AWS Fargate is a serverless service that provides the option of fully managed and abstracted infrastructure for containerized applications managed using AWS ECS. Since AWS Fargate is a managed service, getting the data you need to investigate a potential compromise becomes more complex.
While the visibility provided by built-in CSP tools such as AWS CloudWatch and CloudTrail is important, these data sources alone are not sufficient for a detailed investigation in container environments. In order to gain more visibility into ECS containers, third-party incident and threat intelligence capabilities prove vital to discover, monitor and secure container assets.
Collecting the Right Data
When it comes to investigating potential threats in container environments, assessing whether you have the ability to collect the right data is step one.
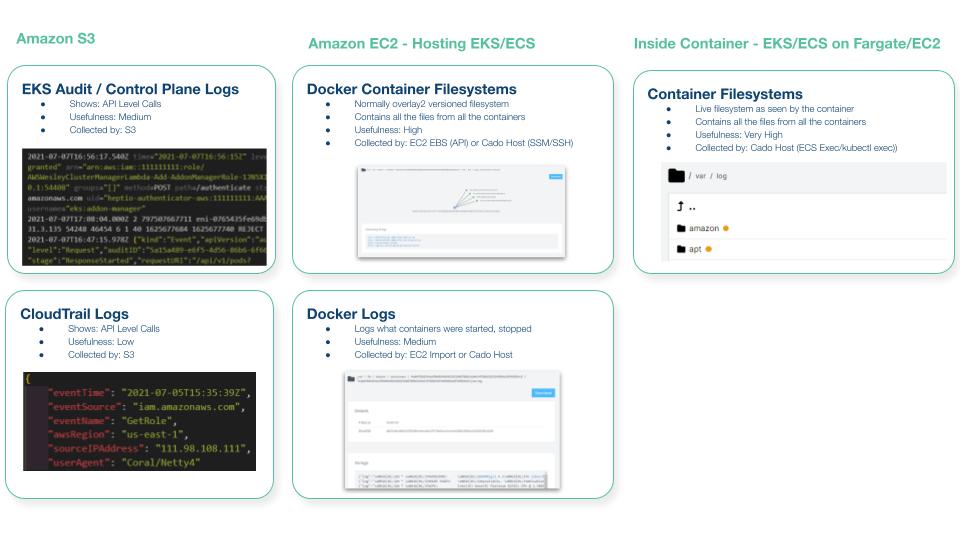
Useful data sources to include as part of a container investigation are:
- System logs and files from within the container
- Container running processes
- Container active network connections
- Container host system
- Container runtime logs (if accessible)
- Container host memory (if accessible)
- AWS VPC flow logs for the VPC the container is attached to
- Logs from container repositories
If data collection wasn't baked into the container declaration before the need to investigate arose, you need to rely on data you can actively interrogate out of the container.
If you’re using ECS on Fargate, taking an image of the running container or the container host isn’t an option as the underlying AWS infrastructure is shared with no access to the end customers. In this case, the /proc directory gives us a snapshot of the volatile state of the container, much like a memory dump. Using this ‘snapshot’, we can build a basic picture of what is going on in the container at that time, such as running processes, active network connections, open files etc. This data provides a foundation of what you need to correlate with other data sources such as firewall logs, network subnet flows etc during an investigation to understand the actions carried out by an attacker.
