Below we have analyzed an on-going campaign to steal AWS accounts through phishing. We’ve identified linked attacks, and outlined what attackers are doing with the stolen accounts. Lastly, we provide some recommendations on how to secure your AWS accounts against these kinds of attacks.
The attack we investigated started with an e-mail sent from a rented server, using an email address from an Irish web-hosting company. The email impersonates AWS, and encourages the recipient to click through to view an open support case:

The links sends the user to https://howitfix[.]com/app/aws/ – which is an AWS phishing page hosted on a compromised server:
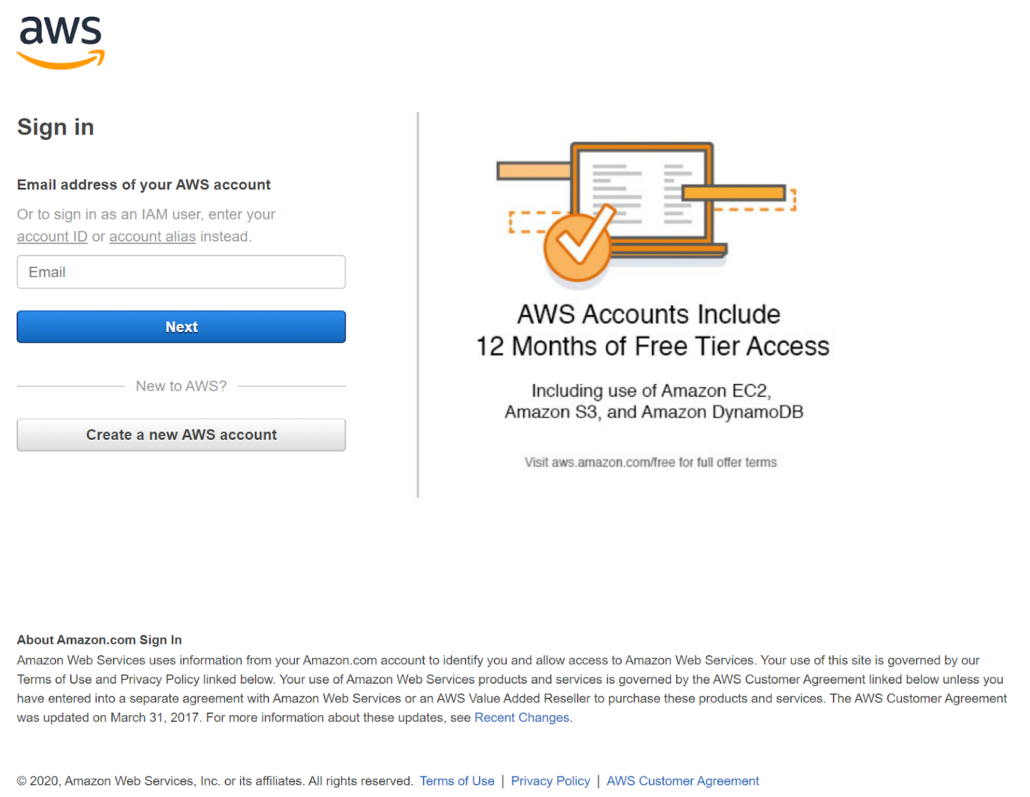
We created a limited AWS account – and entered the account username and incorrect password into the phishing page.
