Creating an incident response playbook for cybersecurity events is a vital step in preparing for and mitigating the effects of cyberattacks. Below, we run you through the process of developing a comprehensive incident response playbook, taking into account the guidelines and principles from various experts. The overall incident response process is likely to look similar in cloud environments such as AWS, Azure and GCP. However you will encounter some differences such as:
- Collecting evidence for forensic analysis can be more challenging in the cloud
- Attacks can move faster in the cloud, as attackers can move between multiple accounts and organizations if they have elevated permissions in IAM.
What is an Incident Response Playbook
An incident response playbook is a predefined set of actions tailored to address specific types of cybersecurity incidents, such as malware infections, DDoS attacks, or security policy violations. Its primary goal is to enable security teams to respond quickly and effectively to cyberattacks, optimizing the security operations center (SOC) processes and bringing about SOC maturity. Basically, it's important to know what to do before an incident hits.
Key Elements of an Incident Response Playbook
- Preparation: This phase includes incident prevention, vulnerability management, user awareness, and malware prevention. It involves defining alert field sets, visual representations, escalation scenarios, and communication tools for contacting stakeholders.
- Detection and Analysis: This involves collecting data from various sources and identifying incident indicators. The analysis phase includes documentation, triage, investigation, and notification, focusing on understanding the scope of the incident and appropriate response measures.
- Containment, Eradication, and Recovery: Containment aims to control the situation after an incident has occurred. Eradication involves cleaning up the traces of the attack, while recovery focuses on restoring normal business operations.
- Post-Incident Activity: This phase involves learning from the incident to improve future responses. It includes reviewing the response team's actions and identifying any gaps or areas for improvement.
A High-Level Incident Response Process
The NCSC provide a high level example process to guide a team through managing a security incident.
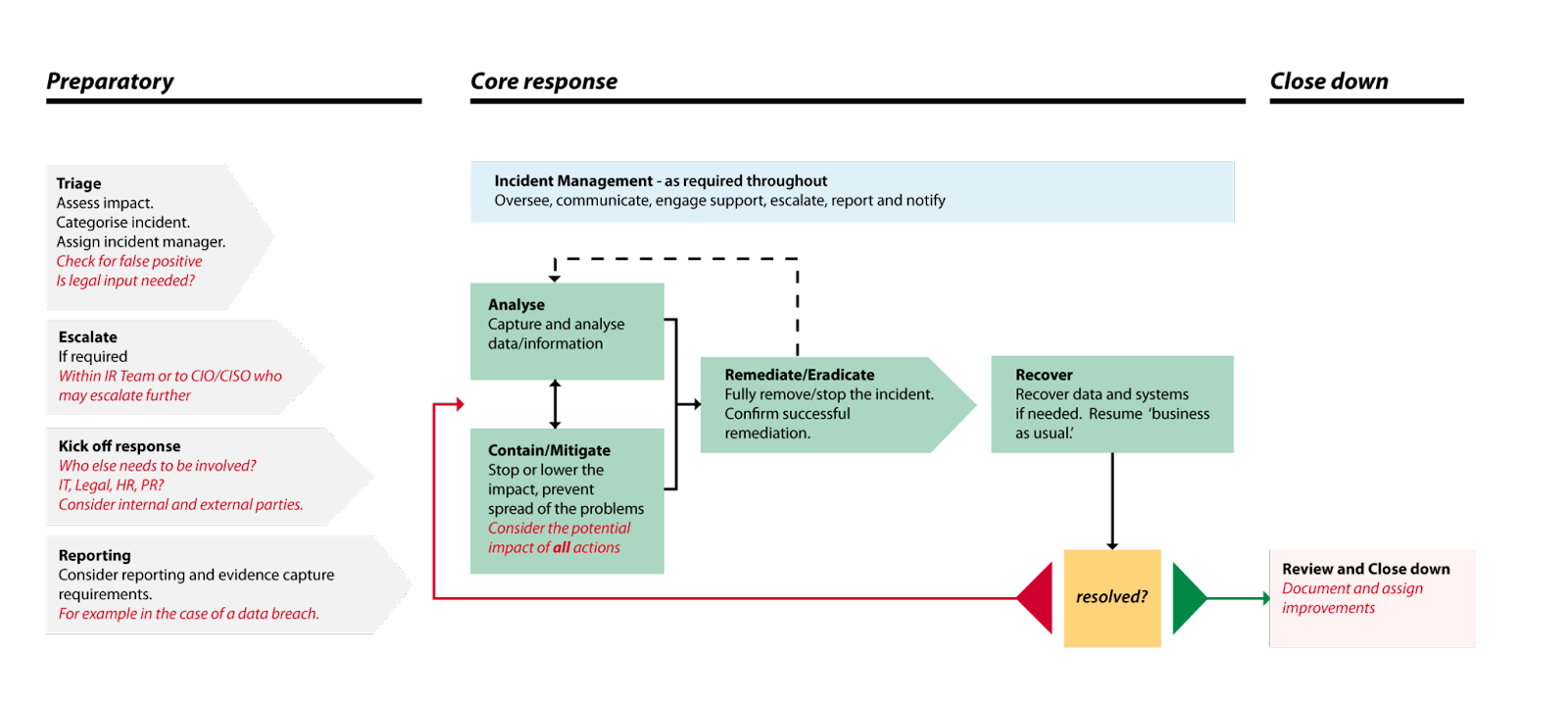
Before an incident:
- In the "Triage" phase, the team assesses the impact, categorizes the incident, assigns an incident manager, checks for false positives, and determines if legal input is needed.