Cado Security Resources
To help security and incident response professionals investigate and respond in AWS ECS container environments, we've published a number of materials:
- Playbook: Ultimate Guide to Incident Response in AWS
- AWS ECS: Fully Managed but Frustrating to Investigate
- Top 9 Best Practices for AWS ECS Security
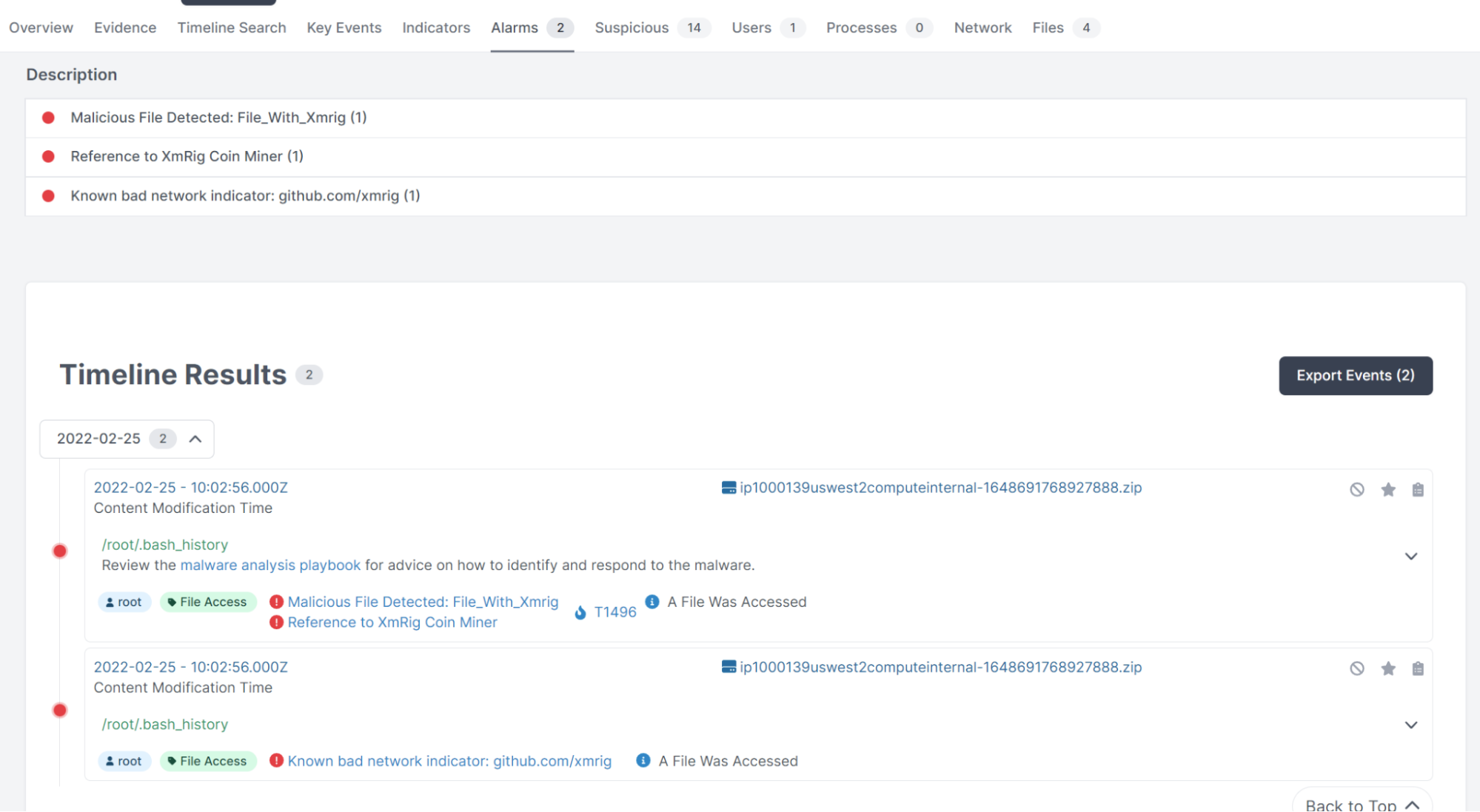
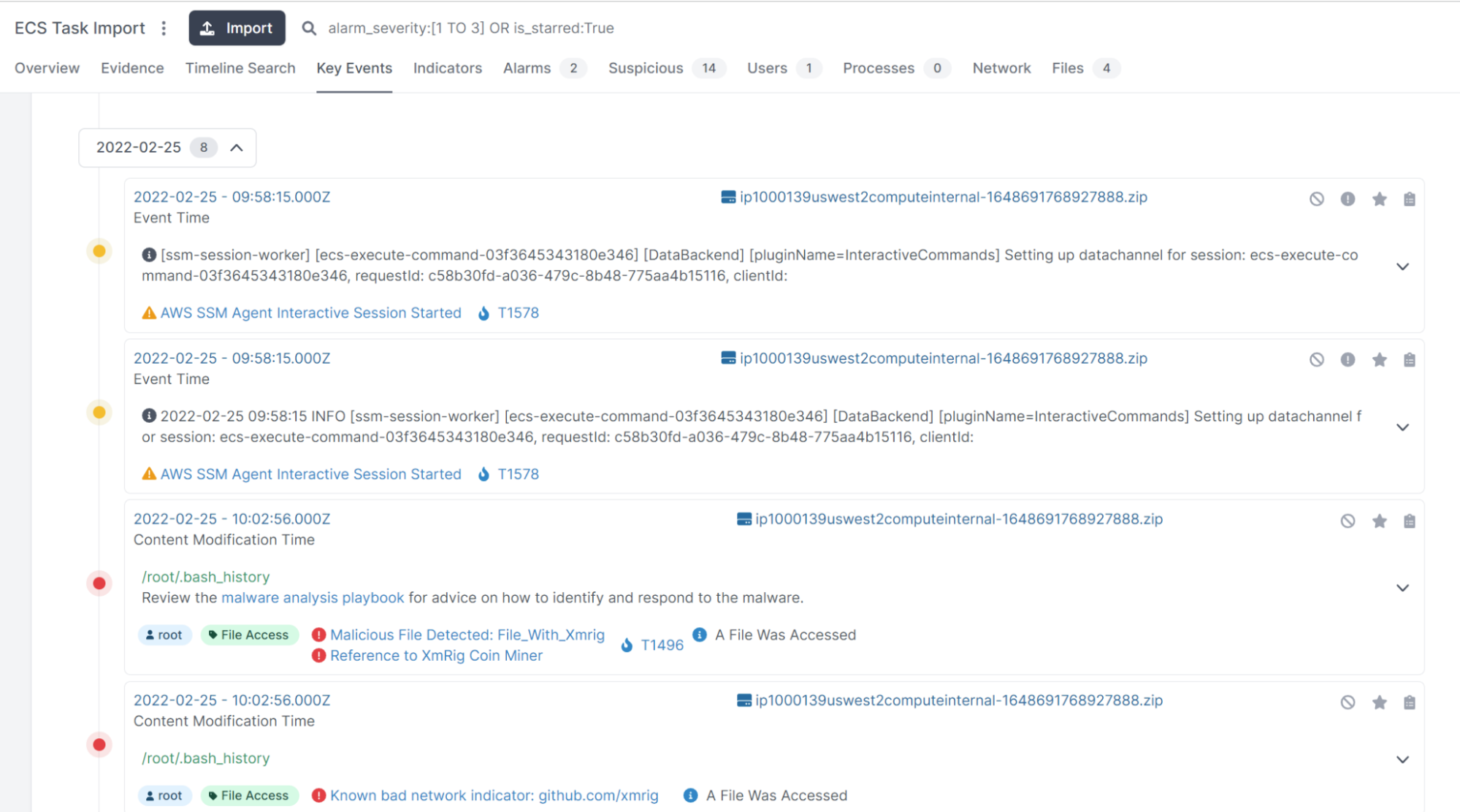
- Cado in Action: Investigating ECS Fargate
The ephemeral nature of cloud environments can make investigating and responding to potential threats nearly impossible. Using the power of automation, The Cado platform simplifies data capture, processing and analysis in cloud, container and serverless environments to expedite incident response.
Check out the 14-day free trial of the Cado platform to perform your own investigation today.