About an hour later, we saw a failed attempt to login to the account from a mobile user on a Moroccan IP address, shown below in CloudTrail:
<code lang="bash" class="language-bash">{ “eventVersion“: “1.05”, “userIdentity“: { “type“: “Root”, “principalId“: “809xxx”, “arn“: “arn:aws:iam::809xxx:root”, “accountId“: “809xxx”, “accessKeyId“: “” }, “eventTime“: “2020-06-07T04:25:51Z”, “eventSource“: “signin.amazonaws.com”, “eventName“: “ConsoleLogin”, “awsRegion“: “us-east-1”, “sourceIPAddress“: “105.155.37.247”, “userAgent“: “Mozilla/5.0 (Linux; Android 8.0.0; SAMSUNG SM-G930F) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/11.2 Chrome/75.0.3770.143 Mobile Safari/537.36”, “errorMessage“: “Failed authentication”, “requestParameters“: null, “responseElements“: { “ConsoleLogin“: “Failure” }, “additionalEventData“: { “LoginTo“: “https://console.aws.amazon.com/console/home?nc2=h_mo&state=hashArgs%23&isauthcode=true”, “MobileVersion“: “No”, “MFAUsed“: “No” }, “eventID“: “164ed813-9818-4ad0-9d09-xxx”, “eventType“: “AwsConsoleSignIn”, “recipientAccountId“: “809xxx”}</code>
Followed by an attempt to reset the account password, shown below in CloudTrail:
<code lang="bash" class="language-bash">{ “eventVersion“: “1.05”, “userIdentity“: { “type“: “Root”, “principalId“: “809xxx”, “arn“: “arn:aws:iam::809xxx:root”, “accountId“: “809xxx”, “accessKeyId“: “” }, “eventTime“: “2020-06-07T04:26:12Z”, “eventSource“: “signin.amazonaws.com”, “eventName“: “PasswordRecoveryRequested”, “awsRegion“: “us-east-1”, “sourceIPAddress“: “105.155.37.247”, “userAgent“: “Mozilla/5.0 (Linux; Android 8.0.0; SAMSUNG SM-G930F) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/11.2 Chrome/75.0.3770.143 Mobile Safari/537.36”, “requestParameters“: null, “responseElements“: { “PasswordRecoveryRequested“: “Success” }, “eventID“: “59b12bc4-f826-4c2d-9879-xxx”, “eventType“: “AwsConsoleSignIn”, “recipientAccountId“: “809xxx”}</code>
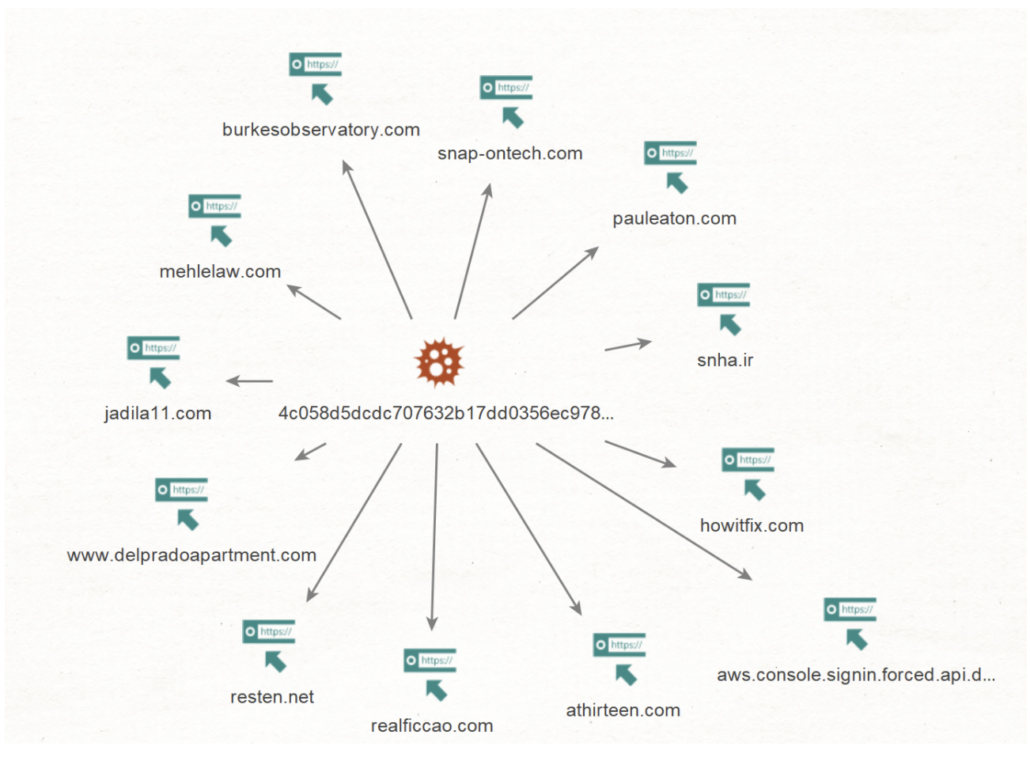
This is not an isolated attack. We discovered a network of AWS Phishing sites using exactly the same AWS phishing template, served from compromised domains:
The submissions of URLs with this hash to VirusTotal provides a rough timeline that this phishing template has been in use:
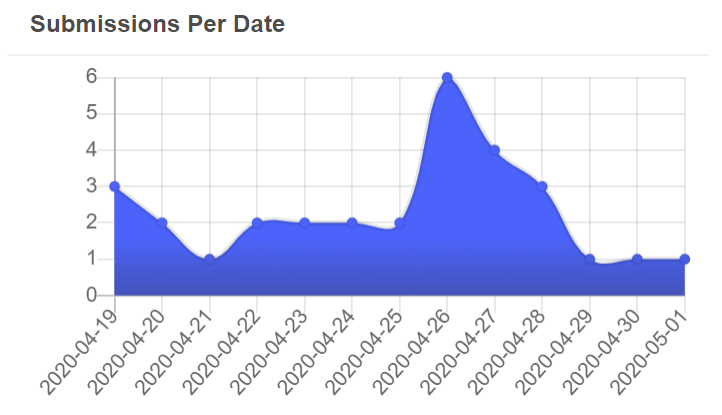
This seems like a widespread, opportunistic, campaign to compromise as many AWS accounts as possible. We’ve also seen linked activity recently reported by another security firm.