- Next is the "Escalate" phase. It involves escalating within the Incident Response (IR) team or to the CIO/CISO, who may escalate further.
- The third step is "Kick off response", deciding who else needs to be involved, such as IT, legal, HR, or PR, and considering both internal and external parties.
- Following that is "Reporting", which includes considering reporting and evidence capture requirements, for example in the case of a data breach.
During an actual incident:
- It is necessary to oversee, communicate, engage support, escalate, report, and notify related parties.
- In the "Analyse" stage, the team captures and analyzes data/information.
- Then it moves to "Contain/Mitigate," with the goal to stop or lower the impact and prevent the spread of the incident.
- The final stage is "Remediate/Eradicate," focusing on fully remediating the incident and confirming successful remediation.
Aligning with NIST Guidelines
A NIST-compliant Cyber Security Incident Response Playbook is a structured document guiding IR teams through the response process. It helps maintain regulatory compliance, enables a coordinated response, and fosters a culture of cybersecurity awareness within the organization. The NIST Special Publication 800-61 Revision 2, also known as the Computer Security Incident Handling Guide provides a lot of direction on how to create effective playbooks. This document outlines the best practices and guidelines for incident response.
To create a NIST-compliant playbook:
- Understand the NIST Incident Response Framework: Familiarize yourself with the key phases of incident response outlined by NIST, including detection, analysis, containment, eradication, and recovery.
- Define Roles and Responsibilities: Clearly establish the roles and responsibilities of your incident response team, including internal handlers, external responders, analysts, and key decision-makers.
- Develop Detailed Procedures: Create step-by-step actions for each phase of an incident, from detection to recovery.
- Conduct a Risk Assessment: Identify potential threats and vulnerabilities specific to your organization and categorize incidents based on their severity.
- Incorporate Third-Parties and Reporting: Establish relationships with external entities and define reporting mechanisms for timely and accurate information dissemination.
- Test, Train, and Refine: Regularly test your playbooks through simulated exercises, conduct training sessions, and refine your playbooks based on these experiences.
NIST SP800-61 Rev. 2 which includes the following phases in incident response:
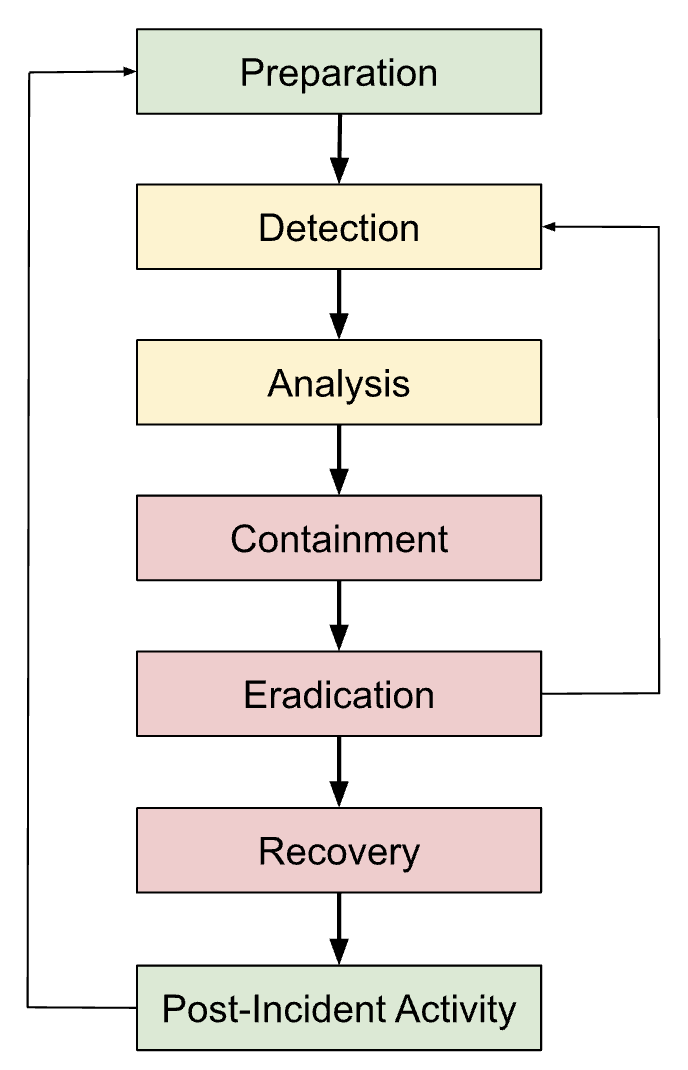
For more on how Cado Security can help you align to the NIST guidelines, see our previous two blogs:
- Decoding the NIST Cloud Computing Forensics Reference Architecture
- Revisiting NIST Forensics Guidance in a Cloud Age
Continual Evaluation and Updates
Regularly review and update your incident response playbooks to address emerging threats and evolving organizational needs. This proactive approach ensures that your organization remains equipped to effectively detect, respond to, and recover from cybersecurity incidents, minimizing their impact on business operations.
