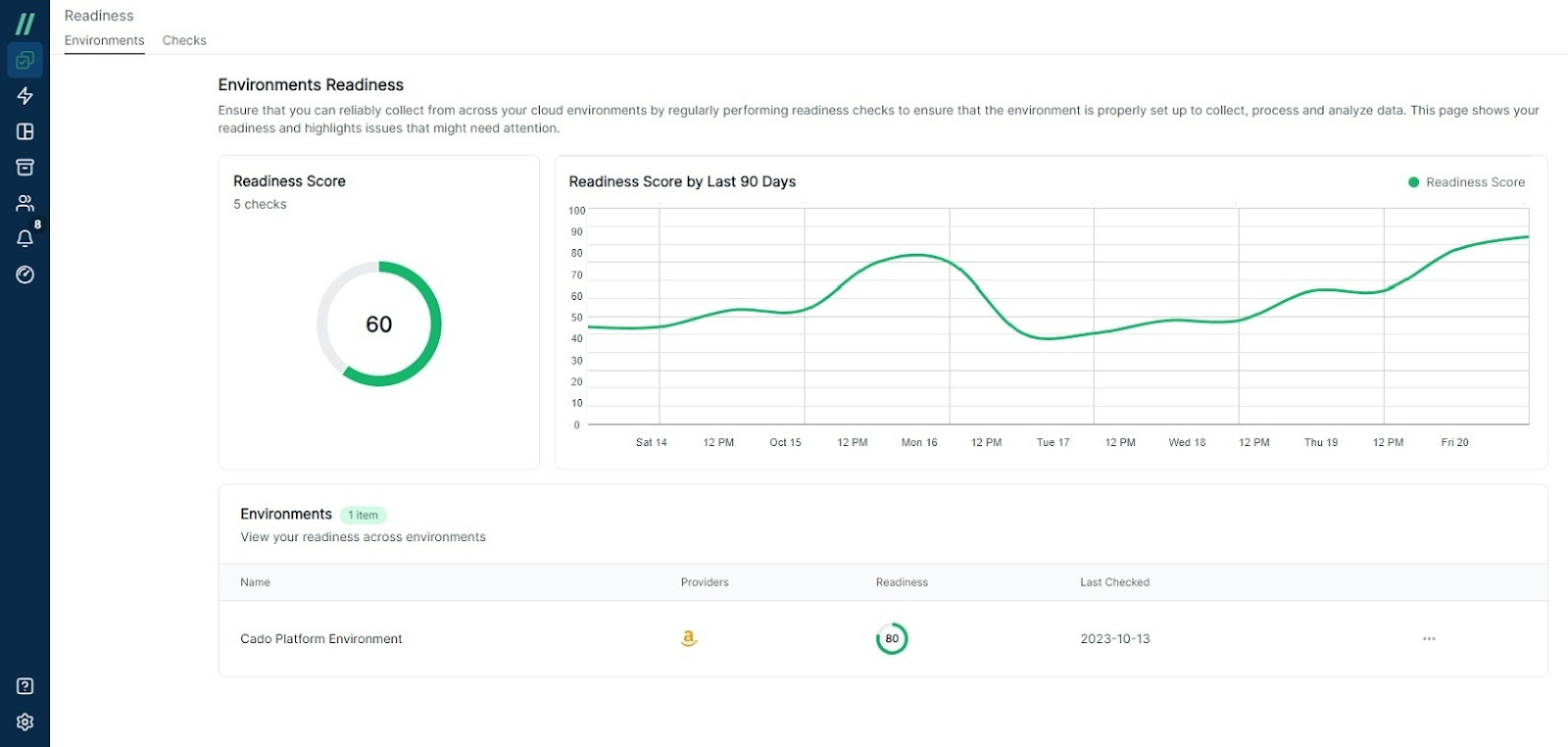
Cado’s Incident Readiness Dashboard
Cado Security recently introduced its Incident Readiness Dashboard to help organizations embrace a proactive approach to cloud incident response. Cado’s readiness checks provide valuable insights into steps that can be taken to optimize an organization’s level of preparedness to investigate and respond to cloud threats. Cado’s new Incident Readiness Dashboard, answers critical questions for security teams including:
- Do we have the ability to acquire evidence from critical sources across our cloud environments?
- Do we have the right permissions to acquire and respond appropriately?
- Do we have the ability to decrypt critical evidence?
- What is our organization’s readiness trend over time, has it improved?
Cado’s Incident Readiness Dashboard also delivers a readiness score and includes actionable recommendations to empower users to promptly close any existing gaps.
If you're interested in learning more, schedule a demo with our team to assess your level of preparedness to perform forensics and incident response in the cloud.