Cashing Out
Many attackers trade AWS accounts on forums where stolen accounts are exchanged. AWS Accounts limited to the free tier go for as little a $4. Accounts with larger limits can go for significantly more.
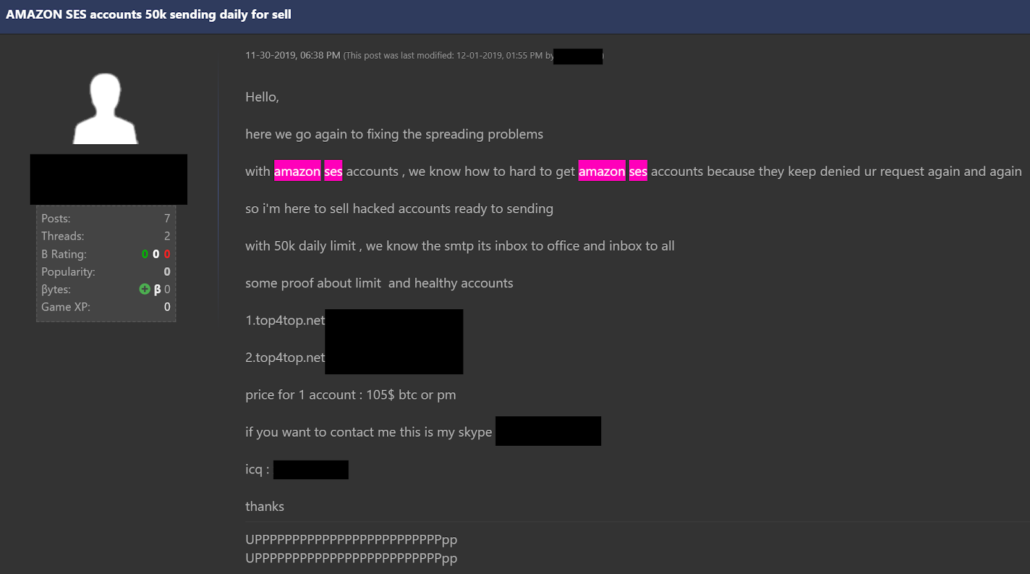
AWS API keys stolen from users who accidentally commit them to public code repositories are normally used to mine crypto-currencies. However, the market for AWS accounts stolen by phishing is mainly for people looking for accounts to use Amazon Simple Email Service (SES).
A common usage is to use these stolen accounts to to send e-mails delivering malware:
Detection and Prevention
There are a number of steps you can take to protect yourself from these attacks:
- The number one step to prevent this phishing is to add mandatory two factor authentication (MFA) to your account.
- Whilst we haven’t seen this attacker phish for two factor authentication credentials, we have seen it in attacks targeting other providers. A security key may provide an additional layer of security.
- Avoid using the Root AWS account where possible, and create accounts with limited credentials.
- Enable CloudTrail logging, and look for suspicious password resets and logins.
- As always, be suspicious of any email asking you to login to your AWS account and check any links you click from an email directly.
- You may prefer to login to AWS by bookmarking the login page.
- You can report suspected phishing messages to AWS here.
Malicious Phishing Page File-Hash
4c058d5dcdc707632b17dd0356ec978d8b32df58daf5c64bd2d43e803323cf1b
Malicious Phishing URLs
These sites are likely compromised and not malicious in themselves. We have reported these sites to be cleaned up.
- http://athirteen[.]com/console
- http://aws.console.signin.forced.api.delpradoapartment[.]com/management/
- http://burkesobservatory[.]com/api/ses/new/
- http://howitfix[.]com/app/aws/new/
- http://jadila11[.]com/api/application/new/index.php
- http://mehlelaw[.]com/security/app/news/
- http://pauleaton[.]com/api/new/index.php
- http://realficcao[.]com/application/api/new/index.php
- http://resten[.]net/api/sign/new/index.php
- http://snap-ontech[.]com/news/update/administration/new/index.php
- http://snha[.]ir/fzNS0k
- http://www.delpradoapartment[.]com/api/new/index.php