How Cado can Help
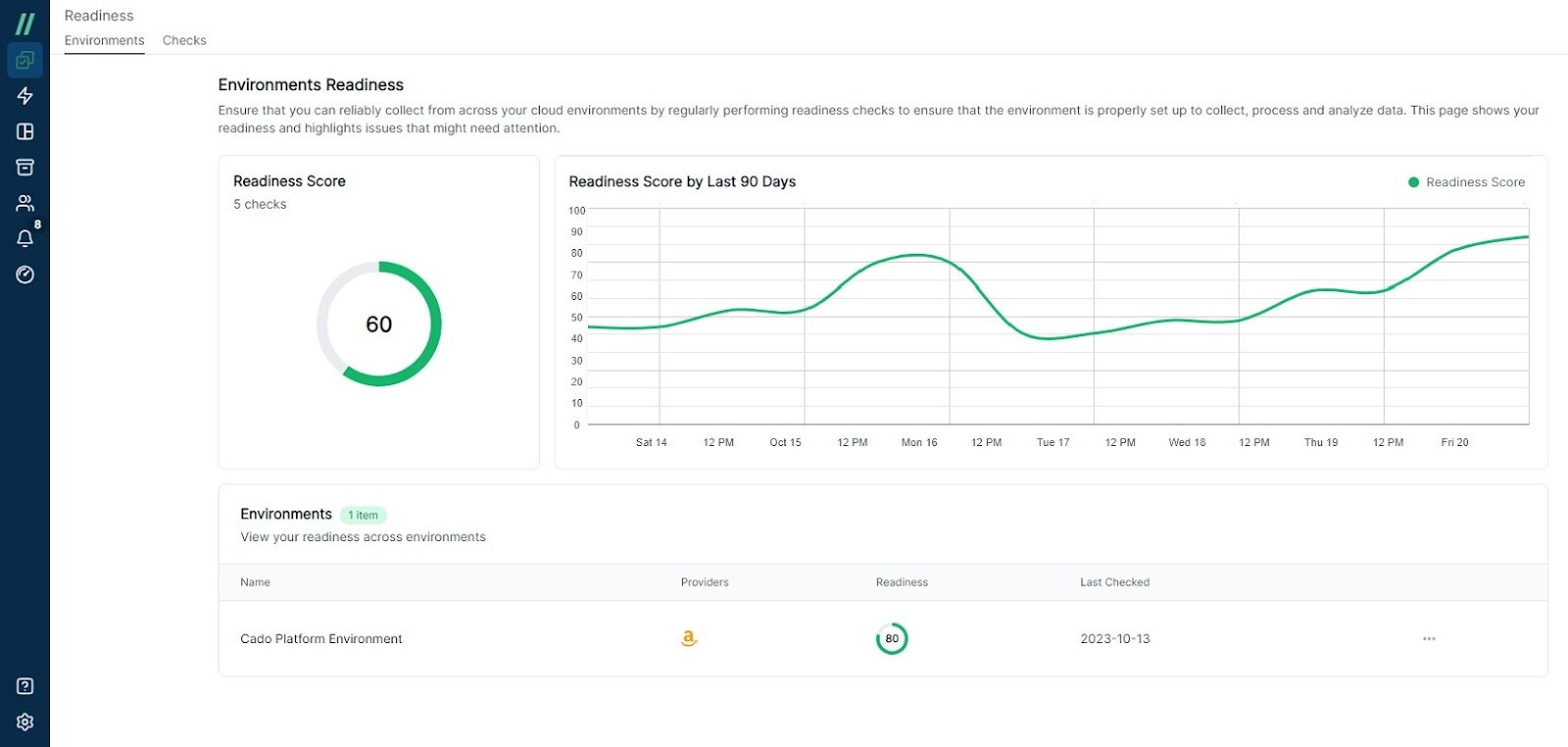
Cado Security offers the Cado Platform, a modern, scalable solution for cloud forensics and incident response. It automates forensic-level data capture and processing across various environments, providing security teams with the ability to investigate and respond to threats effectively. This platform ensures compliance with legal and regulatory standards and empowers teams to respond at cloud speed. We recently launched a new “Cloud Readiness Dashboard” to help organizations prepare for attacks in the cloud.
Developing an incident response playbook is a multifaceted process that requires a deep understanding of your organization's specific needs, the threats it faces, and the best practices in incident response. By leveraging tools like the Cado Platform and adhering to NIST guidelines, you can create a robust playbook that enhances your organization's cybersecurity posture and readiness for any cyber threats.
Interested in learning more about Cado’s Incident Readiness features? Request a demo today.
More from the blog
View All Posts

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

